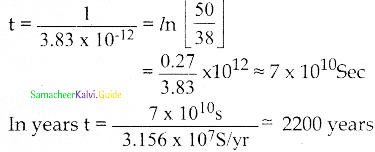Tamilnadu State Board New Syllabus Samacheer Kalvi 12th Physics Guide Pdf Chapter 7 Dual Nature of Radiation and Matter Text Book Back Questions and Answers, Notes.
Tamilnadu Samacheer Kalvi 12th Physics Solutions Chapter 8 Atomic and Nuclear Physics
12th Physics Guide Atomic and Nuclear Physics Text Book Back Questions and Answers
Part – I:
Text Book Evaluation:
I. Multiple Choice Questions:
Question 1.
Suppose an alpha particle accelerated by a potential of V volt is allowed to collide with a nucleus whose atomic number is Z, then the distance of closest approach of alpha particle to the nucleus is
a) 14.4 \(\frac{Z}{V}\) Å
b) 14.4 \(\frac{\mathrm{V}}{\mathrm{Z}}\) Å
c) 1.44 \(\frac{Z}{V}\) Å
d) 1.44 \(\frac{\mathrm{V}}{\mathrm{Z}}\) Å
Answer:
c) 1.44 \(\frac{Z}{V}\) Å
Solution:
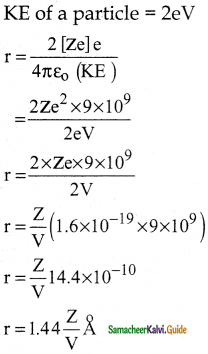
Question 2.
In a hydrogen atom, the electron revolving in the fourth orbit, has angular momentum equal to
a) h
b) \(\frac{\mathrm{h}}{\pi}\)
c) \(\frac{4 h}{\pi}\)
d) \(\frac{2 \mathrm{~h}}{\pi}\)
Answer:
d) \(\frac{2 \mathrm{~h}}{\pi}\)
Solution:
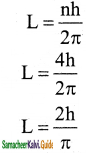
Question 3.
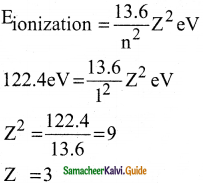
Atomic number of H – like atom with ionization potential 122.4 V for n = 1 is
a) 1
b) 2
c) 3
d) 4
Answer:
c) 3
Solution:
Question 4.
The ratio between the first three orbits of hydrogen atom is
a) 1 : 2 : 3
b) 2 : 4 : 6
c) 1 : 4 : 9
d) 1 : 3 : 5
Answer:
c) 1 : 4 : 9
Solution:
rn α n2
r1 : r2 : r3 = 1 : 4 : 9
Question 5.
The charge of cathode rays is
a) positive
b) negative
c) neutral
d) not defined
Answer:
b) negative
(They are negatively charged particles)
![]()
Question 6.
In J.J. Thomson e/m experiment, a beam of the electron is replaced by that of muons (particle with same charge as that of electrons but mass 208 times that of electrons). No deflection condition is achieved only if
(a) B is increased by 208 times
(b) B is decreased by 208 times
(c) B is increased by 14.4 times
(d) B is decreased by 14.4 times
Answer:
(c) B is increased by 14.4 times
Hint:
In the condition of no deflection \(\frac { e }{ m }\) = \(\frac {{ E }^{2}}{{ 2vB }^{2}}\)
If m is increased by 208 times then B should be increased \(\sqrt { 208 } \) = 14.4 time
Question 7.
The ratio of the wavelengths for the transition from n = 2 to n = 1 in Li++, He+ and H is
a) 1 : 2 : 3
b) 1 : 4 : 9
c) 3 : 2 : 1
d) 4 : 9 : 36
Answer:
d) 4 : 9 : 36
Solution:
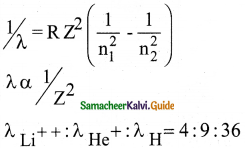
Question 8.
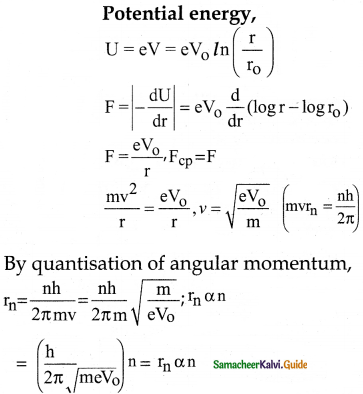
The electric potential between a proton and an electron is given by V = V0 ln \(\left(\frac{\mathbf{r}}{\mathbf{r}_{0}}\right)\) where r0 is a constant. Assume that Bohr atom model is applicable to potential, then variation of radius nth orbit rn with the principal quantum number n is
a) rn α \(\frac{1}{\mathrm{n}}\)
b) rn α n
c) rn α \(\frac{1}{n^{2}}\)
d) rn α n2
Answer:
b) rn α n
Solution:
Question 9.
If the nuclear radius of 27 Al is 3.6 fermi, the approximate unclear radius of64 Cu is
(a) 2.4
(b) 1.2
(c) 4.8
(d) 3.6
Answer:
(c) 4.8
Hint:
\(\frac {{ R }_{Al}}{{ R }_{Cu}}\) = \(\frac{(27)^{1 / 3}}{(64)^{1 / 3}}\) = \(\frac { 3 }{ 4}\)
Rcu = \(\frac { 4 }{ 3}\) RAl = \(\frac { 4 }{ 3}\) x 3.6 fermi
Rcu = 4.8 fermi
Question 10.
The nucleus is approximately spherical in shape. Then the surface area of the nucleus having mass number A varies as
a) A2/3
b) A4/3
c) A1/3
d) A5/3
Answer:
a) A2/3
Solution:
Surface area = 4πR²
Surface area α R²
R α A1/3
Surface area α (A1/3)2
Surface area α A2/3
![]()
Question 11.
The mass of a \({ }_{3}^{7} \mathbf{L i}\) nucleus is 0.042 u less than the sum of the masses of all its nucleons. The binding energy per nucleon of \({ }_{3}^{7} \mathbf{L i}\) nucleus is nearly
a) 46 MeV
b) 5.6 MeV
c) 3.9 MeV
d) 23 MeV
Answer:
b) 5.6 MeV
Solution:
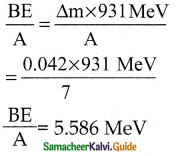
Question 12.
Mp denotes the mass of the proton and Mn denotes the mass of a neutron. A given nucleus of binding energy B, contains Z protons and N neutrons. The mass M (N, Z) of the nucleus is given by(where c is the speed of light)
(a) M (N, Z) = NMn + ZMp – Bc2
(b) M (N, Z) = NMn + ZMp + Bc2
(c) M (N, Z) = NMn + ZMp – B / c2
(d) M (N, Z) = NMn + ZMp + B / c2
Answer:
(c) M (N, Z) = NMn + ZMp – B / c2
Hint:
Binding energy, B = [ZMp + NMn – M (N, Z)] C2
M(N,Z) = ZMp + NMn – \(\frac { B }{{ C }^{ 2 }}\)
Question 13.
A radioactive nucleus (initial mass number A and atomic number Z) emits 2α and 2 positrons. The ratio of number of neutrons to that of proton in the final nucleus will be
a) \(\frac{A-Z-4}{Z-2}\)
b) \(\frac{A-Z-2}{Z-6}\)
c) \(\frac{A-Z-4}{Z-6}\)
d) \(\frac{A-Z-12}{Z-4}\)
Answer:
b) \(\frac{A-Z-2}{Z-6}\)
Question 14.
The half-life period of radioactive element A is same as the mean lifetime of another radioactive element B. Initially both have the same number of atoms. Then.
a) A and B have the same decay rate initially
b) A and B decay at the same rate always
c) B will decay at faster rate than A
d) A will decay at faster rate than B.
Answer:
c) B will decay at faster rate than A
Solution:
(t1/2)A = (tmean)B
\(\frac{0.693}{\lambda_{\mathrm{A}}}\) = \(\frac{1}{\lambda_{\mathrm{B}}}\)
λA = 0.693λB
λA < λB
rate decay = λN
Intially no. of atoms (N) of both are equal but since λB > λA, B will decay at a faster
rate than A.
Question 15.
A system consists of N0 nucleus at t = 0. The number of nuclei remaining after half of a half – life (that is, at time t = \(\frac{1}{2}\)T1/2)
a) \(\frac{\mathrm{N}_{0}}{2}\)
b) \(\frac{N_{0}}{\sqrt{2}}\)
c) \(\frac{\mathrm{N}_{0}}{4}\)
d) \(\frac{\mathrm{N}_{0}}{8}\)
Answer:
(b) \(\frac{N_{0}}{\sqrt{2}}\)) N0
Solution:
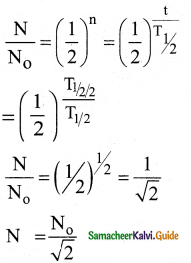
![]()
II. Short answer questions:
Question 1.
What are cathode rays?
Answer:
A cathode ray is a stream of electrons that are seen in vaccum tubes. It is called a “cathode ray” because the electrons are being emitted from the negative charged element in the vaccum tube called the cathode.
Question 2.
Write the properties of cathode rays.
Answer:
Properties of cathode rays:
- Cathode rays possess energy and momentum and travel in a straight line with high speed of the order of 107 ms-1. It can be deflected by the application of electric and magnetic fields. The direction of deflection indicates that they are negatively charged particles.
- When the cathode rays are allowed to fall of matter, they produce heat. They affect the photographic plates and also produce fluorescence when they fall on certain crystals and minerals.
- When the cathode rays fall on a material of high atomic weight, x-rays are produced.
- Cathode rays ionize the gas through which they pass.
- The speed of rys is upto \(\left(\frac{1}{10}\right)^{\text {th }}\) of the speed of light.
Question 3.
Give the results of Rutherford alpha scattering experiment.
Answer:
- Most of the alpha particles are un¬deflected through the gold foil and went straight.
- Some of the alpha particles are deflected through a small angle.
- A few alpha particles (one in thousand) are deflected through an angle more than 90°
Question 4.
Write down the postulates of Bohr atom model.
Answer:
1. The electron in an atom moves around nucleus in circular orbits under the influence of Coulomb electrostatic force of attraction. This Coulomb force gives necessary centripetal force for the electron to undergo circular motion.
2. Electrons in an atom revolve around the nucleus only in certain discrete orbits called stationary orbits where it does not radiate electromagnetic energy. Only those discrete orbits allowed are stable orbits.
3. The angular momentum of the electrons in these stationary orbits are quantized that is, it can be written as integer or integral multiple of \(\frac{\mathrm{h}}{2 \mathrm{~h}}\) called as reduced Planck’s constant – that is, h (read it as h-bar) and the integer n is called as principal quantum number of the orbit.
l = nh;
L = \(\frac{\mathrm{nh}}{2 \pi}\);
mvr = \(\frac{\mathrm{nh}}{2 \pi}\) where h = \(\frac{\mathrm{h}}{2 \pi}\)
This condition is known as angular momentum quantization condition.
4. An electron can jump from one orbit to another orbit by absorbing or emitting a photon whose energy is equal to the difference in energy (∆E) between the two orbital levels.
energy quantization condition
∆E = Efinal – Einitial = hν = \(\frac{\mathrm{hc}}{\lambda}\)
λ – Wavelength or radiation
C – Speed of light
ν – Frequency of the radiation
![]()
Question 5.
What is meant by excitation energy?
Answer:
Excitation energy and excitation potential:
The energy required to excite an electron from lower energy state to any higher energy state is known as excitation energy.
Question 6.
Define the ionization ionization potential.
Answer:
The minimum energy required to remove an electron from an atom in the ground state is known as binding energy or ionization energy.
Eionization = E∞ – En
= 0 – (-\(\frac{13.6}{\mathrm{n}^{2}}\) Z2eV)
= \(\frac{13.6}{\mathrm{n}^{2}}\) Z2eV
Ionization potential is defined as ionization energy per unit charge.
Vionization = \(\frac{1}{\mathrm{e}}\) Eionization = \(\frac{13.6}{\mathrm{n}^{2}}\) Z2V
Question 7.
Write down the drawbacks of Bohr atom model.
Answer:
Limitations of Bohr atom model:
The following are the drawbacks of Bohr atom model:
- Bohr atom model is valid only for hydrogen atom or hydrogen like-atoms but not for complex atoms.
- When the spectral lines are closely examined, individual lines of hydrogen spectrum is accompanied by a number of faint lines. These are often called fine structure. This is not explained by Bohr atom model.
- Bohr atom model fails to explain the intensity variations in the spectral lines.
- The distribution of electrons in atoms is not completely explained by Bohr atom model.
Question 8.
What is distance of closest approach?
Answer:
The minimum distance between the centre of the nucleus and the alpha particle just before it gets reflected back through 180° is defined as the distance of closest approach r0 (also known as contact distance).
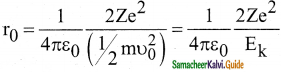
Question 9.
Define impact parameter.
Answer:
The impact parameter is defined as the perpendicular distance between the centre of the gold nucleus and the direction of velocity vector of alpha particle when it is at a large distance.
Question 10.
Write a general notation of the nucleus of element X. What each term denotes?
Answer:
General notation of nucleus of element X.
ZaX
where x is the chemical symbol of the element
A is the mass number and Z is the atomic number.
For example \(7^{\mathrm{N}^{15}}\)
Z = 7, N = (A – Z) = (15 – 7) = 8
![]()
Question 11.
What is isotope? Give an example.
Answer:
Isotopes are atoms of the same element having same atomic number Z, but different mass number A. For example, hydrogen has three isotopes and they are represented as \({ }_{1}^{1} \mathrm{H}\) {H (hydrogen), \({ }_{1}^{2} \mathrm{H}\) (deuterium), and \({ }_{1}^{3} \mathrm{H}\) (tritium). Note that all the three nuclei have one proton and, hydrogen has no neutron, deuterium has 1 neutron and tritium has 2 neutrons.
Question 12.
What is isotone? Give an example.
Answer:
Isotones are the atoms of different elements having same number of neutrons. \(_{ 5 }^{ 12 }B\) and \(_{ 6 }^{ 13 }B\) are examples of isotones which 7 neutrons.
Question 13.
What is isobar? Give an example.
Answer:
Isobars are the atoms of different elements having the same mass number A, but different atomic number Z.
For example \({ }_{16}^{40} \mathrm{~S}, \stackrel{40}{17} \mathrm{Cl}, \stackrel{40}{18} \mathrm{Ar}, \underset{19}{40} \mathrm{~K}\) and \({ }_{20}^{40} \mathrm{Ca}\) are isobars having same mass number 40 and different atomic number. In other words, isobars are the atoms of different chemical element which has same number of nucleon.
Question 14.
Define atomic mass unit u.
Answer:
One atomic mass unit (u) is defined as the 1/12th of the mass of the isotope of carbon \(_{ 6 }^{ 12 }C\).
Question 15.
Show that nuclear density is almost constant for nuclei with Z > 10.
Answer:
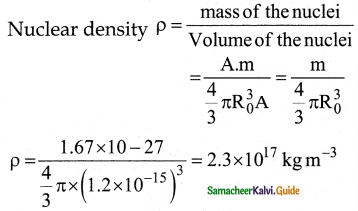
The nuclear density is independent of the mass number A. The nuclear density is almost constant for all the nuclei (Z > 10) irrespective of its size.
![]()
Question 16.
What is mass defect?
Answer:
In general, if M, mp and m are mass of the nucleus (\({ }_{Z}^{A} \mathrm{X}\)), the mass of proton and the mass of neutron respectively
mass defect ∆m = (Zmp + Nmn ) — M difference in mass ∆m is called mass defect.
The mass of any nucleus is always less than the sum of the mass of its indivitual constituents. The difference in mass ∆m is called mass defect.
Question 17.
What is binding energy of a nucleus? Give its expression.
Answer:
when Z protons and N neutrons combine to form a nucleus, mass equal to mass defect disappears and the corresponding energy is released. This is called the binding energy of the nucleus (BE) and is equal to (∆m) c2.
BE = (Zmp + Nmn – M ) c2
Question 18.
Calculate the energy equivalent of 1 atomic mass unit.
Answer:
Using Einstein’s mass-energy equivalence, the energy equivalent of one atomic mass unit
1u = 1.66 × 10-27 × (3 × 108)2
= 14.94 × 10-11 J ≈ 931 MeV
Question 19.
Give the physical meaning of binding energy per nucleon.
Answer:
The average binding energy per nucleon is the energy required to separate single nucleon from the particular nucleus.
\(\overline{\mathrm{BE}}\) = \(\frac{\left[\mathrm{Zm}_{\mathrm{H}}+\mathrm{Nm}_{\mathrm{n}}-\mathrm{M}_{\mathrm{A}}\right] \mathrm{C}^{2}}{\mathrm{~A}}\)
Question 20.
What is meant by radioactivity?
Answer:
The phenomenon of spontaneous emission of highly penetrating radiations such as α, β and γ rays by an element is called radioactivity.
![]()
Question 21.
Give the symbolic representation of alpha decay, beta decay and gamma decay.
Answer:
Alpha decay:
\({ }_{Z}^{A} \mathrm{X}\) → \(\begin{array}{l}
\mathrm{A}-4 \\
\mathrm{Z}-2
\end{array} \mathrm{Y}\) + \({ }_{2}^{4} \mathrm{He}\)
Here X is called the parent nucleus and Y is called the daughter nucleus.
β– decay:
\({ }_{Z}^{A} \mathrm{X}\) → \(\begin{array}{c}
\mathrm{A} \\
\mathrm{Z}+1
\end{array} \mathrm{Y}\) + e– + \(\bar{v}\)
It implies that the element X becomes Y by giving out an electron and antineutrino \(\bar{V}\)
β+ decay:
\({ }_{Z}^{A} \mathrm{X}\) → \(\begin{array}{c}
\mathrm{A} \\
\mathrm{Z}-1
\end{array} \mathrm{Y}\) + e+ + ν
It implies that the element X becomes Y by giving out an positron and neutrino (v).
Gamma decay:
\({ }_{Z}^{A} \mathrm{X*}\) → \({ }_{Z}^{A} \mathrm{Y}\) + gamma (γ) rays
Here the asterisk (*) means excited state nucleus. In gamma decay, there is no change in the mass number or atomic number of the nucleus.
Question 22.
In alpha decay, why the unstable nucleus emits \({ }_{2}^{4} \mathrm{He}\) nucleus? Why it does not emit four separate nucleons?
Answer:
After all \({ }_{2}^{4} \mathrm{He}\) consists of two protons and two neutrons. For example, if \({ }_{92}^{238} \mathrm{U}\) nucleus decays into \({ }_{90}^{234} \mathrm{Th}\) by emitting four separate nucleons (two protons and two neutrons), then the disintegration energy Q for this process turns out to be negative. It implies that the total mass of products is greater than that of parent \({ }_{92}^{238} \mathrm{U}\) nucleus. This kind of process cannot occur in nature because it would Violate conservation of energy. In any decay process, the conservation of energy, conservation of linear momentum and conservation of angular momentum must be obeyed.
Question 23.
What is mean life of nucleus? Give the expression.
Answer:
The mean lifetime of the nucleus is the ratio of sum or integration of life times of all nuclei to the total number nuclei present initially. The expression for mean life time, τ = \(\frac { 1 }{ λ }\).
τ = \(\frac{1}{\lambda}\)
Question 24.
What is half – life of nucleus? Give the expression.
Answer:
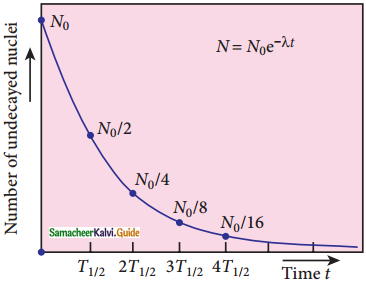
The half – life T1/2 is the time required for the number of atoms initally present to reduce to one half of the initial amount.
T1/2 = \(\frac{\ln 2}{\lambda}\) = \(\frac{0.6931}{\lambda}\)
![]()
Question 25.
What is meant by activity (or) decay rate? Give its unit.
Answer:
Activity (R) or decay rate which is the number of nuclei decayed per second and it is denoted as
R \(=\left|\frac{\mathrm{dN}}{\mathrm{dt}}\right|\).
R = \(\left|\frac{\mathrm{dN}}{\mathrm{dt}}\right|\) = λN0e-λt
R = R0e-λt
The SI unit of activity R is Becquerel and one Becquerel (Bq) is equal to one decay per second. There is also another standard unit for the activity called Curie (Ci).
1 Curie = 1 Ci = 3.7 × 1010 decays per second
1 Ci = 3.7 × 1010 Bq
Question 26.
Define curie.
Answer:
One curie was defined as number of decays per second in 1 g of radium and it is equal to 3.7 x 1010 decays/s.
Question 27.
What are the constituent particles of neutron and proton?
Answer:
According to quark model, proton is made up of two up quarks and one down quark and neutron is made up of one up quark and two down quark.
![]()
III. Long answer questions:
Question 1.
Explain the J.J. Thomson experiment to determine the specific charge of electron.
Answer:
1. In 1887, J.J. Thomson, measured the specific charge (e/m) of electron.
2. The specific charge is defined as the charge per unit mass of particle.
Principle:
3. In the presence of electric and magnetic fields, the cathode rays are deflected.
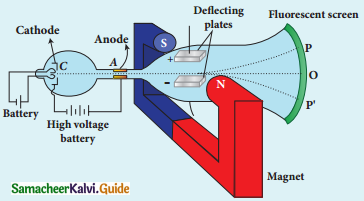
Arrangement of J.J. Thomson experiment to determine the specific charge of an electron
4. A highly evacuated discharge tube is used and cathode rays (electron beam) produced at cathode are attracted towards anode disc A.
5. Anode disc is made with pin hole in order to allow only a narrow beam of cathode rays.
6. These cathode rays are now allowed to pass through the parallel metal plates, maintained at high voltage.
7. Further, this gas discharge tube is kept in between pole pieces of magnet such that both electric and magnetic fields are perpendicular to eacth other.
8. When the cathode rays strike the screen, they produce scintillation and hence bright spot is observed.
9. This is achieved by coating the screen with zinc sulphide.
(i) Determination of velocity of cathode rays :
1. For a fixed electric field between the plates, the magnetic field is adjusted such that the cathode rays (electron beam) strike at the original position O
2. i.e magnitude of electric force is balanced by the magnitude of force due to magnetic field.
eE = eBν
=>ν = \(\frac{E}{B}\) ………………(1)
e- charge of the cathode rays
3. Electric force balancing the magnetic force – the path of electron beam is a straight line.
ii) Determination of specific charge:
1. Since the cathode rays (electron beam) are accelerated from cathode to anode, the potential energy of the electron beam at the cathode is converted into kinetic energy of the electron beam at the anode.
2. Let V be the potential difference between anode and cathode, then the potential energy is eV.
3. Then from law of conservation of energy.
e V = \(\frac{1}{2}\) mν2
⇒ \(\frac{e}{m}=\frac{1}{2 V}\) ν2
4. Substituting the value of velocity from equation (1), we get
\(\frac{\mathrm{e}}{\mathrm{m}}=\frac{1}{2 \mathrm{~V}} \frac{\mathrm{E}^{2}}{\mathrm{~B}^{2}}\)
5. Substituting the values of E, B and V, the specific charge can be determined as
\(\frac{\mathrm{e}}{\mathrm{m}}\) = 1.7 × 1011 C kg-1
![]()
Question 2.
Discuss the Millikan’s oil drop experiment to determine the charge of an electron.
Answer:
The Millikan’s experiment is used to determine one of the fundamental constants of nature known as charge of an electron.
Principle:
1. This method is based on the study of the motion of uncharged oil drop under free fall due to gravity and charged oil drop in a uniform electric field.
2. By adjusting electric field suitably, the motion of oil drop inside the chamber can be controlled – that is, it can be made to move up or down or even kept balanced in the field of view for sufficiently long time.
Experimental arrangement:
1. The apparatus consists of two horizontal circular metal plates A and B each with diameter around 20 cm and are separated by a small distance 1.5 cm.
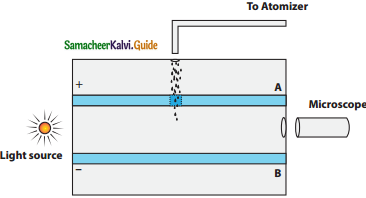
Millkan’s Experiment
2. These two parallel plates are enclosed in a chamber with glass walls. Further, plates A and B are given a high potential difference around 10 kV such that electric field acts vertically downward.
3. A small hole is made at the centre of the upper plate A and atomizer is kept exactly above the hole to spray the liquid.
4. When a fine droplet of highly viscous liquid (like glycerine) is sprayed using atomizer, it falls freely downward through the hole of the top plate only under the influence of gravity.
5. Few oil drops in the chamber can acquire electric charge (negative charge) because of friction with air or passage of x – rays in between the parallel plates.
6. Further the chamber is illuminated by light which is passed horizontally and oil drops can be seen clearly using microscope placed perpendicular to the light beam. These drops can move either upwards or downward.
(a) Determination of radius of the droplet:
Fg = gravitational force
Fb = buoyant force
Fv = viscous force
viscous force and buoyant force balance the gravitational force.
7. When the electric field is switched off, the oil drop accelerates downwards. Due to the presence of air drag forces, the oil drops easily attain its terminal velocity and moves with constant velocity.
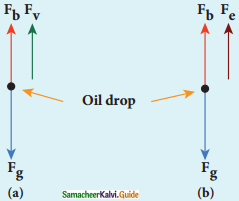
(a) Free body diagram of the oil drop without electric field
(b) Free body diagram of the oil drop with electric field
8. Let the gravitational force acting on the oil drop (downward) be Fb = mg, m = mass of the oil drop g = Acceleration due to gravity.
9. Let ρ be the density of the oil drop, and r be the radius of the oil drop, then the mass of the oil drop can be expressed in terms of its density as
ρ = \(\frac{\mathrm{m}}{\mathrm{V}}\)
m = ρ(\(\frac{4}{3}\) πr3) (volume of the sphere, V = \(\frac{4}{3}\) πr3)
10. The gravitational force can be written in terms of density as
Fg = mg
=>Fg = ρ(\(\frac{4}{3}\)) πr3
11. Let σ be the density of the air, the upthrust force experienced by the oil drop due to displaced air is
Fb = σ(\(\frac{4}{3}\) πr3)g
12. From Stokes law, the viscous force on the oil drop is.
Fv = 6πrυη
The force balancing equation is
Fg = Fb + Fv
ρ(\(\frac{4}{3}\) πr3)g = σ(\(\frac{4}{3}\) πr3)g + 6πrυη
\(\frac{4}{3}\) πr3(ρ – σ) = 6πrυη
\(\frac{2}{3}\) πr3(ρ – σ) = 3πrυη
r = \(\left[\frac{9 \eta v}{2(\rho-\sigma) g}\right]^{\frac{1}{2}}\) …………….(1)
Thus, equation (1) gives the radius of the oil drop.
(b) Determination of electric charge:
(a) Fe = qE
(c) buoyant force Fb
13. When the electric field is switched on, charged oil drops experience an upward electric force (qE).
14. Among many drops, one particulars drop can be chosen in the field of view of microscope and strength of the electric field is adjusted to make that particular drop to be stationary.
15. Under these circumstances, there will be no viscous force acting on the oil drop. Force acting on the oil droplet is
Fe + Fb = Fg
⇒ qE + \(\frac{4}{3}\) πr3 σg = \(\frac{4}{3}\) πr3 ρg
⇒ qE = \(\frac{4}{3}\) πr3 (ρ – σ)g
⇒ q = \(\frac{4}{3 \mathrm{E}}\) πr3 (ρ – σ)g …………..(2)
Substituting equation (1) in equation (2), we get
q = \(\frac{18 \pi}{\mathrm{E}}\left(\frac{\eta^{3} v^{3}}{2(\rho-\sigma) \mathrm{g}}\right)^{\frac{1}{2}}\)
16. Millikan repeated this experiment several times and computed the charges on oil drops. He found that the charge of any oil drop can be written as integral multiple of a basic value, (e = 1.6 × 10-19 C), which is nothing but the charge of an electron.
![]()
Question 3.
Derive the energy expression for hydrogen atom using Bohr atom model.
Answer:
Energy of a Hydrogen atom:
Bohr postulates is find the allowed energies of the atom for different allowed orbits of the electron.
(a) The electron in an atom moves around nucleus in circular orbits under the influence of coulomb electrostatic force of attraction.
(b) Electrons in an atom revolve around the nucleus only in certain discrete orbits called stationary orbits where it does not radiate electromagnetic energy.
Angular momentum quantization condition,
L = n\(\hbar\) = \(\frac{\mathrm{nh}}{2 \pi}\)
h – planck’s constant
n – principal quantum number of the orbit.
c) An electron can jump from one orbit to another orbit by absorbing or emitting a photon whose energy is equal to the difference in energy (∆E) between the two orbital levels.
energy quantization condition
∆E = Efinal – Einitial = hυ = \(\frac{\mathrm{hc}}{\lambda}\)
λ – wavelength of the radiation
c – speed of light
υ – frequency of the radiation
Radius of the orbit of the electron:
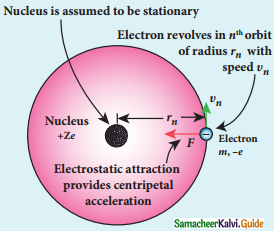
Electron revolving around the nucleus
1. The nucleus has a positive charge +Ze.
2. Let z be the atomic number of the atom.
3. Let -e be the charge of the electron.
4. The nucleus at rest and an electron revolving around the nucleus in a circular orbit of radius rn with a constant speed υn
Coulomb’s law, the force of attraction between the nucleus and the electron is
\(\overrightarrow{\mathrm{F}}_{\text {coulomb }}\) = \(\frac{1}{4 \pi \varepsilon_{0}} \frac{(+\mathrm{Ze})(-\mathrm{e})}{\mathrm{r}_{\mathrm{n}}^{2}} \hat{\mathrm{r}}\)
= –\(\frac{1}{4 \pi \varepsilon_{0}} \frac{Z \mathrm{e}^{2}}{\mathrm{r}_{\mathrm{n}}^{2}} \hat{\mathrm{r}}\)
5. This force provides necessary centripetal force.
\(\overrightarrow{\mathrm{F}}_{\text {centripetal }}=\frac{m v_{n}^{2}}{r_{n}} \hat{r}\)
where m be the mass of the electron that moves with a velocity υn in a circular orbit.
Therfore,
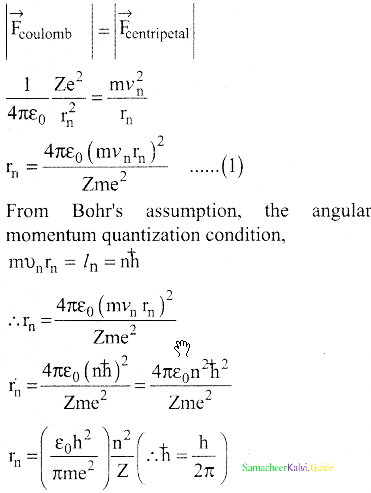
Where n∈N ε0, n, e and π → are constant
radius of the orbit,
rn = a0 \(\frac{n^{2}}{Z}\)
Bohr radius a0 = \(\frac{\varepsilon_{0} h^{2}}{\pi m e^{2}}\)
a0 = 0.529 Å
Bohr radius is also used as unit of length called Bohr
1 Bohr = 0.53 Å
For hydrogen atom Z = 1
rn = a0 n2
rn α n2
For the first orbit (ground sate)
r1 = a0
r2 = 4a0 = 4r1
r3 = 9a0 = 9r1
r4 = 16a0 = 16r1
The energy of an electron in the nth orbit:
Since the electrostatic force is a conservative force, the potential energy for the nth orbit is
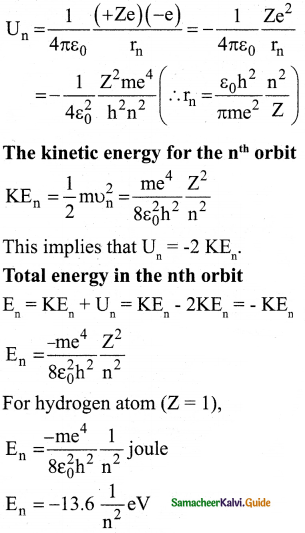
6. The negative sign in the equation indicates that the electron is bound to the nucleus
7. where n stands for a principal quantum number.
8. The energies of the excited states come closer and closer together when the principal quantum number n takes higher values.
9. The ground state energy of hydrogen (-13.6 eV) is used as a unit of energy called Rydberg (lRydberg = -13.6eV).
10. For the first orbit (ground state), the total energy of electron is E1 = -13.6 eV.
11. For the second orbit (first excited state), the total energy of electron is E2 = – 3.4eV.
12. For the third orbit (second excited state), the total energy of electron ie E3 = -1.51 eV and so on.
13. When the electron is taken away to an infinite distance (very far distance) from nucleus, both the potential energy and kinetic energy terms vanish and hence the total energy also vanishes.
![]()
Question 4.
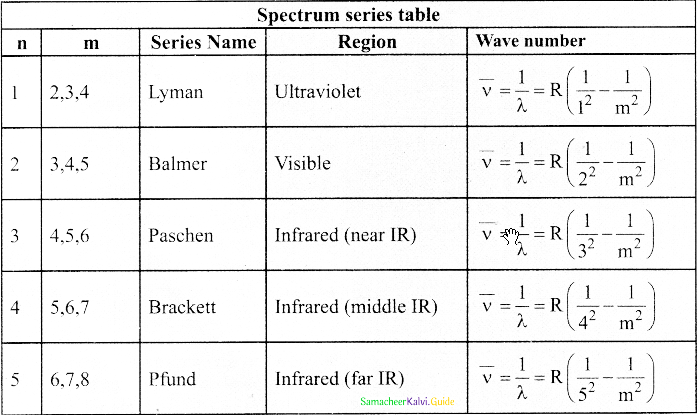
Discuss the spectral series of hydrogen atom.
Answer:
Spectral series of hydrogen atom:
1. As electron in excited states have very small lifetime, these electrons jump back to ground state through spontaneous emission in a short duration of time (approximately 10) by emitting the radiation with same wavelength (or frequency) corresponding to the colours is absorbed. This is called emission spectroscopy.
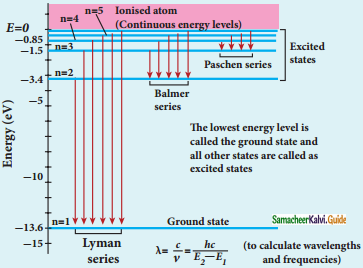
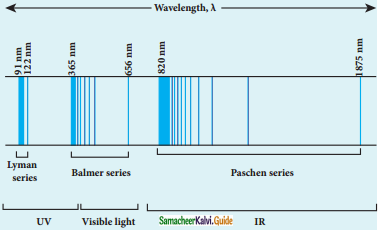
Spectral series – Lyman, Balmer, Paschen series
2. In each series, the distance of separation between the consecutive wavelengths decreases from higher wavelength to the lower wavelength, and also wavelength in each series approach a limiting value known as the series limit.
3. The wavelengths of these spectral lines perfectly agree with the equaion derived from Bohr atom model.
\(\frac{1}{\lambda}=\mathrm{R}\left(\frac{1}{\mathrm{n}^{2}}-\frac{1}{\mathrm{~m}^{2}}\right)=\overline{\mathrm{v}}\) …………..(1)
where \(\bar{v}\) is known as wave number which is inverse of wavelength, R is known as Rydberg
constant whose value is 1.09737 × 107 m-1 and m and n are positive integers such that m > n.
The various spectral series are discussed below:
Question 5.
Explain the variation of average binding energy with the mass number by graph and discuss its features.
Answer:
Binding energy curve :
1. \(\overline{\mathrm{BE}}\) is plotted against A of all known nuclei.
2. It gives a curve as seen in Figure.
3. average binding energy per nucleon \(\overline{\mathrm{BE}}\).
It is given by,
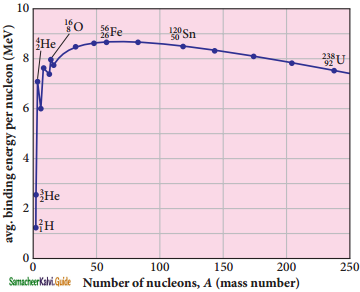
Avg. binding energy of the nucleus
4. The average binding energy per nucleon is the energy required to separate single nucleon from the particular nucleus.
Important inferences from of the average binding energy curve:
1. The value of \(\overline{\mathrm{BE}}\) rises as the mass number increases until it reaches a maximum value of 8.8 MeV for A = 56 (iron) and then it slowly decreases.
2. The average binding energy per nucleon is about 8.5 MeV for nuclei having mass number between A = 40 and 120. These elements are comparatively more stable and not radioactive.
3. For higher mass numbers, the curve reduces slowly and \(\overline{\mathrm{BE}}\) for uranium is about 7.6 MeV. They are unstable and radioactive.
From Figure if two light nuclei with A < 28 combine with a nucleus with A < 56, the binding energy per nucleon is more for final nucleus than initial nuclei. Thus, if the lighter elements combine to produce a nucleus of medium value A, a large amount of energy will be released. This is the basis of nuclear fusion and is the principle of the hydrogen bomb.
4. If a nucleus of heavy element is split (fission) into two or more nuclei of medium value A, the energy released would again be large. The atom bomb is based on this principle and huge energy of atom bombs comes from this fission when it is uncontrolled.
![]()
Question 6.
Explain in detail the nuclear force.
Answer:
1. Nucleus contains protons and neutrons. From electrostatics, like charges repel each other.
2. In the nucleus, the protons are separated by a distance of about a few Fermi (10-15 m), they must exert on each other a very strong repulsive force. For example,
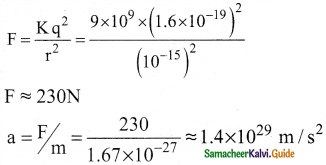
3. This is nearly 1028 times greater than the acceleration due to gravity.
4. From this observation, it was concluded that there must be a strong attractive force between protons to overcome the repulsive Coulomb’s force.
5. This attractive force which holds the nucleus together is called strong nuclear force.
6. A few properties of strong nuclear force are the strong nuclear force is of very short range, acting only up to a distance of a few Fermi.
7. But inside the nucleus, the repulsive Coulomb force or attractive gravitational forces between two protons are much weaker than the strong nuclear force between two protons.
8. Similarly, the gravitational force between two neutrons is also much weaker than strong nuclear force between the neutrons. So nuclear force is the strongest force in nature.
9. The strong nuclear force is attractive and acts with an equal strength between proton-proton, proton-neutron. and neutron – neutron.
10. Strong nuclear force does not act on the electrons. So it does not alter the chemical properties of the atom.
Question 7.
Discuss the alpha decay process with an example.
Answer:
Alpha decay:
1. When unstable nuclei decay by emitting an a – particle (\({ }_{2}^{4} \mathrm{He}\) nucleus), it loses two protons and two neutrons. As a result, its atomic number Z decreases by 2, the mass number decreases by 4. The alpha decay process symbolically represented as.
\({ }_{Z}^{A} \mathrm{X}\) → \({ }_{Z-2}^{A-4} \mathrm{Y}\) + \({ }_{2}^{4} \mathrm{He}\)
2. Here X is called the parent nucleus and Y is called the daughter nucleus.
3. Example:
Decay of Uranium \({ }_{92}^{238} \mathrm{U}\) to thorium \({ }_{90}^{234} \mathrm{Th}\) with the emission of \({ }_{2}^{4} \mathrm{He}\) nucleus (α – particle)
\({ }_{92}^{238} \mathrm{U}\) → \({ }_{90}^{234} \mathrm{Th}\) + \({ }_{2}^{4} \mathrm{He}\)
4. As already mentioned, the total mass of the daughter nucleus and \({ }_{2}^{4} \mathrm{He}\) nucleus is always
5. less than that of the parent nucleus. The difference in mass (∆m = mx – my -mα ) is released as energy called disintegration energy Q and is given by
Q = (mx – my – mα) c2
6. For spontaneous decay (natural radioactivity) Q > 0. In alpha decay process, the disintegration energy is certainly positive (Q > 0).
7. In fact, the disintegration energy Q is also the net kinetic energy gained in the decay process or if the parent nucleus is at rest, Q is the total kinetic energy of daughter nucleus and the \({ }_{2}^{4} \mathrm{He}\) nucleus.
8. Suppose Q < 0, then the decay process cannot occur spontaneously and energy must be supplied to induce the decay.
![]()
Question 8.
Discuss the beta decay process with examples.
Answer:
In beta decay, a radioactive nucleus emits either electron or positron. If electron (e–) is emitted, it is called β– decay and if positron (e+) is emitted, it is called p+ decay. The positron is an anti-particle of an electron whose mass is same as that of electron and charge is opposite to that of electron – that is, +e. Both positron and electron are referred to as beta particles.
1. β– decay:
In β– decay, the atomic number of the nucleus increases by one but mass number remains the same. This decay is represented by
\(_{ Z }^{ A }{ X }\) → \(_{ Z+12 }^{ A }{ Y}\) + e– + \(\bar { v } \) …(1)
It implies that the element X becomes Y by giving out an electron and antineutrino (\(\bar { v } \)). In otherwords, in each β– decay, one neutron in the nucleus of X is converted into a proton by emitting an electron (e–) and antineutrino. It is given by
n → p + e– + \(\bar { v } \)
Where p -proton, \(\bar { v } \) -antineutrino. Example: Carbon (\(_{ 6 }^{ 14 }{ C }\)) is converted into nitrogen (\(_{ 7 }^{ 14 }{ N }\)) through β- decay.
\(_{ 6 }^{ 14 }{ C }\) → \(_{ 7 }^{ 14 }{ N }\) + e– + \(\bar { v } \)
2. β+ decay:
In p+ decay, the atomic number is decreased by one and the mass number remains the same. This decay is represented by
\(_{ Z }^{ A }{ X }\) → \(_{ Z-12 }^{ A }{ Y}\) + e+ + v
It implies that the element X becomes Y by giving out a positron and neutrino (v). In other words, for each β+ decay, a proton in the nucleus of X is converted into a neutron by emitting a positron (e+) and a neutrino. It is given by
p → n + e+ + v
However, a single proton (not inside any nucleus) cannot have β+ decay due to energy conservation, because neutron mass is larger than proton mass. But a single neutron (not inside any nucleus) can have β– decay.
Example: Sodium (\(_{ 11 }^{ 23 }{ Na }\)) is converted into neon (\(_{ 10 }^{ 22 }{ Ne }\)) decay.
\(_{ 11 }^{ 23 }{ Na }\) → \(_{ 10 }^{ 22 }{ Ne }\) + e+ + v
Beta-decay:
In beta decay, a radioactive nucleus emits either electron or positron. If electron (e–) is emitted, it is called β– decay and if positron (e+) is emitted, it is called β+ decay. The positron is an anti – particle of an electron whose mass is same as that of electron and charge is opposite to that of electron – that is, +e. Both positron and electron are referred to as beta particles.
Question 9.
Discuss the gamma decay process with example.
Answer:
Gamma decay :
1. In α and β decay, the daughter nucleus is in the excited state most of the time. The typical life time of excited state is approximately 10-11 s. So this excited state nucleus immediately returns to the ground state or lower energy state by emitting highly energetic photons called γ rays. In fact, when the atom is in the excited state, it returns to the ground state by emitting photons of energy in the order of few eV. But when the excited state nucleus returns to its ground state, it emits a highly energetic photon (y rays) of energy in the order of MeV. The gamma decay is given by
![]()
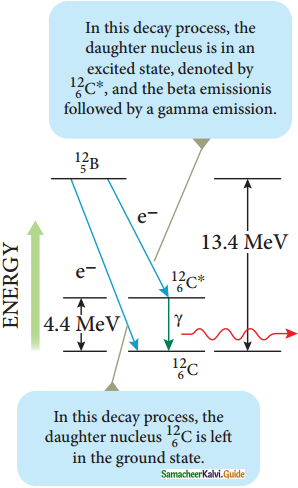
Gamma decay
2. Here the asterisk (*) means excited state nucleus. In gamma decay, there is no change in the mass number or atomic number of the nucleus.
3. Boron (\({ }_{5}^{12} \mathrm{~B}\)) has two beta decay modes as shown in figure.
4. It undergoes beta decay directly into ground state carbon \({ }_{6}^{12} \mathrm{C}\) by emitting an electron of maximum of energy 13.4 MeV.
5. It undergoes beta decay to an excited state \({ }_{6}^{12} \mathrm{C}^{*}\) by emitting an electron of maximum energy 9.0 MeV followed by gamma decay to ground state by emitting a photon of energy 4.4 MeV.
It is represented by
\({ }_{6}^{12} \mathrm{~B} \rightarrow{ }_{6}^{12} \mathrm{C}+\mathrm{e}^{-}+\overline{\mathrm{v}}\)
![]()
Question 10.
Obtain the law of radioactivity.
Answer:
Law of radioactive decay:
Radioactive law of disintegration:
1. At any instant t, the number of decays per unit time, called rate of decay \(\left(\frac{d N}{d t}\right)\) is proportional to the number of nuclei (N) at the same instant.
\(\frac{d N}{d t}\) α N
\(\frac{d N}{d t}\) = -λN ………………(1)
2. Here proportionality constant λ is called decay constant which is different for different radioactive sample the negative sign in the equaion implies that the N is decreasing with time.
By rewriting the equation (1) we get
dN = -λNdt …………….(2)
3. Here dN represents the number of nuclei decaying in the time interval dt.
4. Let us assume that at time t = 0 s, the number of nuclei present in the radioactive sample is N0
\(\frac{d N}{N}\) = -λdt ……………..(3)
5. By integrating the equaion (3)
6. We can calculate the number of undecayed nuclei N at any time t.
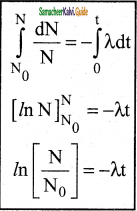
Law of radioactive decay
7. Taking exponentials on both sides, we get
8. N = N0 e-λt …………..(4) (Note: elnx = ey = x = ey)
9. Equation (4) is called the law of radioactive decay.
10. N0 denotes the number of nuclei at initial time t = 0.
11. N denotes the number of undecayed nuclei present at any time t
12. Note that the number of atoms is decreasing exponentially over the time.
13. This implies that the time taken for all the radioactive nuclei to decay will be infinite.
Activity (R):
Activity or decay rate which is the number of nuclei decayed per second. It is denoted as R. R is a positive quantity.
R = \(\left|\frac{\mathrm{d} \mathrm{N}}{\mathrm{dt}}\right|\)
N = N0 e-λt
R = λN0e-λt,
R = R0 eλ ………………(5)
Where R0 = λN0
eqn (1) is also equivalent to radioactive law of decay.
Here,
R0 is the activity of the sample at t = 0
R is the activity of the sample at any time t. Activity also shows exponential decay behavior.
The activity R also canbe expressed interms of number of undecayed atoms present at any time t.
R = λN …………..(3)
λ – decay constant
N – Number of undecayed nuclei at the same time t.
Since N decreases over time, R also decreases.
SI unit: Becquerel (Bq)
Question 11.
Discuss the properties of neutrino and its role in beta decay.
Answer:
Neutrino:
Initially, it was thought that during beta decay, a neutron in the parent nucleus is converted to the daughter nuclei by emitting only electron as given by
\(_{ Z }^{ A }{ X }\) → \(_{ Z+1 }^{ A }{ X}\) Y+e–
1. But the kinetic energy of electron coming out of the nucleus did not match with the experimental results. In alpha decay, the alpha particle takes only certain allowed discrete energies whereas in beta decay, it was found that the beta particle (i.e, electron) have a continuous range of energies.
2. But the conservation of energy and momentum gives specific single values for electron energy and the recoiling nucleus Y. It seems that the conservation of energy, momentum are violated and could not be explained why energy of beta particle have continuous range of values. So beta decay remained as a puzzle for several years.
3. After a detailed theoretical and experimental study, in 1931 W. Pauli proposed a third particle which must be present in beta decay to carry away missing energy and momentum. Fermi later named this particle the neutrino (little neutral one) since it has no charge, have very little mass.
4. For many years, the neutrino (symbol v , Greek nu) was hypothetical and could not be verified experimentally. Finally, the neutrino was detected experimentally in 1956 by Fredrick Reines and Clyde Cowan. Later Reines received Nobel prize in physics in the year 1995 for his discovery.
The neutrino has the following properties
- It has zero charge
- It has an antiparticle called anti-neutrino.
- Recent experiments showed that the neutrino has very tiny mass.
- It interacts very weakly with the matter. Therefore, it is very difficult to detect. In fact, in every second, trillions of neutrinos coming from the sun are passing through our body without any interaction.
![]()
Question 12.
Explain the idea of carbon dating.
Answer:
1. The interesting application of beta decay is radioactive dating or carbon dating.
2. Using this technique, the age of an ancient object can be calculated.
3. All living organisms absorb crabon dioxide (Co2) from air to synthesize organic molecules.
In this absorbed Co2, the major part is \({ }_{6}^{12} \mathrm{C}\) and very small fraction (1.3 × 10-12) is radioactive \({ }_{6}^{14} \mathrm{C}\) whose half life is 5730 years.
4. Carbon 14 in the atmosphere is always decaying but at the same time, cosmic rays from outer space are continuously bombarding the atoms in the atmosphere which produces \({ }_{6}^{14} \mathrm{C}\)
5. So the continuous production and decay of \({ }_{6}^{14} \mathrm{C}\) in the atmosphere keep the ratio of \({ }_{6}^{14} \mathrm{C}\) to \({ }_{6}^{12} \mathrm{C}\) always constant.
6. Since our human body, tree or any living organism continuously absorb Co2 from the atmosphere, the ratio of \({ }_{6}^{14} \mathrm{C}\) to \({ }_{6}^{12} \mathrm{C}\) in the living organism is also nearly constnt.
7. But when the organism dies, it stops absorbing Co2
8. Since \({ }_{6}^{14} \mathrm{C}\) starts to decay, the ratio of \({ }_{6}^{14} \mathrm{C}\) to \({ }_{6}^{12} \mathrm{C}\) in a dead organism or specimen decreases over the years.
9. Suppose the ratio of \({ }_{6}^{14} \mathrm{C}\) to \({ }_{6}^{12} \mathrm{C}\) in the ancient tree pieces excavated is known, then the age of the tree pieces can be calculated.
Question 13.
Discuss the process of nuclear fission and its properties.
Answer:
Nuclear Fission :
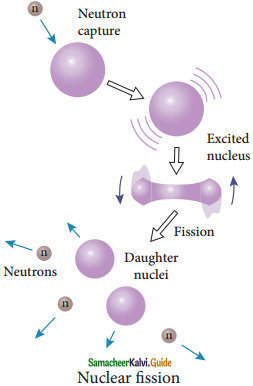
1. The process of breaking up of the nucleus of a heavier atom into two smaller nuclei with the release of a large amount of energy is called nuclear fission.
2. In 1939, German scientists Otto Hahn and F. Strassman discovered that when uranium nucleus is bombarded with a neutron, it breaks up into two smaller nuclei of comparable masses with the release of energy.
3. Uranium undergoes fission reaction in 90 different ways.
4. The most common fission reactions of \({ }_{92}^{234} \mathrm{U}\) nuclei are shown here.
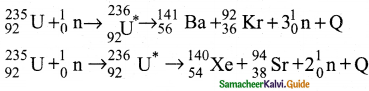
5. Here Q is energy released during the decay of each uranium nuclei.
6. When the slow neutron is absorbed by the uranium nuclei, the mass number increases by one and goes to an excited state \({ }_{92}^{234} \mathrm{U}^{*}\)
7. But this excited state does not last longer than 10-12s and decay into two daughter nuclei along with 2 or 3 neutrons.
8. From each reaction, on an average, 2.5 neutrons are emitted.
Energy released in fission:
1. We can calculate the energy (Q) released in each uranium fission reaction
![]()

2. So the energy released in each fission = 0.225303 × 931 MeV ≈ 200 MeV
3. This energy first appears as kinetic energy of daughter nuclei and neutrons.
4. But later, this kinetic energy is transferred to the surrounding matter as heat.
![]()
Question 14.
Discuss the process of nuclear fusion and how energy is generated in stars?
Answer:
Nuclear Fusion:
1. When two or more light nuclei (A < 20) combine to form a heavier nucleus, then it is called nuclear fusion.
2. In the nuclear fusion, the mass of the resultant nucleus is less than the sum of the masses of original light nuclei. The mass difference appears as energy. The nuclear fusion never occurs at room temperature unlike nuclear fission. It is because when two light nuclei come closer to combine, it is strongly repelled by the coulomb repulsive force.
3. To overcome this repulsion, the two light nuclei must have enough kinetic energy to move closer to each other such that the nuclear force becomes effective. This can be achieved if the temperature is very much greater than the value 107 K. When the surrounding temperature reaches around 107 K, lighter nuclei start fusing to form heavier nuclei and this resulting reaction is called thermonuclear fusion reaction.
Energy generation in stars:
1. The natural place where nuclear fusion occurs is the core of the stars, since its temperature is of the order of 107 K. In fact, the energy generation in every star is only through thermonuclear fusion. Most of the stars including our Sun fuse hydrogen into helium and some stars even fuse helium into heavier elements.
2. The early stage of a star is in the form of cloud and dust. Due to their own gravitational pull, these clouds fall inward. As a result, its gravitational potential energy is converted to kinetic energy and finally into heat.
3. When the temperature is high enough to initiate the thermonuclear fusion, they start to release enormous energy which tends to stabilize the star and prevents it from further collapse.
4. The sun’s interior temperature is around 1.5 x 107 K. The sun is converting 6 x 1011 kg hydrogen into helium every second and it has enough hydrogen such that these fusion lasts for another 5 billion years.
5. When the hydrogen is burnt out, the sun will enter into new phase called red giant where helium will fuse to become carbon. During this stage, sun will expand greatly in size and all its planets will be engulfed in it.
6. According to Hans Bethe, the sun is powered by proton-proton cycle of fusion reaction. This cycle consists of three steps and the first two steps are as follows:
\(_{ 1 }^{ 1 }{ H }\) + \(_{ 1 }^{ 1 }{ H }\) → \(_{ 1 }^{ 2 }{ H }\) + e+ + v …… (1)
\(_{ 1 }^{ 1 }{ H }\) + \(_{ 1 }^{ 2 }{ H }\) → \(_{ 2 }^{ 3 }{ H }\) + γ …… (2)
A number of reactions are possible in the third step. But the dominant one is
\(_{ 2 }^{ 3 }{ H }\) + \(_{ 12}^{ 3 }{ H }\) → \(_{ 2 }^{ 4}{ H }\) + \(_{ 1 }^{ 1 }{ H }\) + \(_{ 1 }^{ 1 }{ H }\)…… (3)
The overall energy production in the above reactions is about 27 MeV. The radiation energy we received from the sun is due to these fusion reactions.
Question 15.
Describe the working of nuclear reactor with a block diagram.
Answer:
Nuclear Reactor:
1. Nuclear Reactor is a system in which the nuclear fission takes place in a self sustained controlled manner and the energy produced is used either for research purpose or for power generation.
2. The first nuclear reactor was built in the year 1942 at Chicago, USA by physicist Enrico Fermi.
3. The main parts of a nuclear reactor are fuel, moderator and control rods.
4. In addition to this, there is a cooling system which is connected with power generation set up.
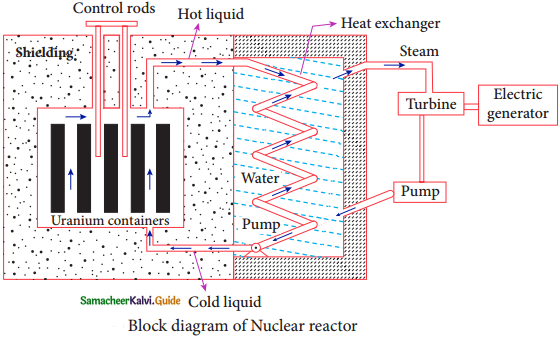
Fuel:
The fuel is fissionable material, usually uranium or plutonium. Naturally occurring uranium contains only 0.7% of \({ }_{92}^{235} \mathrm{U}\) and 99.3% are only \({ }_{92}^{238} \mathrm{U}\). So the \({ }_{92}^{238} \mathrm{U}\) must be enriched such that it contains at least 2 to 4% 0f \({ }_{92}^{235} \mathrm{U}\).
Neutron Source :
1. In addition to this, a neutron soruce is required to initiate the chain reaction for the first time.
2. A mixture of beryllium with plutonium or polonium is used as the neutron source. During fission of \({ }_{92}^{235} \mathrm{U}\), only fast neutrons are emitted but the probability of initiating fission by it in another nucleus is very low. Therefore, slow neutrons are preferred for sustained nuclear reactions.
Moderators:
1. The moderator is a material used to convert fast neutrons into slow neutrons.
2. Usually the moderators are chosen in such a way that it must be very light nucleus having mass comparable to that of neutrons. Hence, these light nuclei undergo collision with the neutrons and the speed of the neutron is reduced.
3. Most of the reactors use water, heavy water (D20) and graphite as moderators.
4. A billiard ball striking a stationary billiard ball of equal mass would itself be stopped but the same billiard ball bounces off almost with same speed when it strikes a heavier mass. This is the reason for using lighter nuclei as moderators.
Control rods:
1. The control rods are used to adjust the reaction rate. During each fission, on an average 2.5 neutrons are emitted and in order to have the controlled chain reactions, only one neutron is allowed to cause another fission and the remaining neutrons are absorbed by the control rods.
2. Usually cadmium or boron acts are control rod material and these rods are inserted into the uranium blocks.
3. Depending on the insertion depth of control rod into the uranium, the average number of neutrons produced per fission is set to be equal to one or greater than one.
4. If the average number of neutrons produced per fission is equal to one, then reactor is said to be in critical state.
5. In fact, all the nuclear reactors are maintained in critical state by suitable adjustment of control rods.
6. If it is greater than once, then reactor is said to be in super – critical and it may explode sooner or may cause massive destruction.
Shielding:
For protection against harmful radiations, the nuclear reactor is surrounded by a concrete wall of thickness of about 2 to 2.5 m.
Cooling System:
1. The cooling system removes the heat generated in the reactor core.
2. Ordinary water, heavy water and liquid sodium are used as coolant since they have very high specific heat capacity and have large boiling point under high pressure.
3. This coolant passes through the fuel block and carries away the heat to the steam generator through heat exchanger.
4. The steam runs the turbines which produce electricity in power reactors.
![]()
Question 16.
Explain in detail the four fundamental forces.
Answer:
Fundamental forces of nature:
- It is known that there exists gravitational force between two masses and it is universal in nature. Our planets are bound to the sun through the gravitational force of the sun.
- The force between two charges there exists electromagnetic force and it plays major role in most of our day-to-day events.
- The force between two nucleons, there exists a strong nuclear force and this force is responsible for the stability of the nucleus.
- In addition to these three forces, there exists another fundamental force of nature called the weak force. This weak force is even shorter in range than nuclear force. This force plays an important role in beta decay and energy production of stars.
- During the fusion of hydrogen into helium in sun, neutrinos and enormous radiations are produced through weak force.
- Gravitational, electromagnetic, strong and weak forces are called fundamental forces of nature.
Question 17.
Briefly explain the elementary particles of nature.
Answer:
1. An atom has a nucleus surrounded by electrons and nuclei is made up of protons and neutrons.
2. Tikl 1960s, it was thought that protons, neutrons and electrons are fundamental building blocks of matter.
3. In 1964, physicist Murray Geliman and George Zweig theoretically proposed that protons and neutrons are not fundamental particles; in fact they are made up of quarks.
4. These quarks are now considered as elementary particles of nature.
5. Electrons are fundamental or elementary particles because they arc not made up of anything.
6. In the year 1968, the quarks were discovered experimentally by Stan ford Linear Accelerator Center (SLAC), USA.
7. There are six quarks namely, up, down, charm, strange, top and bottom and their antiparticles.
8. All these quarks have fractional charges.
9. Charge of up quarks is +\(\frac{2}{3}\)e
10. Charge of down quark is –\(\frac{1}{3}\)e
According to the quark model:
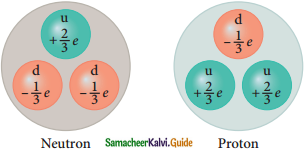
Constituents of Nucleons
| Proton is made up of two up quarks and one down quark | Neutron is made up of one up quark and two down quarks |
11. The study of elementary particles is called particle physics.
12. To date, more than 20 Nobel prizes have been awarded in the field of particle physics.
![]()
IV. Exercises:
Question 1.
Consider two hydrogen atoms HA and HB ground state. Assume that hydrogen atom HA is at rest and hydrogen atom HB is moving with a speed and make head-on collide on the stationary hydrogen atom HA. After the strike, both of them move together. What is the minimum value of the kinetic energy of the moving hydrogen atom HB, such that any one of the hydrogen atoms reaches one of the excitation states?
Answer:
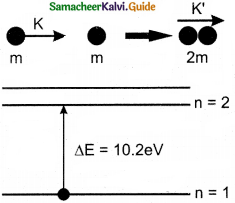
From conservation of linear momentum, p = p’
\(\sqrt{2 \mathrm{~km}}=\sqrt{2 \mathrm{k}^{\prime}(2 \mathrm{~m})}\)
(or) K = 2K’ …………….(1)
From conservation of energy
K = K’ + ∆E …………….(2)
Solving Eqs (1) and (2), we get
∆E = K/2
Now minimum value of E for hydrogen atom is 10.2 eV
∆E ≥ 10.2 eV
K/2 ≥ 10.2
K ≥ 20.4 eV
Question 2.
In the Bohr atom model, the frequency of transitions is given by the following expression ν = Rc\(\left(\frac{1}{n^{2}}-\frac{1}{m^{2}}\right)\) where n < m, Consider the following transition:
| Transitions | M → n |
| 1 | 3 → 2 |
| 2 | 2 → 1 |
| 3 | 3 → 1 |
Show that the frequency of these transitions obey the sum rule (which is known as the Ritz combination principle)
Answer:
Data:
ν = Rc\(\left(\frac{1}{n^{2}}-\frac{1}{m^{2}}\right)\) where n < m
The principle states that the spectral lines of any element included frequencies that are either the sum or the difference of the frequencies of two other lines.
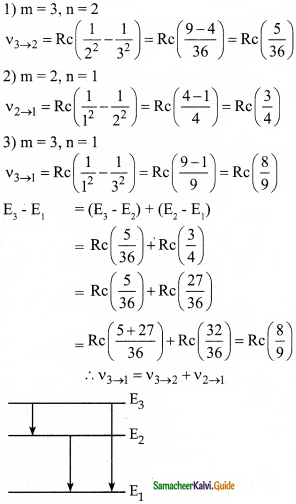
Question 3.
(a) A hydrogen atom is excited by radiation of wavelength 97.5 nm. Find the principal quantum number of the excited state.
(b) Show that the total number of lines in emission spectrum is \(\frac{\mathrm{n}(\mathrm{n}-1)}{2}\) and compute the total number of possible lines in emission spectrum.
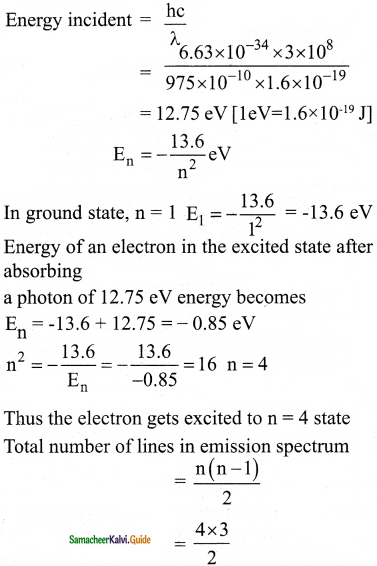
Answer:
Data :
λ = 97.5 nm = 97.5 × 10-9 m = 975 × 10-10 m
Question 4.
Calculate the radius of the earth if the density of the earth is equal to the density of the nucleus, (mass of earth 5.97 × 1024 kg].
Answer:
Data:
mass of earth = 5.97 × 1024 kg
Nuclear density = 2.3 × 1017 kg/m3
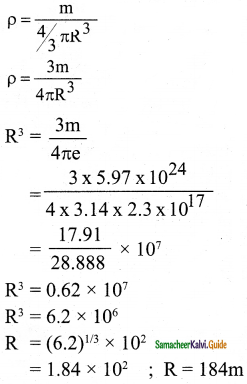
Question 5.
Calculate the mass defect and the binding energy per nucleon of the \(\text { }_{47}^{108} \mathrm{Ag}\) nucleus. (atomic mass of Ag = 107.905949)
Answer:
The \(\text { }_{47}^{108} \mathrm{Ag}\) nucleus contains 47 protons and 61 neutrons
mass of 47 protons = 47 × 1.007825 = 47.367775 u
mass of 61 neutrons =61 × 1.008665 = 61.528565 u
Total mass = 47.367775 + 61.528565 = 108.89634 u
Mass defect, ∆M = 108.89634 – 107.905949
∆M = 0.990391 u
BE = 0.990391 u × c2
BE = 0.990391 × 931 MeV
\(\frac{\mathrm{BE}}{\mathrm{A}}\) = \(\frac{0.990391 \times 931}{108}\) Mev
\(\frac{\mathrm{BE}}{\mathrm{A}}\) = 8.5 MeV/A.
![]()
Question 6.
Half-lives of two radioactive elements A and B are 20 minutes and 40 minutes respectively. Initially, the samples have equal number of nuclei. Calculate the ratio of decayed numbers of A and B nuclei after 80 minutes.
Ans:
Data:
(T1/2)A = 20 minutes
(T1/2)B = 40 minutes
t = 80 minutes
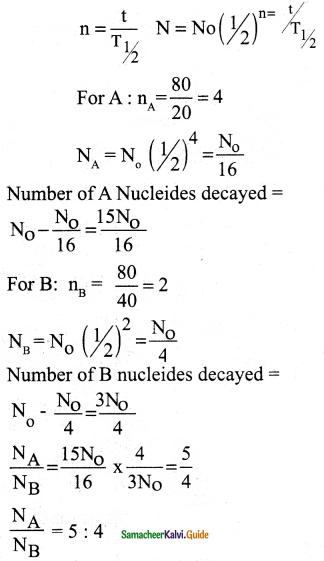
Question 7.
On your birthday, you measure the activity of the sample 210 Bi which has a half – life of 5.01 days. The initial activity that you measure is 1 µCi.
(a) What is the approximate activity of the sample on your next birthday? Calculate
(b) the decay constant
(c) the mean life
(d) an initial number of atoms.
Answer:
Data:
T1/2 = 5.01 days
1 ci = 3.7 × 1010 decays/s
R0 = 1 µci
t = one year = 365 days
n = \(\frac{t}{T_{1 / 2}}\)
= \(\frac{365}{5.01}\) ≈ 73 half lives
(a) R = (1/2)n R0
R = (1/2)73 (1 µci)
R = 10-22 µci
(b) λ = \(\frac{0.6931}{\mathrm{~T}_{1 / 2}}\) (1 day = 86400S)
λ = \(\frac{0.6931}{5.01 \times 86400}\)
λ = 1.6 × 10-6 S
(c) τ = \(\frac{1}{\lambda}\)
τ = \(\frac{\mathrm{T}_{1 / 2}}{0.6931}\)
= \(\frac{5.01}{0.6931}\)
τ = 7.24 days
(d) R0 = N0 λ
N0 = \(\frac{R_{0}}{\lambda}\)
= \(\frac{1 \times 10^{-6} \times 3.7 \times 10^{10}}{1.6 \times 10^{-6}}\)
N0 = 2.31 × 1010
Question 8.
Calculate the time required for 60% of a sample of radon to undergo decay. Given T1/2 of radon = 3.8 days.
Answer:
Data:
Half life of radon = 3.8 days
Amount of sample disintegrated = 60%
Time required =?
λ = \(\frac{0.6931}{3.8}\) per day
Amount of sample disintegrated = 60%
Amount of sample present = 40%
Let N0 be the original amount of the sample present.
From law of disintegration,
N = N0 e-λt
Substituting N = 40% of N0,
\(\left(\frac{40}{100}\right)\) N0 = N0 e-λt
e-λt = \(\left(\frac{40}{100}\right)\)
e-λt = \(\frac{40}{100}\)
e-λt = \(\left(\frac{100}{40}\right)\) = 2.5
Log e 2.5 = λ × t
t = \(\frac{\log _{10} 2.5 \times 2.3026 \times 3.8}{0.6931}\)
t = 5.022 days
Question 9.
Assuming that energy released by the fission of a single \({ }_{92}^{235} \mathrm{U}\) nucleus is 200 MeV, calculate the number of fissions per second required to produce 1-watt power.
Answer:
Data:
Energy per fission = 200 MeV
Required power = 1 watt = 1 J/s
Number of fissions per second =?
Since the two energies are in different units, we must convert them into the same unit.
Energy released per fission = 200 MeV
= 200 × 106 eV
= 200 × 106 × 1.6 × 10-19 J
= 320 × 10-13 J [ 1 eV = 1.6 × 10-19 J]
Let N be the number of fission per second, producing 1 W
Energy per fission × N = Total energy released per second.
320 × 10-13 × N= 1 J/S
N = \(\frac{1}{320 \times 10^{-13}}\)
= 3.125 × 1010 fissions
Number of fissions per second to produce the required power is 3.125 × 1010
Question 10.
Show that the mass of radium with (\({ }_{88}^{226} \mathrm{Ra}\)) an activity of 1 curie is almost a gram. Given T1/2 = 1600 years.
Ans:
Data:
Activity = 1 curie
Half life of Radium = 1600 years
1 curie = 3.7 × 1010 disintegrations per second
From law of disintegration,
N = \(\frac{3.7 \times 10^{10}}{0.6931}\) × 1600 × 365 × 24 × 60 × 60
= \(\frac{1.8669}{0.6931}\) × 1021
= 2.6936 × 1021
According to Avagadro’s principle,
6.023 × 1023 atoms = 226 gm of radium
\(\frac{\mathrm{d} \mathrm{N}}{\mathrm{dt}}\) = λN
N = \(\frac{\mathrm{d} \mathrm{N}}{\mathrm{dt}}\) \(\frac{1}{\lambda}\)
\(\frac{\mathrm{d} \mathrm{N}}{\mathrm{dt}}\) = 1 Curie
= 3.7 × 1010 disintegration per second
λ = \(\frac{0.6931}{\mathrm{~T}_{1 / 2}}\) per year
λ = \(\frac{0.6931}{1600 \times 365 \times 24 \times 60 \times 60}\) Per second × 2.6936 × 1021 atoms
= \(\frac{226}{6.023 \times 10^{23}}\) × 2.6936 × 1021
= 101.0715 × 10-2 g
= 1.0107 gram
The activity of 1 curie of 1 gram of radium is approximately 1 gram.
![]()
Question 11.
Characol pieces of tree is found from an archeological site. The carbon-14 content of this characol is only 17.5% that of equivalent sample of carbon from a living tree. What is the age of tree?
Answer:
Data:
activity R = 17.5%
T1/2 = 5730 yr
The activity of the sample R = R0 e-λt
e-λt = R0/R
By taking the algorithm on bothsides, we get
t = \(\frac{1}{\lambda} \ln \left(\frac{\mathrm{R}}{\mathrm{R}_{\mathrm{O}}}\right)\)
T1/2 = \(\frac{1 \mathrm{n} 2}{\lambda}\)
t = \(\frac{\mathrm{T}_{1 / 2}}{\ln 2} \ln \left(\frac{\mathrm{R}}{\mathrm{R}_{\mathrm{O}}}\right)\)
t = \(\frac{5730}{1 \mathrm{n} 2} \ln \left(\frac{1}{0.175}\right)\) = 14,400 yr
t = 1.44 × 104 yr
Part – II:
12th Physics Guide Atomic and Nuclear Physics Additional Questions and Answers
I. Match the following:
Question 1.
In J.J Thomson’s experiment.
| Field | e/m |
| 1. Electric | a. 1/2V E2/B2 |
| 2. Magnetic | b. 2yE/Cl2B2 |
| 3. Electric and magnetic | c. E/B2R |
| 4. No | d. Not defined |
Answer:
- b
- c
- a
- d
Question 2.
In Millikan’s oil drop experiment
| Force | Formula |
| 1. gravitational force (Fg) | a. σ (4/3 πr3)g |
| 2. Electric force (Fe) | b. ρ(4/3 πr3)g |
| 3. Buoyant force (Fb) | c. 6πηrυ |
| 4. Viscous force (FV) | d. qE (d) |
Answer:
- b
- d
- a
- c
Question 3.
| I | II |
| 1. Electron | a. E. Goldstein |
| 2. Proton | b. Ruther ford |
| 3. Neutron | c. James Chadwick |
| 4. Atomic nucleus | d. J.J Thomson |
Answer:
- d
- a
- c
- b
Question 4.
| I | II |
| 1. Canal rays consist of Postively charged particles protons | a. Ruther ford |
| 2. Electrons are distributed in shells | b. J. J. Thomson |
| 3. Centre of an atom is dense | c. J. Dalton |
| 4. Atom is indivisble | d. Neil Bohr |
Answer:
- b
- d
- a
- c
Question 5.
| I | II |
| 1. Deuterium | a. Radio carbon Dating |
| 2. Carbon 14 | b. Treatment of cancer |
| 3. Isotope of Uranium | c. Nuclear reactors |
| 4. Cobalt 60 | d. An isotope of hydrogen |
Answer:
- d
- a
- c
- b
![]()
II. Choose the odd man out:
Question 1.
a) J.J .Thomson
b) Ruther ford
c) Bohr
d) Millikan
Answer:
d) Millikan
Reason:
Milikan – Charge of an electron, others – Atom models
Question 2.
a) \(\frac{E^{2}}{2 V B^{2}}\)
b) \(\frac{2 y E}{C^{2} B^{2}}\)
c) \(\frac{E}{B^{2} R}\)
d) \(\mathrm{E} / \mathrm{B}\)
Answer:
d) \(\mathrm{E} / \mathrm{B}\)
Reason:
\(\mathrm{E} / \mathrm{B}\) – velocity,
others – Specific charge
Question 3.
a) \(\frac{m e^{4} z^{2}}{8 \varepsilon_{0}^{2} h^{2} n^{2}}\)
b) \(\frac{-m e^{4} z^{2}}{8 \varepsilon_{n}^{2} h^{2} n^{2}}\)
c) \(\frac{-m e^{4} z^{2}}{4 \varepsilon_{0}^{2} h^{2} n^{2}}\)
d) \(\frac{n^{4} h^{2} \varepsilon 0}{\pi m e^{2} Z}\)
Answer:
d) \(\frac{n^{4} h^{2} \varepsilon 0}{\pi m e^{2} Z}\)
Reason:
d) \(\frac{n^{4} h^{2} \varepsilon 0}{\pi m e^{2} Z}\) – radius of nth orbit,
others – Energy of an electron in the nth orbit
Question 4.
a) 10.2 eV
b) 12.1 eV
c) 12.75 eV
d) 13.6 eV
Answer:
d) 13.6 eV
Reason:
13.6eV – Ionization energy, Others – Excitation energy
![]()
Question 5.
a) Lyman
b) Paschen
c) Brackett
d) Pfund
Answer:
a) Lyman
Reason:
Lyman – UV region, others – IR region
Question 6.
a) \({ }_{1} \mathrm{H}^{1}{ }_{1} \mathrm{H}^{2}\)
b) \({ }_{1} \mathrm{H}^{1}{ }_{1} \mathrm{H}^{3}\)
c) \({ }_{3}^{6} \mathrm{Li},{ }_{3}^{7} \mathrm{Li}\)
d) \({ }_{1}^{3} \mathrm{H},{ }_{2}^{3} \mathrm{He}\)
Answer:
d) \({ }_{1}^{3} \mathrm{H},{ }_{2}^{3} \mathrm{He}\)
Reason:
Millikan – charge of an electron
Question 7.
a) \({ }_{17}^{37} \mathrm{Cl},{ }_{16}^{37} \mathrm{~S}\)
b) \({ }_{20}^{40} \mathrm{Ca},{ }_{18}^{40} \mathrm{Ar}\)
c) \({ }_{19}^{40} \mathrm{~K},{ }_{20}^{40} \mathrm{Ca}\)
d) \({ }_{19}^{12} \mathrm{~B},{ }_{6}^{13} \mathrm{C}\)
Answer:
d) \({ }_{19}^{12} \mathrm{~B},{ }_{6}^{13} \mathrm{C}\)
Reason:
\({ }_{19}^{12} \mathrm{~B},{ }_{6}^{13} \mathrm{C}\) – Isotones, others – Isobars
Question 8.
a) Water
b) Heavy water
c) graphite
d) Liquid sodium
Answer:
d) Liquid sodium
Reason
liquid sodium – Cooling system, Others – Moderators.
Question 9.
a) Gravitational force
b) Electromagnetic force
c) Centripetal force
d) nuclear force
Answer:
c) Centripetal force
Reason:
Centripetal force – It is not fundamental, Others – Fundamental forces of nature.
![]()
III. Choose the incorrect pair:
Question 1.
a) 110 mm of Hg – No discharge
b) 100mm of Hg – Crackling sound
c) 10 mm of Hg – Cathode rays
d) 0.01mm of Hg – Crooke’s dark space
Answer:
c) 10mm of Hg – Cathode rays
Reason:
10 mm of Hg – Positive column
Question 2.
a) e/m – 1.7 × 1011 C kg-1
b) e – 1.6 × 10-19 C
c) R – 1.09737 × 10-7 m-1
d) R0 – 6.97 × 10-15 m
Answer:
d) R0 – 6.97 × 10-15 m
Reason:
R0 – 1.2 × 10-15 m (or) 1.2 F
Question 3.
a) \({ }_{5}^{12} \mathrm{~B},{ }_{6}^{13} \mathrm{C}\) – Isotones
b) \({ }_{16}^{40} 5,{ }_{17}^{40} \mathrm{C}\) – Isobars
c) \({ }_{6}^{11} \mathrm{C},{ }_{6}^{12} \mathrm{C}\) – Isotopes
d) \({ }_{6}^{14} \mathrm{C},{ }_{6}^{11} \mathrm{C}\) – Radio isotopes
Answer:
d) \({ }_{6}^{14} \mathrm{C},{ }_{6}^{11} \mathrm{C}\) – Radio isotopes
Reason:
\({ }_{6}^{14} \mathrm{C}\) – Radio isotopes
\({ }_{6}^{11} \mathrm{C}\) – It is not Radio isotopes
Question 4.
a) Nuclear reactor fuel – Plutonium
b) Control rods – Aluminum
c) Cooling system – Ordinary water
d) Moderators – Ordinary water
Answer:
b) Control rods – Aluminum
Reason:
Control rods – Cadmium
![]()
IV. Choose the correct Pair:
Question 1.
a) BE/A of \({ }_{2}^{4} \mathrm{He}\) – 28 MeV
b) BE of \({ }_{2}^{4} \mathrm{He}\) – 7 MeV
c) BE/A of \({ }_{26}^{56} \mathrm{Fe}\) – 8.8 MeV
d) 56 BE of \({ }_{26}^{56} \mathrm{Fe}\) – 470 MeV
Answer:
c) BE/A of \({ }_{26}^{56} \mathrm{Fe}\) – 8.8 MeV
Reason:
c) BE/A of \({ }_{26}^{56} \mathrm{Fe}\) – 8.8 MeV
Question 2.
a) \({ }_{Z}^{\mathrm{A}} \mathrm{X}\) → \(\begin{array}{c}
\mathrm{A}-4 \\
\mathrm{y} \\
\mathrm{Z}-2
\end{array}\) + \({ }_{2}^{4} \mathrm{He}\)
b) \({ }_{Z}^{\mathrm{A}} \mathrm{X}\) → \(\begin{array}{c}
\mathrm{A} \\
\mathrm{y} \\
\mathrm{Z}-1
\end{array}\) + e+ + \(\bar{v}\)
c) \({ }_{Z}^{\mathrm{A}} \mathrm{X}\) → \(\begin{array}{c}
\mathrm{A} \\
\mathrm{Z}+1
\end{array} \mathrm{Y}\) + e– + ν
d) \({ }_{Z}^{\mathrm{A}} \mathrm{X}\) → \(\begin{array}{c}
\mathrm{A} \\
\mathrm{Z}+1
\end{array} \mathrm{Y}\) + γ
Answer:
a) \({ }_{Z}^{\mathrm{A}} \mathrm{X}\) → \(\begin{array}{c}
\mathrm{A}-4 \\
\mathrm{y} \\
\mathrm{Z}-2
\end{array}\) + \({ }_{2}^{4} \mathrm{He}\)
Reason:
a) \({ }_{Z}^{\mathrm{A}} \mathrm{X}\) → \(\begin{array}{c}
\mathrm{A}-4 \\
\mathrm{y} \\
\mathrm{Z}-2
\end{array}\) + \({ }_{2}^{4} \mathrm{He}\) – α – decay
Question 3.
a) C – 14 – 5730 years
b) Neutron – 14 Minutes
c) Phosphorous – 4 minutes
d) Nitrogen – 10.7 minutes
Answer:
a) C – 14 – 5730 years
Reason:
C – 14 – 5730 years (Half life period)
Question 4.
a) 60Co – Thyroid gland
b) 24Na – Treatment of cancer
c) 56Fe – Diagnose anaemia
d) 32p – Locate brain tumors
Ans :
c) 56Fe – diagnose anaemia
Reason:
56Fe – diagnose anaemia.
![]()
V. Assertion and Reason:
Question 1.
Assertion:
Density of all the the nuclei is same.
Reason:
Radius of nucleus is directly proportional to the cube root of mass number.
a) If both assertion and reason are true and the reason is the correct explanation of the reason.
b) If both assertion and reason are true but reason is not the correct explanation of the assertion.
c) If assertion is true but reason is false.
d) If both assertion and reason are false
Answer:
a) If both assertion and reason are true and the reason is the correct explanation of the reason
Solution:
R = Ro A1/3 R α A1/3
Question 2.
Assertion:
For the scattering of a α particles at a large angles, only the nucleus of the atom is responsible.
Reason:
Nucleus is very heavy in comparison to electrons.
a) If both assertion and reason are true and the reason is the correct explanation of the reason.
b) If both assertion and reason are true but reason is not the correct explanation of the assertion.
c) If assertion is true but reason is false.
d) If both assertion and reason are false
Answer:
a) If both assertion and reason are true and the reason is the correct explanation of the reason
Solution:
We know that an electron is very light particle as compared to an a particle. Hence electron cannot scatter, the α particles scatters at large angles, according to law of conservation of energy.
Question 3.
Assertion:
Bohr had to postulate that the electrons in stationary orbits around the nucleus do not radiate.
Reason:
According to classical physics all moving electrons radiate.
a) If both assertion and reason are true and the reason is the correct explanation of the reason.
b) If both assertion and reason are true but reason is not the correct explanation of the assertion.
e) If assertion is true but reason is false.
d) If both assertion and reason are false
Answer:
b) If both assertion and reason are true but reason is not the correct explanation of the assertion.
Solution:
An atom radiates energy, only when electron jumps from a stationary orbit of higher energy to an orbit of lower energy.
Question 4.
Assertion:
Radioactive nuclei emit β-1 particles.
Reason:
Electrons exist inside the nucleus
a) If both assertion and reason are true and the reason is the correct explanation of the reason.
b) If both assertion and reason are true but reason is not the correct explanation of the assertion.
c) If assertion is true but reason is false.
d) If both assertion and reason are false
Answer:
c) If assertion is true but reason is false.
Solution:
So electrons do not exist in the nucleus, [n—> p + e-1 + \(\bar{v}\)]
![]()
VI. Choose the correct statement:
Question 1.
Which of the following statements is correct for cathode rays?
a) They are not deflected by electric and magnetic fields.
b) Cathode rays possess energy and momentum
c) When the cathode rays are allowed to fall on matter, they does not produce heat.
d) The speed of cathode rays is up to \(\left(\frac{1}{20}\right) \mathrm{th}\) of the speed of light
Answer:
b) Cathode rays possess energy and momentum
Solution:
It can be deflected by application of electric and magnetic fields. They produce heat. The \(\left(\frac{1}{10}\right) \mathrm{th}\) of the speed of light
Question 2.
Which of the following statement is correct for isotopes.
a) Same number of neutrons
b) Same number of mass number
c) Same atomic number
d) Same number of electrons
Answer:
c) Same atomic number
Solution:
Same number of protons, same atomic number, different number of neutrons different mass number.
Question 3.
Which of the following statement is correct for an alpha decay.
a) When stable nuclei decay by emitting an α particle
b) It gains two electrons and two neutrons
c) \({ }_{88}^{226} \mathrm{Ra}\) → \({ }_{86}^{222} \mathrm{Ra}\) + \({ }_{2}^{4} \mathrm{He}\)
d) It does not emit four seperate nucleons.
Answer:
c) \({ }_{88}^{226} \mathrm{Ra}\) → \({ }_{86}^{222} \mathrm{Ra}\) + \({ }_{2}^{4} \mathrm{He}\)
Solution:
Unstable nuclei, it loses two protons and two neutrons, and It does not emit four separate nucleons.
Question 4.
Which of the following statement is correct for neutrons.
a) Neutrons are unstable inside the nucleus
b) Neutrons are stable outside the nucleus
c) Those radiations are electromagnetic waves
d) \({ }_{4}^{9} \mathrm{Be}+{ }_{2}^{4} \mathrm{He} \rightarrow{ }_{6}^{12} \mathrm{C}+{ }_{0}^{1} \mathrm{n}\)
Answer:
d) \({ }_{4}^{9} \mathrm{Be}+{ }_{2}^{4} \mathrm{He} \rightarrow{ }_{6}^{12} \mathrm{C}+{ }_{0}^{1} \mathrm{n}\)
Solution:
Neutrons are stable inside the nucleus. But outside the nucleus they are unstable. Those radiations are not em waves but they are particles.
![]()
VII. Choose the incorrect statements:
Question 1.
Which of the following statements are incorrect for fine structure constant α
a) α = Velocity of an electron in the first orbit / The speed of light
b) α = e2/2ε0 hc
c) \(\frac{\mathrm{V}_{1}}{\mathrm{C}}=\frac{1}{137}\)
d) α is dimension number
Answer:
d) α is dimension number
Solution:
α is a dimensionless number
Question 2.
Which of the following statements are incorrect for Bohr atom model.
a) Bohr atom model is valid only for hydrogen atom.
b) Fine structure is explained by Bohr atom model.
c) Bohr atom model fails to explain the intensity variations in the spectral lines.
d) The distribution of electrons in atoms is not completely explained by Bohr atom model.
Answer:
b) Fine structure is explained by Bohr atom model.
Solution:
Fine structure is not explained by Bohr atom model.
Question 3.
Which of the following statements are incorrect for decay.
a) α – decay: atomic number z decreases by 2, mass number decreases by 4.
b) β – decay: atomic number z increases by one and the mass number remains the same.
c) γ – decay: no change in the mass number or atomic number of the nucleus.
d) Both α and β particles are emitted during a single decay.
Answer:
d) Both α and β particles are emitted during a single decay.
Solution:
Both α and β particles are not emitted during a single decay.
Question 4.
Which of the following statements are incorrect for elementary particles.
a) The study of elementary particles is called particle physics.
b) Electrons are not elementary particles.
c) Charge of up quark is + 2/3e
d) Charge of down quark is -1/3e
Answer:
b) Electrons are not elementary particles.
Solution:
Electrons are fundamental particles because they are not made up of anything.
![]()
VIII. Choose the best answer:
Question 1.
The potential difference applied to an X-ray tube is 5 kV and the current through it is 3.2 mA. Then the number of electrons striking the target per second is
(a) 2 x 1016
(b) 5 x 1018
(c) 1 x 1017
(d) 4 x 105
Answer:
(a) 2 x 1016
Hint:
n = \(\frac { It }{ e }\) = \(\frac{3.2 \times 10^{-3} \times 1}{1.6 \times 10^{-19}}\) = 2 x 1016.
Question 2.
Proton Carries _______.
a) a positive charge
b) a negative charge
c) No charge
d) None of these
Answer:
a) a positive charge
Question 3.
The radioisotope used for locating brain tumours is ________.
a) Phosphor
b) Potassium
c) Iodine
d) Sodium
Answer:
c) Iodine
Question 4.
The speed of the particle, that can take discrete values is proportional to
(a) n-3/2
(b) n-1
(c) n1/2
(d) n
Answer:
(d) n
Hint:
P = mv = \(\frac { nh }{ 2a }\) ; V ∝ n.
Question 5.
Which of these four elements are essential for the construction of nuclear reactors?
a) Cobalt
b) Nickel
c) Zirconium
d) Tungsten
Answer:
C) Zirconium
![]()
Question 6.
The nuclei have mass numbers in the ratio 1 : 8. find the ratio of their nuclei radii.
a) 1 : 8
b) 1 : 2
c) 2 : 1
d) 8 : 1
Answer:
b)1 : 2
Question 7.
The source of the sun’s energy is _______.
a) Fission
b) Radioactivity
c) Fusion
d) Ionization
Answer:
c) Fusion
Question 8.
Energy required for the electron excitation in Li++ from the first to the third Bohr orbit is
(a) 12.1 eV
(b) 36.3 eV
(b) 36.3 eV
(c) 108.8 eV
Answer:
(c) 108.8 eV
Hint:
En = – 13.6 \(\frac { { Z }^{ 2 } }{ { n }^{ 2 } } \)
∆E = E3 – E2 = 13.6 (3)2 \(\left[ \frac { 1 }{ { 1 }^{ 2 } } -\frac { 1 }{ { 3 }^{ 2 } } \right] \)
= \(\frac { 13.6×9×8 }{ 9 } \) = 108.8 eV.
Question 9.
Which of the following transition will have the highest emission wavelength.
a) n = 2 to n = 1
b) n = 4 to n = 1
c) n = 6 to n = 2
d) n = 5 to n = 2
Answer:
d) n = 5 to n = 2
Question 10.
One atomic mass unit (u) =
a) 1.660 × 10-27 kg
b) 1.660 × 10-20 kg
e) 1.660 × 10-24 kg
d) 1.660 × 10-22 kg
Answer:
a) 1.660 × 10-27 kg
![]()
Question 11.
\(\frac{12}{5} \mathrm{~B} \rightarrow \frac{12}{6} \mathrm{C}+\ldots \ldots \bar{v}\)
a) e–
b) e+
c) γ
d) None of these
Answer:
a) e–
Question 12.
For an electron in the second orbit of hydrogen, what is the moment of momentum as per Bohr’s model?
(a) 2πh
(b) πh
(c) h / π
(d) 2h / π
Answer:
(c) h / π
Hint:
In second orbit of hydrogen, L = 2 \(\left( \frac { h }{ 2\pi } \right) \) = \(\frac { h }{ π }\).
Question 13.
1 curie = ________ Bq
a) 3.7 × 1010
b) 3.7 × 10-10
c) 3.8 × 10-10
d) 3.8 × 1010
Answer:
a) 3.7 × 1010
Question 14.
The mean life of \({ }_{0}^{1} \mathrm{n}\) is
a) 18.75 minutes
b) 8.11 minutes
c) 13 minutes
d) 10 minutes
Answer:
a) 18.75 minutes
Question 15.
A beam of cathode rays is subjected to crossed Electric (E) and magnetic fields. (B). This fields are adjusted such that the beam is not deflected. The specific charge of the cathode rays is given by
a) \(\mathrm{E}^{2} / 2 \mathrm{VB}^{2}\)
b) \(\mathrm{B}^{2} / 2 \mathrm{VE}^{2}\)
c) \(\frac{2 \mathrm{VB}^{2}}{\mathrm{E}^{2}}\)
d) \(\frac{2 V E^{2}}{B^{2}}\)
Answer:
a) \(\mathrm{E}^{2} / 2 \mathrm{VB}^{2}\)
Solution:
eV = 1/2 mv2
e/m = \(\frac{v^{2}}{2 V}\)
∴ V = E/B
\(\frac{e}{m}=\frac{E^{2}}{2 V B^{2}}\)
![]()
Question 16.
The specific charge of an electron is ________.
a) 1.6 × 10-19 C/kg
b) 4.8 × 10-10 C/kg
c) 1.76 × 1011 C/kg
d) 1.76 × 10-11 C/kg
Answer:
c) 1.76 × 1011 C/kg
Solution:
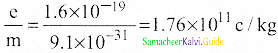
Question 17.
The ratio of specific charge of an α – particle to that of a proton is
a) 2 : 1
b) 1 : 1
c) 1 : 2
d) 1 : 3
Answer:
c) 1 : 2
Solution:
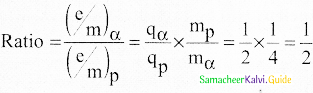
Question 18.
A narrow electron beam passes undeviated through an electric field E = 3 × 104 v/m and an overlapping magnetic field B = 2 × 10-3 wb/m2. The electron motion, electric field and magnetic field are mutually perpendicular. The speed of the electron is _______.
a) 60 m/s
b) 10.3 × 107 m/s
c) 1.5 × 107 m/s
d) 0.67 × 10-7 m/s
Answer:
c) 1.5 × 107 m/s
Solution:
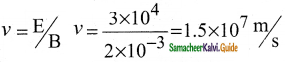
Question 19.
In Bohr’s model of hydrogen atom, the radius of the first electron orbit is 0.53 Å. What will be the radius of the third orbit?
(a) 4.77 Å
(b) 47.7 Å
(c) 9 Å
(d) 0.09 Å
Answer:
(a) 4.77 Å
Hint:
r3 = (3)2 r1 = 9 x 0.53 = 4.77 Å.
Question 20.
In millikan’s oil drop experiment, an oil drop of mass 16 × 10-6 Kg is balanced by an electric field of 106 v/m. The charge in coulomb on the drop, assuming g = 10 m/s2 is
a) 6.2 × 10-11
b) 16 × 10-19
c) 16 × 10-11
d) 16 × 10-13
Answer:
c) 16 × 10-11
Solution:
eE = mg
e = mg/E
= \(\frac{16 \times 10^{-6} \times 10}{10^{6}}\)
= 16 × 10-11 C
![]()
Question 21.
An alpha nucleus of energy 1/2 mv2 bombards a heavy target of charge Ze. Then, the distance of closest approach for the alpha nucleus will be proportional to
a) V2
b) 1/m
c) 1/V4
d) 1/Ze
Answer:
b) 1/m
Solution:
r0 = \(\frac{1}{4 \pi \varepsilon_{\mathrm{o}}} \frac{2 \mathrm{ze}^{2}}{1 / 2 \mathrm{mv}^{2}}\)
i.e, r α \(\frac{1}{\mathrm{~m}}\)
Question 22.
An α – particle is projected with an energy of 4 MeV directly towards gold nucleus. Calculate the distance of its closest approach, (gold z = 79)
a) 5.688 × 10-14 m
b) 7.699 × 10-14 m
c) 5.688 × 10-14m
d) 7.699 × 10-14 m
Answer:
a) 5.688 × 10-14 m
Solution :
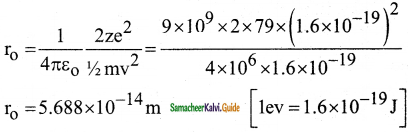
Question 23.
In terms of Bohr radius a0, the radius of the second Bohr orbit of a hydrogen atom is given by
(a) 4a0
(b) 8a0
(c) √2a0
(d) 2a0
Answer:
(a) 4a0
Hint:
rn = r1 n2
r2 = a0 (2)2 =4a0
Question 24.
The hydrogen atom in the ground state is excited by monochromatic radiation of a wavelength of λ = 975 Å. The number of spectral lines in the resulting spectrum emitted will be:
a) 10
b) 6
c) 3
d) 2
Answer:
b) 6
Question 25.
One femtometre is equivalent to
(a) 1015 m
(b) 10-15 m
(c) 10-12 m
(d) 1011 m
Answer:
(b) 10-15 m
![]()
Question 26.
The ratio of the kinetic energy to the total energy of an electron in a Bohr orbit of the hydrogen
a) 1 : -2
b) 1 : -1
c) 1 : 1
d) 2 : 1
Answer:
b) 1 : -1
Solution :
KE = – (TE);
KE/TE = -1
Question 27.
In the spectrum of hydrogen, the ratio of the longest wavelength in the lyman series to the longest wavelength in Balmer series is
a) 9/4
b) 27/5
c) 5/27
d) 4/9
Answer:
c) 5/27
Solution:
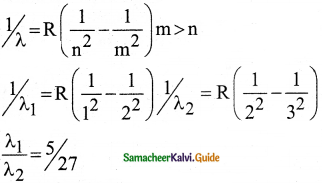
Question 28.
The radius of the 5th orbit of a hydrogen atom is 13.25. Calculate the wavelength of the electron in the 5th orbit.
a) λ = 16.64 Å
b) λ = 26.5O Å
c) λ = 13.25 Å
d) λ = 13.64 Å
Answer:
a) λ = 16.64 Å
Question 29.
What would be the radius of the second orbit of He+ ions?
(a) 1.058 Å
(b) 3.023 Å
(c) 2.068 Å
(d) 4.458 Å
Answer:
1.058 Å
Hint:
rn = \(\frac {{ n }^{2}}{ Z }\) r1
For He+ ion, n = 2, Z = 2
∴ r2 = \(\frac {4}{ 2 }\) x 0.59 Å = 1.058 Å.
Question 30.
The first excitation potential to a given atom is 10.2 V. Then ionisation potential must be
a) 20.4 V
b) 13.6 V
e) 30.6 V
d) 40.8 V
Answer:
b) 13.6V
Solution:
First excitation potential energy E2 – E1 = 10.2eV
E1 = -13.6 eV
Ionisation potential energy,
E∞ – E1 = 0 + 13.6 = 13.6 eV
Ionisation potential = 1/e
Eionization = 13.6 V
![]()
Question 31.
Hydrogen atom excites energy level from fundamental state to n = 3. Number of spectral lines according to Bohr is _______.
a) 4
b) 3
c) 1
d) 2
Answer:
b) 3
Solution:
\(\frac{\mathrm{n}(\mathrm{n}-1)}{2}\) = \(\frac{3(3-1)}{2}\) = 3
Question 32.
What would be the radius of second orbit of He+ ion?
a) 1.058 Å
b) 3.023 Å
e) 2.068 Å
d) 4.458 Å
Answer:
a) 1.058 Å
Solution :
rn = a0 \(\frac{n^{2}}{z}\) for He+ ion
Z = 2, n = 2, a0 = 0.529 Å
r2 = 0.529 Å (4/2) = 1.058 Å
Question 33.
The size of an atom is proportional to
(a) A
(b) A1/3
(c) A2/3
(d) A-1/3
Answer:
(b) A1/3
Question 34.
Energy levels A, B, C of a certain atom correspond to increasing values of energy. (j.c) EA < EB < Ec. ?2 )3 arc in the wavelengths C to B, B to A, and C to A respectively, which of the following statements is correct.
a) λ3 = λ1 + λ2
b) λ3 = \(\frac{\lambda_{1} \lambda_{2}}{\lambda_{1}+\lambda_{2}}\)
c) λ1 = λ2 + λ3
d) λ32 = λ12 + λ22
Answer:
b) λ3 = \(\frac{\lambda_{1} \lambda_{2}}{\lambda_{1}+\lambda_{2}}\)
Solution:
(EC – EA) = (EC – EB) + (EB – EA)
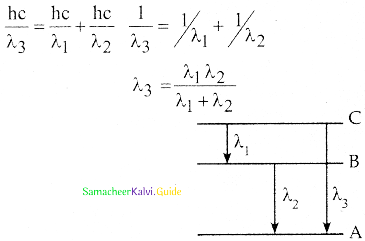
Question 35.
If in nuclear fusion process, the masses of the fusing nuclei be m1 and m2 and the mass of the resultant is m1, then
a) m3 = m1 + m2
b) m3 = m1 – m2
c) m3 < m1 + m2
d) m3 > m1 + m2
Answer:
c) m3 < m1 + m2
![]()
Question 36.
The nuclear radius of \(\begin{array}{l}
8 \\
4
\end{array} \text { Be }\) nucleus is
a) 1.3 × 10-15 m
b) 2.4 × 10-15 m
c) 1.3 × 10-13 m
d) 2.4 × 10-10 m
Answer:
b) 2.4 × 10-15 m
Solution:
R = R0 A1/3
R = 1.2 × 10-15 × 81/3
R = 1.2 × 10-15 × (23)1/3
R = 2.4 × 10-15 e
Question 37.
The mass defect of a \({ }_{3}^{7} \mathrm{Li}\) is 0.042u. Its binding energy per nucleon is
a) 23 MeV
b) 46 MeV
c) 5.6 MeV
d) 3.9 MeV
Answer:
c) 5.6 MeV
Solution:
\(\frac{\mathrm{BE}}{\mathrm{A}}\) = \(\frac{0.042 \times 931 \mathrm{MeV}}{7}\) = 5.6 MeV
Question 38.
The mass defect of a certain nucleus is found to be 0.03u. Its binding energy is _______.
a) 27.93 eV
b) 27.93 KeV
e) 27.93 MeV
d) 27.93 GeV
Answer:
c) 27.93 MeV
Solution:
BE = 0.03 × 931 MeV = 27.93 MeV
Question 39.
The SI unit of radioactivity is _______.
a) Roentgen
b) Rutherford
c) Curie
d) Becquerel
Answer:
d) Becquerel
![]()
Question 40.
Radioactive material A has decay constant 8λ and material B has decay constant λ. Initially they have same number of nuclei. After what time, the ratio of number of nuclei of material B to that A will be 1/e
a) 1/λ
b) 1/7λ
c) 1/8λ
d) 1/9λ
Answer:
b) 1/7λ
Solution:
NA = N0 e-8λt,
NB = N0 e-λt
\(\frac{\mathrm{N}_{\mathrm{A}}}{\mathrm{N}_{\mathrm{B}}}\) = \(\frac{\mathrm{e}^{-8 \lambda t}}{\mathrm{e}^{-\lambda \mathrm{t}}}\) \(\frac{1}{\mathrm{e}}\)
= e-7λt e-1 = e-λt
= 7λt = 1
t = 1/7λ
Question 41.
If a radioactive substance to 1/16 of its original mass in 40 days, what is its half life
a) 10 days
b) 20 days
c) 40 days
d) None of these
Answer:
a) 10 days
Solution:
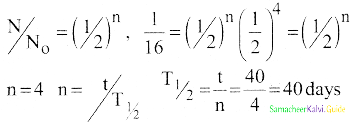
Question 42.
The explosion of atom bomb is based on the principle of _______.
a) uncontrolled fission reaction
b) controlled fission reaction
e) fusion reaction
d) Thermonuclear reaction
Answer:
a) uncontrolled fission reaction
Question 43.
The average energy released per fission is _______.
a) 200 eV
b) 200 MeV
c) 200 GeV
d) 200 MeV
Answer:
b)200 MeV
Solution:
Energy released in fission = 200 MeV
Question 44.
In Bohr Atom model when the principal quantum number (n) increases the velocity of electron ________.
a) increases and then decreases
b) increases
c) decreases
d) remains constant
Answer:
c) decreases
![]()
IX. Two Marks Questions:
Question 1.
Define excitation potential.
Answer:
Excitation potential is defined as excitation energy per unit charge.
Question 2.
Why gas is a poor conductor of electricity?
Answer:
Gases at normal atmospheric pressure are poor conductors of electricity because they do not have free electrons for conduction.
Question 3.
What phenomenon occurs at a pressure of 100mm of Hg in the discharge tube?
Answer:
- When the pressure is kept near 100mm of Hg, the discharge of electricity through the tube takes place.
- Consequently, irregular streaks of light appear and also crackling sound is produced. 10. State Earnshaw’s theorem.
Question 4.
What is known as positive column?
Answer:
When the pressure is reduced to the order of 10mm of Hg, a luminous column known as positive column is formed from anode to cathode.
Question 5.
What is called crooke’s dark space?
Answer:
When the pressure reaches to around 0.01 mm of Hg, positive column disappears. At this time, a dark space is formed between anode and cathode which is often called crooke’s dark space.
![]()
Question 6.
Write the principle of JJ Thomson’s experiment?
Answer:
In the presence of electric and magnetic fields, the cathode rays are deflected.
Question 7.
The e/m ratio of cathode does not depend on?
Answer:
The specific charge is independent of
- gas used
- nature of the electrodes.
Question 6.
Write down the properties of the neutrino.
Answer:
The neutrino has the following properties:
- It has zero charge
- It has an antiparticle called anti-neutrino.
- Recent experiments showed that the neutrino has a very tiny mass.
- It interacts very weakly with the matter. Therefore, it is very difficult to detect.
- In fact, in every second, trillions of neutrinos coming from the sun are passing through our bodies without any interaction.
Question 9.
Why Thomson’s model of the atom is known as a watermelon model?
Answer:
This is because in Thomson’s model the electrons are assumed to be uniformly embedded in a sphere of positively charged matter like seeds in watermelon.
Question 10.
State Earnshaw’s theorem.
Answer:
From classical electrodynamics, no stable equilibrium points exist in electrostatic configuration.
![]()
Question 11.
What is Thomson’s atom model?
Answer:
- It this model, the atoms are visualized as homogeneous spheres which contain uniform distribution of positively charged particles. The negatively charged patticles known as electrons are embedded in it like seeds in water melon.
- The atoms are electrically neutral, this implies that the total positive charge in an atom is equal to the total negative charge.
Question 12.
What are the drawbacks of Thomson atom model?
Answer:
It fails to explain the origin of spectral lines observed in the spectrum of hydrogen atom and other atoms.
Question 13.
The large angle scattering is possible only due to nucleus. Why?
Answer:
α particles can be scattered through large angles only if they collide against a positively charged heavy particle such as a nucleus.
Question 14.
What is the value of impact parameter for scattering through 180°?
Answer:
b = K cot(θ/2)
θ is called scattering angle, b = K cot 90° = 0
It can be proved that impact parameter is zero, for θ = 180°
Question 15.
State Bohr’s angular momentum quantization condition.
Answer:
The angular momentum of the electron in stationary orbits are quantized that is it can be written as integer or integral multiple of h/2π
l = nh/2π (or) mvr = nh/2π
where
n = principal quantum number of the orbit.
h/2π = reduced plank’s constant.
![]()
Question 16.
State Bohr’s energy quantization condition.
Answer:
An electron can jump from one orbit to another orbit by absorbing or emitting a photon whose energy is equal between the two orbital levels.
∆E = Efinal – Einitial = hν = hc/λ
C = speed of light, λ = wavelength of the radiation, ν = frequency of the radiation
Question 17.
Define wave number of radiation. Give its unit
Answer:
\(\bar{v}=\frac{1}{\lambda}\)
where \(\bar{v}\) is known as wave number which is inverse of wavelength.
unit: m-1
Question 18.
What are stationary orbits?
Answer:
- Electrons in an atom revolve around the nucleus only in certain discrete orbits called stationary orbits where it does not radiate electromagnetic energy.
- Only those discrete orbits allowed are stable orbits.
Question 19.
What is a velocity selector?
Answer:
- The velocity selector allows the long of a particular velocity to come out of it, by the combined action of electric and a magnetic field. “
- Force due to electric field = Force due to magnetic field
eE = eBV
V = E/B
Question 20.
How much is the energy possessed by an electron for n = ∞?
Answer:
For n = ∞,
En = –\(\frac{13.6}{\mathrm{n}^{2}}\) ev = 0
![]()
Question 21.
What is atomic mass unit (u)?
Answer:
One atomic mass unit (u) is defined as the 1/12 th of the mass of the isotope of carbon \({ }_{6}^{12} \mathrm{C}\)
1u = \(\frac{\text { mass of }_{6}^{12} \text { Catom }}{12}\)
= \(\frac{1.992 \times 10^{-26}}{12}\)
lu = 1.660 × 10-27 kg
Question 22.
State empirical formula related to the radius of nucleus and its mass number.
Answer:
The nuclei are found to be approximately spherical in shape. It is experimentally found that the radius of nuclei for Z > 10, satisfies the following empirical formula.
R = R0 A1/3
A = mass number of the nucleus
R0 = 1.2 F
Question 23.
Give the nature of α, β, and γ – radiations.
Answer:
α rays are in fact \({ }_{2}^{4} \mathrm{He}\) nuclei and β rays are electrons or positrons. Certainly, they are not electromagnetic radiation. The γ ray alone is electromagnetic radiation.
Question 24.
What is an α particle?
Answer:
An α particle is a helium nucleus consisting of two protons and two neutrons. It carrier two units of positive charge.
Question 25.
Define decay constant (λ).
Answer:
It is defined as the reciprocal of mean life λ = 1/τ
![]()
Question 26.
What is the half-life of nucleus? Give the expression.
Answer:
The half (T1/2) is defined as the time required for the number of atoms initially present to reduce to one half of the initial amount, T1/2 = 0.6931 τ
Question 27.
Nuclear fusion reactions are also known as thermonuclear reactions. Why?
Answer:
When the surrounding temperature reaches around 107K, lighter nuclei start fusing to form heavier nuclei and this resulting reaction is called thermonuclear fusion reaction.
Question 28.
What is nuclear fission?
Answer:
If a heavier nucleus decays into lighter nuclei, it is called nuclear fission.
Question 29.
What are nuclear fusion?
Answer:
If two lighter nuclei fuse to heavier nuclei, it is called nuclear fusion.
Question 30.
Why is nuclear fusion not possible in a laboratory?
Answer:
Nuclear fusion requires very high temperature of 107 K. So nuclear fusion is not possible in a laboratory.
![]()
X. Three Marks Questions:
Question 1.
What were Rutherford’s conclusions on the atom?
Answer:
1. From the experimental observations, Rutherford proposed that an atom has a lot of empty space and contains a tiny matter known as nucleus whose size is of the order of 10-14 m. The nucleus is positively charged and most of the mass of the atom is concentrated in nucleus.
2. The nucleus is surrounded by negatively charged electrons. Since static charge distribution cannot be in a stable equilibrium, he suggested that the electrons are not at rest and they revolve around the nucleus in circular orbits like planets revolving around the sun.
Instability of atom
Spiral in motion of an electron around the nucleus.
Question 2.
Write down the drawbacks of the Rutherford model.
Answer:
Drawbacks of Rutherford model:
1. Rutherford atom model helps in the calculation of the diameter of the nucleus and also the size of the atom but has the following limitations.
2. This model fails to explain the distribution of electrons around the nucleus and also the stability of the atom.
3. According to classical electrodynamics, any accelerated charge emits electromagnetic radiations. Due to emission of radiations, it loses its energy. Hence, it can no longer sustain the circular motion. The radius of the orbit, therefore, becomes smaller and smaller (undergoes spiral motion) and finally the electron should fall into the nucleus and the atoms should disintegrate. But this does not happen.
4. Hence, Rutherford model could not account for the stability of atoms.
5. According to this model, emission of radiation must be continuous and must give a continuous emission spectrum but experimentally we observe only line (discrete) emission spectrum for atoms.
Question 3.
Obtain the expression for the distance of closest approach based on Rutherford atom model.
Answer:
Distance of closest approach :
1. When an alpha particle moves straight towards the nucleus, it reaches a point where it comes to rest momentarily and returns back.
2. The minimum distance between the centre of the nucleus and the alpha particle just before it gets reflected back through 180° is defined as the distance of closest approach rQ (also known as contact distance).
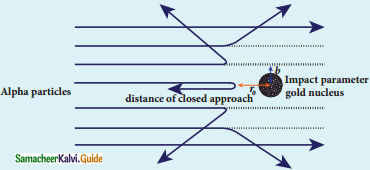
Distance of closest approach and impact parameter
3. At this distance, all the kinetic energy of the alpha particle will be converted into electrostatic potential energy
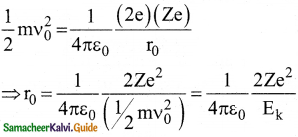
where Ek is the kinetic energy of the alpha particle.
4. This is used to estimate the size of the nucleus but the size of the nucleus is always lesser than the distance of the closest approach.
5. Further, Rutherford calculated the radius of the nucleus for different nuclei and found that it ranges from 10-14 m to 10-15 m.
![]()
Question 4.
Obtain the expression for the impact parameter based on Rutherford atom model.
Answer:
Impact parameter:
1. The impact parameter is defined as the perpendicular distance between the centre of the gold nucleus and the direction of velocity vector of alpha particle when it is at a large distance.
2. The relation between impact parameter and scattering angle can be shown as
b ∝ cot(\(\frac{\theta}{2}\)) ⇒ b = K cot(\(\frac{\theta}{2}\)) …………(1)
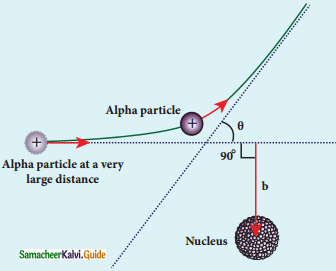
Impact parameter
where K = \(\frac{1}{4 \pi \varepsilon_{0}} \frac{2 \mathrm{Ze}^{2}}{\mathrm{mv}_{0}^{2}}\) and θ is called scattering angle.
3. Equation (1) implies that when impact parameter increases, the scattering angle decreases. Smaller the impact parameter, larger will be the deflection of alpha particles.
Question 5.
Obtain the expression for the velocity of electron in nth orbit.
Answer:
1. Bohr’s angular momentum quantization condition leads to
mυnrn = nh/2π
Variation of velocity of the electron in the orbit with principal quantum number.
For hydrogen atom ( z = 1), the radius of nth orbit is
rn = a0 n2
mυna0n2 = nh/2π
υn = (\(\frac{\mathrm{hz}}{2 \pi \mathrm{ma}_{\mathrm{o}}}\)) \(\frac{1}{n}\)
υn ∝ \(\frac{1}{n}\)
2. The velocity of electron decreases as the principal quantum number increases.
3. This curve is the rectangular hyperbola.
4. This implies that the velocity of electron in ground state is maximum when compared to excited states.
5. Variation of velocity of the electron in the orbit with principal quantum number.
Question 6.
Sketch the energy levels for the hydrogen atoms.
Answer:
1. Horizontal linear are drawn which represent the energy levels of the hydrogen atom.
2. The energy of the electron in the nth orbit of the hydrogen atom is given by, En = –\(\frac{13.6}{\mathrm{n}^{2}}\) eV
3. For the first orbit (ground state), the total energy of electron is E1 = -13.6 eV
4. For the second orbit (first excited state), the total energy of electron is E2 = -3.4 eV
5. For the third orbit (second excited state), the total energy of electron is E3 = -1.51 eV
6. For the fourth orbit (third excited state), the total energy of electron is E4 = -0.85 eV
7. For the fifth orbit (fourth excited state), the total energy of electron is E5 = -0.54 eV and so on.

![]()
Question 7.
What is the significance of the negative energy of electron in the orbit?
Answer:
1. This signifies that the electron is bound to the nucleus.
2. Due to electrostatic attraction between electron and nucleus, the potential energy (PE) is negative and is greater than kinetic energy (KE) of electron.
3.Total energy (TE) of electron is negative. It cannot escape from the atom.
4. Potential energy
Un = –\(\frac{1}{4 \varepsilon_{0}^{2}} \frac{Z^{2} m e^{4}}{h^{2} n^{2}}\) ………….(1)
5. Kinetic energy
KEn = –\(\frac{1}{8 \varepsilon_{\mathrm{o}}^{2}} \frac{\mathrm{Z}^{2} \mathrm{me}^{4}}{\mathrm{~h}^{2} \mathrm{n}^{2}}\) ………..(2)
6. Total energy
En = \(\frac{1}{8 \varepsilon_{0}^{2}} \frac{Z^{2} e^{4} m}{h^{2} n^{2}}\) …………(3)
The negative sign in equation (3) indicates that the electron is bound to the nucleus.
Question 8.
Obtain Bohr’s quantisation condition on the basis of the wave picture of an electron.
Answer:
1. The circumference of an electron’s orbit of radius r must be an integral multiple of de Broglie wavelength – that is,
2πr = n(\(\frac{\mathrm{h}}{\mathrm{mv}}\)) …………(1)
But the de Broglie wavelength (λ) for an electron of mass m moving with velocity ν is
λ = \(\frac{\mathrm{h}}{\mathrm{mv}}\) where h is called Planck’s constant.
Thus from equation (1)
2πr = n(\(\frac{\mathrm{h}}{\mathrm{mv}}\))
mvr = \(\frac{\mathrm{nh}}{27}\)
2. For any particle of mass m undergoing circular motion with radius r and velocity v, the magnitude of angular momentum / is given by l = r (mv)
mvr = l = nh
This is the famous Bohr’s quantisation condition for angular momentum.
Question 9.
What is the value of charge of a neutrino? Although trillions of neutrinos coining from the sun pass throught our body every second, it is very difficult to detect them. Why?
Answer:
1. The neutrino has zero charge.
2. Neutrino interacts very weakly with the matter. In every second, trillions of neutrinos coming from the sun are passing through our body without any interaction.
Question 10.
Is the nuclear density same for all elements?
Answer:
Yes.
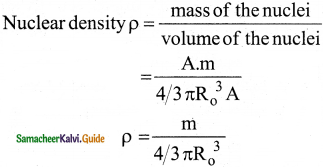
1. The above expression shows that the nuclear density is independent of the mass number A.
2. In other words, all the nuclei (Z > 10) have the same density and it is an important characteristic of the nuclei.
![]()
Question 11.
Why is the mass of a nucleus always less than the sum of the masses of its constituents, neutrons, and protons?
Answer:
- When nucleons approach each other to form a nucleus, they strongly attract each other. Their potential energy decreases and becomes negative.
- It is this potential energy which holds the nucleons together in the nucleus.
- The decrease in potential energy results in a decrease in the mass of the nucleons inside the nucleus.
Question 12.
What do you mean by the charge independent character of nuclear forces?
Answer:
- The strong nuclear force is attractive and acts with an equal strength between proton-proton, proton – neutron, and neutron – neutron
- This shows that nuclear force is not electrostatic in nature. So nuclear force is charge independent.
Question 13.
How are β – rays emitted from a nucleus, when it does not contain electrons?
Answer:
- A neutron of a nucleus decays into a proton, an electron and an antineutrino.
- It is this electron which is emitted as β – particle.
\({ }_{0} \mathrm{n}^{1} \rightarrow{ }_{1} \mathrm{p}^{1}+{ }_{-1} \mathrm{e}^{0}+\overline{\mathrm{v}}\)
Question 14.
Which is more dangerous: radioactive material with a short half-life, or a long half-life?
Answer:
One should not think that shorter half-life material is safer than longer half-life material because it will not last long. The shorter half-life sample will have higher activity and it is more radioactive which is more harmful.
Question 15.
What is radiocarbon dating?
Answer:
- Radiocarbon dating is a method of estimating the age of a dead specimen by calculation the amount C present in the specimen having the half-life of C as 5730 years.
- Since our human body, tree or any living organism continuously absorb CO2 from the atmosphere, the ratio of \({ }_{6}^{14} \mathrm{C}\) to \({ }_{6}^{12} \mathrm{C}\) in the living organism is also nearly constant. But when the organism dies, it stops absorbing CO2.
- Since \({ }_{6}^{14} \mathrm{C}\) starts to decay, the ratio of \({ }_{6}^{14} \mathrm{C}\) to \({ }_{6}^{12} \mathrm{C}\) in a dead specimen decreases over the years.
- Suppose the ratio of \({ }_{6}^{14} \mathrm{C}\) to \({ }_{6}^{12} \mathrm{C}\) in the ancient tree pieces excavated is known, then the age of the tree pieces can be calculated.
![]()
Question 16.
How do you classify the neutrons in terms of their kinetic energy?
Answer:
- Neutrons are classified according to their kinetic energy as
- Slow neutrons – 0 to 1000 eV
- Fast neutrons – 0.5 MeV to 10 MeV
- The neutrons with an average energy of about 0.025 eV in thermal equilibrium are called thermal neutrons because at 298K, the thermal energy KT ~ 0.025 eV. slow and fast neutrons play a vital role in nuclear reactors.
- In nuclear reactors, fast neutrons are converted into slow neutrons using moderators.
Question 17.
What is a chain reaction?
Answer:
Chain reaction:
- When one \({ }_{92}^{235} \mathrm{U}\) nucleus undergoes fission, the energy released might be small.
- But from each fission reaction, three neutrons are released.
- These three neutrons cause further fission in another three \({ }_{92}^{235} \mathrm{U}\) nuclei which in turn produce nine neutrons.
- These nine neutrons initiate fission in another 27 \({ }_{92}^{235} \mathrm{U}\) nuclei and so on.
- This is called a chain reaction and the number of neutrons goes on increasing almost in geometric progression.
Question 18.
What is a controlled and uncontrolled chain reaction?
Answer:
- There are two kinds of chain reactions:
- Uncontrolled chain reaction.
- Controlled chain reaction.
- In an uncontrolled chain reaction, the number of neutrons multiplies indefinitely, and the entire amount of energy released in a fraction of a second.
- The atom bomb is an example of nuclear fission in which an uncontrolled chain reaction occurs.
- In nuclear reactors, the controlled chain reaction is achieved.
Question 19.
What is a nuclear reactor? Mention the uses of nuclear reactors.
Answer:
Nuclear reactor: Nuclear reactor is a system in which nuclear fission takes place in a self-sustained controlled manner.
Uses of nuclear reactors:
- A nuclear reactor is used for power generation.
- A nuclear reactor is used for research purposes.
- A nuclear reactor is useful to produce radioisotopes.
Question 20.
How many nuclear reactors are there in India?
Answer:
India has 22 nuclear reactors in operation. Nuclear reactors are constructed in two places in Tamilnadu, Kalpakkam and Kudankulam. Even though nuclear reactors are aimed to cater to our energy need, in practice nuclear reactors now are able to provide only 2% of energy requirement of India.
![]()
Question 21.
What is the difference between critical and super-critical state?
Answer:
- If the average number of neutrons produced per fission is equal to one, then the reactor is said to be in a critical state.
- In fact, all the nuclear reactors are maintained in a critical state by suitable adjustment of control rods.
- If it is greater than one, then the reactor is said to be supercritical and it may explode sooner or may cause massive destruction to cause another fission and the remaining neutrons are absorbed by the control rods.
- Usually, cadmium or boron acts as control rod material and these rods are inserted into the uranium blocks.
Question 22.
What is the role of control rods in a nuclear reactor?
Answer:
- The control rods are used to adjust the reaction rate.
- During each fission, on average 2.5 neutrons are emitted and in order to have the controlled chain reactions, only one neutron is allowed to cause another fission and the remaining neutrons are absorbed by the control rods.
- Usually cadmium or boron are used as control rod material and these rods are inserted into the uranium blocks.
XI. Five Marks Questions:
Question 1.
How are cathode rays produced in a discharge tube?
Answer:
1. It consists of a long-closed glass tube (of length nearly 50 cm and diameter of 4 cm) inside of which the gas in pure form is filled usually.
2. The small opening in the tube is connected to a high vacuum pump and a low-pressure gauge.
3. This tube is fitted with two metallic plates known as electrodes which are connected to a secondary of an induction coil.
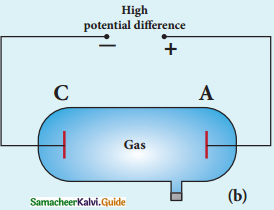
4. The electrode connected to positive of secondary is known as anode and the electrode to the negative of the secondary is cathode.
5. The potential of secondary is maintained at about 50 kV.
6. Suppose the pressure of the gas in discharge tube is reduced to around 110mm of Hg using vaccum pump, it is observed that no discharge takes place.
7. When the pressure is kept near 100 mm of Hg, the discharge of electricity through the tube takes place. Consequently, irregular streaks of light appear and also crackling sound is produced.
8. When the pressure is reduced to the order of 10mm of Hg, a luminous column known as positive column is formed from anode to cathode.
9. When the pressure reaches to around 0.01 mm of Hg, positive column disappears. At this time, a dark space is formed between anode and cathode which is often called Crooke’s dark space and the walls of the tube appear with green colour.
10. At this stage, some invisible rays emanate from cathode called cathode rays, which are later found be a beam of electrons.
Question 2.
Determination of the specific charge of the electron (e/m) from the path of an electron beam. When the magnetic field is switched off.
Answer:
When the magnetic field is turned off, the deflection is only due to the electric field.
The deflection in the vertical direction is due to the electric force.
Fe = eE …………….(1)
m – mass of the electron
According to Newton’s second law of motion,
Fe = mae ……………(2)
from eqn (1) and (2)
eE = mae
ae = (\(\frac{\mathrm{e}}{\mathrm{m}}\) E)
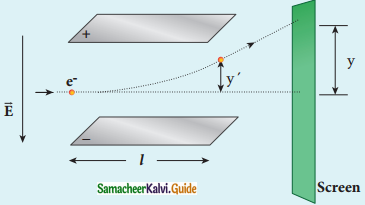
Deviation of path by applying uniform electric field
Let
y – deflection on the screen
u – initial upward velocity
l – length of one of the plates
t – time
The time taken by the cathode rays to travel in electric field t = (l/v)
Note:
u = 0, ae = e/m
S = ut + 1/2 at2
y’ = ut + 1/2 aet2
y’ = 1/2 \(\left(\frac{e}{m} E\right)\left(\frac{l}{V}\right)^{2}\)
V = E/B
y’ = \(1 / 2(\mathrm{e} / \mathrm{m}) \frac{l^{2} \mathrm{~B}^{2}}{\mathrm{E}}\)
y ∝ y’
y’ = cy’
C – proportionality constant which depends on the geometry of the discharge tube
y = c \(\left(\frac{1}{2}(\mathrm{e} / \mathrm{m}) \frac{l^{2} \mathrm{~B}^{2}}{\mathrm{E}}\right)\)
e/m = \(\frac{2 \mathrm{yE}}{\mathrm{c} l^{2} \mathrm{~B}^{2}}\)
Substituting the values on RHS, e/m = 1.7 × 1011 Ckg-1
![]()
Question 3.
Determination of the specific charge of the electron (e/m) from the path of an electron beam when the electric field is switched off.
Answer:
1. Suppose that the electric field is switched off and only the magnetic field is switched on. Now the deflection occurs only due to the magnetic field.
2. The force experienced by the electron in a uniform magnetic field applied perpendicular to its path is
Fm = BeV …………..(1)
3. Since this force provides the centripetal force, the electron beam undergoes a semi-circular path.
F = \(\frac{m v^{2}}{R}\) ………….(2)
from eqn (1) and (2)
Bev = \(\frac{m v^{2}}{R}\)
e/m = V/BR ……………(3)
V = E/B
e/m = E/B2R ………………(4)
Substituting the values on RHS,
e/m = 1.7 × 1011 Ckg-1
Question 4.
Explain the results of Rutherford a particle scattering experiment.
Answer:
1. A source of alpha particles (radioactive material, for example, polonium) is kept inside a thick lead box with a fine hole.
2. The explain particles coming through the fine hole of the lead box pass through another fine hole made on the lead screen.
3. These particles are now allowed to fall on the thin gold foil and it is observed that the alpha particles passing through gold foil are scattered through different angles.
4. A movable screen (from 0° to 180°) which is made up of zinc sulphide (ZnS) is kept on the other side of the gold foil to collect the alpha particles.
5. Whenever alpha particles strike the screen, a flash of light is observed which can be seen through a microscope.
6. Rutherford proposed an atom model based on the results of the alpha scattering experiment.
7. In this experiment, alpha particles (positively charged particles) are allowed to fall on the atoms of a metallic gold foil.
8. The results of this experiment are given below but the experiment showed the model.
- Most of the alpha particles are undeflected through the gold foil and went straight.
- Some of the alpha particles are deflected through a small angle.
- A few alpha particles (one in a thousand) are deflected through an angle more than 90°
- Very few alpha particles returned back (backscattered) that is, deflected back by 180°
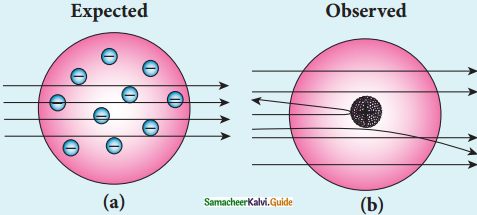
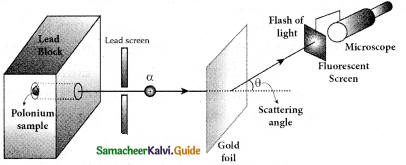
Schematic diagram for scattering of alpha particles experiments by Rutherford.
Question 5.
Explain the spectrum of Hydrogen.
Answer:
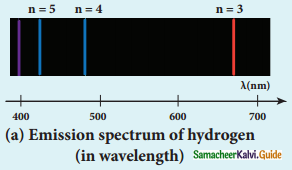
Emission spectrum of hydrogen:
When the hydrogen gas enclosed in a tube is heated up, it emits electromagnetic radiations of a certain sharply defined characteristic wavelength (line spectrum), called hydrogen emission spectrum.
The absorption spectrum of hydrogen:
1. When any gas is heated up, the thermal energy is supplied to excite the electrons. Similarly, by passing light on the atoms, electrons can be excited by absorbing photons.
2. Once the electrons get sufficient energy as given by Bohr’s postulate (c), it absorbs energy with particular wavelength (or frequency) and jumps from its stationary state (original state) to higher energy state. Those wavelengths (or frequencies) for which the colours are not observed are seen as dark lines in the absorption spectrum.
3. Since electrons in excited states have a very small lifetime, those electrons jump back to the ground state through spontaneous emission in a short duration (≈10-8 s) by emitting the radiation with the same wavelength (or) frequency corresponding to the colours it absorbed. This is called emission spectroscopy.
4. The following are the spectral series in hydrogen atom:
- Lyman series
- Balmer series
- Paschen series
- Brockett series
- Pfund series.
![]()
Question 6.
How does a smoke detector work?
Answer:
1. A very interesting application of alpha decay is in smoke detectors which prevent us from any hazardous fire.
2. The smoke detector uses around 0.2 mg of man made weak radioactive isotope called americium \({ }_{95}^{241} \mathrm{Am}\).
3. This radioactive source is placed between two oppositely charged metal plates and radiations from \({ }_{95}^{241} \mathrm{Am}\) continuously ionize the nitrogen, oxygen molecules in the air space between the plates.
4. As a result, there will be a continuous flow of small steady current in the circuit. If smoke enters, the radiation is being absorbed by the smoke particles rather than air molecules. As a result, the ionization and along with it the current is reduced.
5. This drop-in current is detected by the circuit and the alarm starts
6. The radiation dosage emitted by americium is very much less than the safe level, so it can be considered harmless.
Question 7.
Obtain an expression for half-life.
Answer:
1. We can define the half-life T1/2 as the time required for the number of atoms initially present to reduce to one-half of the initial amount.
2. The half-life is the important characteristic of every radioactive sample. Some radioactive nuclei are known to have half-life as long as 1014 years and some nucleus have a very shorter lifetime (10-14 S).
3. We can express half-life in terms of the decay constant. At t = T1/2, the number of undecayed
nuclei N = \(\frac{\mathrm{N}_{0}}{2}\)
4. By substituting this value into the equation, we get
\(\frac{\mathrm{N}_{0}}{2}\) = N0 e-λT1/2
1/2 = e-λT1/2 (or) e+λT1/2 = 2
Taking logarithm on both sides and rearranging the terms.
T1/2 = \(\frac{\ln 2}{\lambda}\) = \(\frac{0.6931}{\lambda}\) ……………(1)
5. If the number of atoms present at t = 0 is N0, then \(\frac{N_{0}}{2}\) atoms remain undecayed in first half life and \(\frac{N_{0}}{4}\) atoms remain undecayed after second half life and so on.
6. In general, after n half – lives, the number of nuclei remaining undecayed is given by
N = \(\left(\frac{1}{2}\right)^{\mathrm{n}}\) N0 …………..(2)
where n can be integer or non integer. Since the activity of radioactive sample also obeys the exponential decay law, we can also write an equation for an acitivity similar to equation,
[R = λN0 e-λt]
After n half lives, the activity or decay rate of any radiosample is
R = \(\left(\frac{1}{2}\right)^{\mathrm{n}}\) R0
Question 8.
Obtain an expression for mean life.
Answer:
1. The mean life time of the nucleus is the ratio of sum or integration of life times of all nuclei to the total number nuclei present initially.
2. The total number of nuclei decaying in the time interval for t to t + ∆t is equal to
R ∆t = λNe-λt ∆t.
3. It implies that until the time t, this R ∆t number of nuclei lived. So the life time of these R ∆t nuclei is equal to be tR∆t. In the limit ∆t = 0 the total life time of all the nuclei would be the integration of tRdt from the limit t = 0 to t = ∞
Mean life
τ = \(\frac{\int_{0}^{\infty} t[\mathrm{Rdt}]}{\mathrm{N}_{0}}\)
= \(\frac{\int_{0}^{\infty} t\left[\lambda N_{0} e^{-\lambda t} d t\right]}{N_{0}}\) ……………………(1)
After a few integration (refer box item), the expression for mean life time,
τ = 1/λ ………….(2)
mean life and decay constant is inversely proportional to each other. Using mean life, the half life can be rewritten as
T1/2 = τln2 = 0.6391 τ ………….(3)
Question 9.
Describe the discovery of neutrons. Discovery of Neutrons.
Answer:
- In 1930, two German physicists Both and Becker found that when beryllium was bombarded with a particles, highly penetrating radiation was emitted. This radiation was capable of penetrating the thick layer of lead and was unaffected by the electric and magnetic fields. Initially, It was thought aY radiation.
- But in the year 1932, James Chadwick discovered that those radiations are not EM waves but they are particles of mass little greater than the mass of the proton and had no charge. He called them as neutrons.
- The above reaction can be written as
\({ }_{4}^{9} \mathrm{Be}+{ }_{2}^{4} \mathrm{He} \rightarrow{ }_{6}^{12} \mathrm{C}+{ }_{0}^{1} \mathrm{n}\)
where \({ }_{0}^{1} \mathrm{n}\) denotes neutron
![]()
Question 10.
List the properties of neutrons.
Answer:
- Neutrons are the constituent particles of all nuclei, except hydrogen.
- Neutrons are neutral particles with no charge and mass slightly greater than protons.
- Neutrons are not deflected by electric and magnetic fields.
- Neutrons are stable inside the nucleus. But outside the nucleus they are unstable. If the neutron comes out of the nucleus (free neutron), it decays with the emission of proton, electron, and antineutrino with a half-life of 13 minutes.
- Neutrons are classified according to their kinetic as
- slow neutrons (0 to 1000 eV)
- fast neutrons (0.5 MeV to 10 MeV)
- The neutrons with an average energy of about 0.025 eV in thermal equilibrium are called a thermal neutron because at 298K, the thermal energy KT – 0.025eV. Slow and fast neutrons play a vital role in nuclear reactors.
- As neutrons are neutral, they can easily penetrate any nucleus.
Question 11.
What are the applications of radioisotopes?
Answer:
I) Medical applications:
- In the Medical applications field, radioisotopes are used both in diagnosis and therapy.
- Radio Cobalt [60C] – Treatment of cancer
- Radio – Sodium [24Na] – detect the presence of blocks in blood vessels.
- Radioiodine [131I] – detection of the nature of thyroid gland and also for the treatment.
- Radio [56Fe] – diagnose anaemia
- Radio [32P] – treatment of skin diseases.
II) Agriculture:
Radio – phosphorous [32P] – Increase the crop yields.
III) Industry:
In Industry, the lubricating oil containing radioisotopes is used to study the wear and tear of the machinery.
IV) Molecular biology:
In molecular biology, radioisotopes are used in sterilising pharmaceutical, and surgical instruments.
V) Radiocarbon dating:
Radio-carbon dating is a method of estimating the age of a dead specimen by calculating the amount of 14C present in the specimen having the half-life of 14C as 5730 years.
Question 12.
Explain chain reaction in nuclear fission.
Answer:
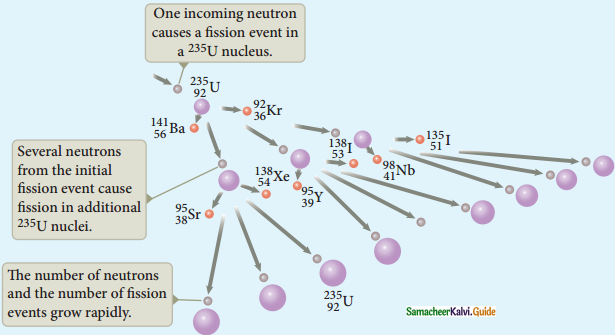
Nuclear chain reaction
1. When one \({ }_{92}^{235} \mathrm{U}\) nucleus undergoes fission, the energy released might be small. But from each fission reaction, three neutrons are released.
2. These three neutrons cause further fission in another three nuclei \({ }_{92}^{235} \mathrm{U}\) which in turn produce nine neutrons.
3. These nine neutrons initiate fission in another 27 \({ }_{92}^{235} \mathrm{U}\) nuclei and so on. This is called a chain reaction and the number of neutrons goes on increasing almost in a geometric progress
4. There are two kinds of chain reactions:
(i) uncontrolled chain reaction
(ii) controlled chain reaction.
5. In an uncontrolled chain reaction, the number of neutrons multiply indefinitely and the entire amount of energy released in a fraction of second.
6. The atom bomb is an example of nuclear fission in which an uncontrolled chain reaction occurs. Atom bombs produce massive destruction for mankind.
7. It is possible to calculate the typical energy released in a chain reaction.
8. In the 100th step, the number of nuclei that undergoes fission is around 2.5 x 1040
9. The total energy released after 100th step is 2.5 × 1040 × 200 MeV = 8 × 1029 J.
10. If the chain reaction is controllable, then we can harvest an enormous amount of energy for our needs.
11. It is achieved in a controlled chain reaction.
12. In the controlled chain reaction, the average number of neutron released in each stage is kept as one such that it is possible to store the released energy.
13. In nuclear reactors, the controlled chain reaction is achieved and the produced energy is used for power generation or for research purpose.
Question 13.
Calculate the average energy released per fission.
Answer:
Energy released in fission :
We can calculate the energy (Q) released in each uranium fission reaction. We choose the most
favorable fission which is given in the equation
\({ }_{92}^{235} \mathrm{U}+{ }_{0}^{1} \mathrm{n} \rightarrow{ }_{92}^{236} \mathrm{U}^{*} \rightarrow{ }_{56}^{141} \mathrm{Ba}+{ }_{36}^{92} \mathrm{Kr}+3{ }_{0}^{1} \mathrm{n}+\mathrm{Q}\)
Mass of \({ }_{92}^{235} \mathrm{U}\) = 235.045733 u
Mass of \({ }_{0}^{1} \mathrm{n}\) = 1.008665 u
Total mass of reactant = 236.054938 u
Mass of \({ }_{56}^{141} \mathrm{Ba}\) = 140.9177 u
Mass of \({ }_{36}^{92} \mathrm{Kr}\)= 91.8854 u
Mass of 3 neutrons = 3.025995 u
The total mass of products = 235.829095 u
Mass defect ∆m = 236.054398 u – 235.829095 u = 0.225303 u
So the energy released in each fission = 0.225303 × 931 MeV ≈ 200 MeV
This energy first appears as kinetic energy of daughter nuclei and neutrons. But later, this kinetic energy is transferred to the surrounding matter as heat.
![]()
XII. Additional Problems – (2 Marks):
Question 1.
The radius of the 5th orbit of hydrogen atom is 13.25 Å. Calculate the wavelength of the electron in the 5th orbit.
Solution:
2πr = nλ
2 × 3.14 × 13.25 Å = 5 × λ
λ = 16.64 Å
Question 2.
Calculate the radius of \({ }_{79}^{197} \mathrm{Au}\) nucleus.
Solution:
According to the equation
R = R0 A1/3,
R = 12 × 10-15 × (197)1/3
= 697 × 10-15 m
Or R = 6.97 F
Question 3.
Compute the binding energy per nucleon of \({ }_{2}^{4} \mathrm{He}\) nucleus.
Solution:
We found that the BE of \({ }_{2}^{4} \mathrm{He}\) = 28 Mev
Binding energy per nucleon = \(\overline{\mathrm{BE}}\) =28 MeV/4 = 7 MeV.
Question 4.
Calculate the mass of an electron from the known values of specific charge and charge of electron.
Solution:
Data:
e = 1.602 × 10-19 C
e/m = 1.759 × 1011 C Kg-1
m = e/m = \(\frac{1.602 \times 10^{-19}}{1.759 \times 10^{11}}\)
m = 9.1 × 10-31 kg
Question 5.
The radius of the 4th orbit of hydrogen atom is 2.12 A°. Calculate the wavelength of the electron in the 4th orbit.
Solution:
Data: r4 = 2.12 A°
2πr = nλ
λ4 = \(\frac{2 \pi r_{4}}{4}\)
= \(\frac{2 \times 3.14 \times 2.12 \mathrm{~A}^{0}}{4}\)
λ4 = 13.313 Å
![]()
Question 6.
The ground state energy of hydrogen atom is -13.6 eV. If an electron makes a transition from an energy level -0.85 eV to -1.51 eV, Calculate the wavelenth of the spectral line emitted. To which series of hydrogen spectrum does this wavelenth belong?
Solution:
Here ∆E = E2 – E1 = -0.85-(-1.51).
= 0.66 eV
∆E = 0.66 x 1.6 x 10-19 J
λ = \(\frac { hc }{ ∆E }\) = \(\frac{6.63 \times 10^{-34} \times 3 \times 10^{8}}{0.66 \times 1.6 \times 10^{-19}}\)
= 18.84 x 10-7
λ = 18840 Å
This wavelength belongs to the Pachen series of the hydrogen spectrum.
Question 7.
The half-life of radon is 3.8 days. Calculate its mean life.
Solution:
Data:
T1/2 = 3.8 days
τ = \(\frac{\mathrm{T}_{1 / 2}}{0.6931}\)
τ = T1/2 × 1.44
τ = 3.8 × 1.44
τ = 5.472 days
Question 8.
The isotope \({ }_{92}^{238} \mathrm{U}\) successively under goes three α- decays and two β– – decays what is the resulting isotope?
Solution:
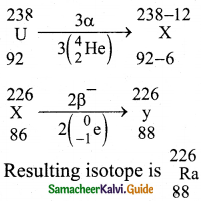
Question 9.
A radioactive isotope of silver has half life of 20 minutues. What fraction of the original mass would remain after one hour?
Solution:
Data:
T1/2 = 20 minutes
t = 1 hour = 60 minutes
n = \(\frac{t}{T_{1 / 2}}=\frac{60}{20}\) =3
\(\frac{\mathrm{N}}{\mathrm{N}_{\mathrm{o}}}\) = (1/2)n
= (1/2)3 = 1/8
Question 10.
How long will a radioactive isotope, whose half life is T years, take for its activity to reduce to 1/8 th of its initial value?
Solution:
Data:
R/R0 = 1/8
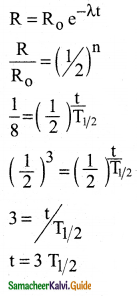
![]()
XIII. Additional Problems (3 Marks):
Question 1.
Express one atomic mass unit in energy units, first in Joules and then in MeV. Using this, express the mass defect of \(_{ 8 }^{ 16 }{ O }\) in MeV.
Solution:
We have, m = 1 amu = 1.66 x 10-27 kg, c = 3 x 108 ms-1
E = mc2 = 1.66 x 10-27 x (3 x 108)2
= 14.94 x10-11 J
= \(\frac{1.494 \times 10^{-10}}{1.6 \times 10^{-13}} \mathrm{MeV}\) [ 1 MeV = 1.6 x 10-13]
= 931.5 MeV
The \(_{ 8 }^{ 16 }{ O }\) nucleus contains 8 protons and 8 neutrons
Mass of 8 protons = 8 x 1.00727 = 8. 05816 amu
Mass of 8 neutrons = 8 x 1.00866 = 8. 06928 amu
Total Mass = 16.12744 amu
Mass of \(_{ 8 }^{ 16 }{ O }\) nucleus = 15.99053 amu
Mass defect = 0.13691 amu
∆Eb = 0.13691 x 931.5 Mev
∆Eb = 127.5 Mev
Question 2.
Forthe p fund series, calculatethe wavelength of the first member. Given Rydberg constant R = 1.09737 × 107 m-1
Solution:
Data:
R = 1.09737 × 107 m-1
For longest wavelength of paschen
n1 = 5, n2 = 6
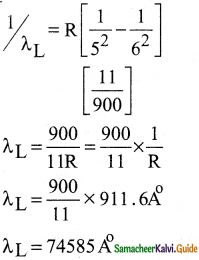
Question 3.
The wavelength of the second line of the Balmer series in the hydrogen spectrum is 4861 A° calculate the wavelength of the first line.
Solution:
Data:
λ2 = 4861 A°
n1 = 2, n2 = 3
1/λ1 = R[latex]\frac{1}{2^{2}}-\frac{1}{3^{2}}[/latex] = \(\frac{5 \mathrm{R}}{36}\)
n1 = 2, n2 = 4
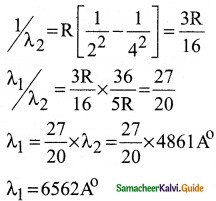
Question 4.
Calculate the value of fine structure constant.
Solution:
Data:
e = 1.6 × 10-19 C
ε0 = 8.854 × 10-12 C2 N-1 m2
h = 6.6 × 10-34 Nms
c = 3 × 108 m/s
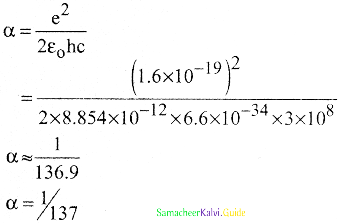
Question 5.
Determine the speed of electron in n = 3 orbit of He+ ion.
Solution:
Data:
n =3, z =2
νn = \(\frac{\alpha c Z}{n}\)
νn = \(\frac{C}{137} \frac{Z}{n}\) [∴ α = 1/137]
ν = \(\frac{3 \times 10^{8} \times 2}{137 \times 3}\)
ν = \(\frac{6}{411}\) × 108
= 0.0146 × 108
ν = 1.46 × 106 m/s
![]()
Question 6.
Calculate the distance of closest appraoch of a particles to the copper nucleus when a particles of 5 MeV are scattered back by a thin sheet of copper [Z for copper = 29]
Solution:
Data:
KE =1/2 mv2 = 5MeV
= 5 × 106 × 1.6 × 10-19 J
= 8 × 10-3 J[ 1 eV = 1.6 × 10-19 J]
Z = 29 r0 =?
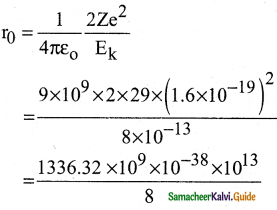
r0 = 167.04 × 10-16 m
r0 = 1.6704 × 10-14 m
Question 7.
If 200 MeV energy is released in the fission of a single nucleus of \(_{ 92 }^{ 235 }{ U }\), how many fissions must occur to produce a power of 1 kW?
Solution:
Let the number of fissions per second be n.
Then, Energy released per second = n x 200 MeV
= n x 200 x 1.6 x 10-13 J
Energy required per second = Power x Time
= 1kW x 1 s = 1000 J
Energy released = Energy required
n x 200 x 1.6 x 10-13 = 1000
n = 3.125 x 10-13
Question 8.
The half-life period of a radioactive element A is the same as the mean life of another radioactive element B. Initially both of them have the same number of atoms. The radioactive element B decays faster than A.Explain, why?
Solution:
element A decay constant λ
element B decay constant λ
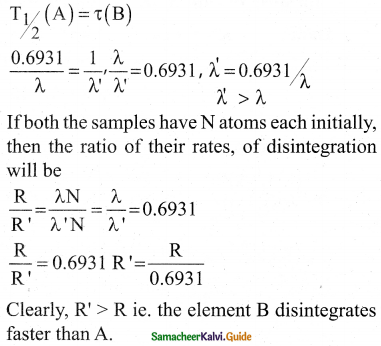
Question 9.
Find the (i) angular momentum (ii) velocity of the electron in the 5th orbit of hydrogen atom.
(h = 6.6 × 10-34 Js, m = 9.1 × 10-31 kg)
Solution:
(i) Angular momentum is given by l = n\(\hbar\)
= \(\frac{\mathrm{nh}}{2 \pi}\)
l = \(\frac{5 \times 6.6 \times 10^{-34}}{2 \times 3.14}\)
= 5.25 × 10-34 kgm2s-1
(ii) Velocity is given by
Velocity υ = \(\frac{l}{m r}\)
= 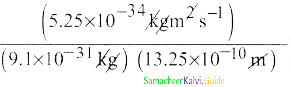
υ = 4.4 × 105 ms-1
Question 10.
Calculate the number of nuclei of carbon 14 undecayed after 22,920 years if the initial number of carbon – 14 atoms is 10,000. The half- life of carbon 14 is 5730 years.
Solution:
To get the time interval in terms of half- life,
n = \(\frac{t}{\mathrm{~T}_{1 / 2}}\)
= \(\frac{22,920 \mathrm{yr}}{5730 \mathrm{yr}}\) = 4
The number of nuclei remaining undecayed after 22,920 years,
N = (\(\frac{1}{2}\))n N0
= (\(\frac{1}{2}\))4 × 10,000
N = 625
Question 11.
An electron in Bohr’s hydrogen atom has an energy of – 3.4ev. what is the angular momentum of the electron?
Solution:
Given:
En = -3.4 eV
We know that, En = -13.6\(\frac{1}{n^{2}}\) eV
i.e. -3.4eV = -13.6\(\frac{e V}{n^{2}}\) (or)
n2 = \(\frac{13.6}{3.4}\) = 4
∴ n = 2
Angular momentum,
L = \(\frac{n h}{2 \pi}\)
L = \(\frac{2 \times\left(6.6 \times 10^{-34}\right)}{2 \times 3.14}\)
= 2.1 × 10-34 kgm2 s-1
![]()
XIV. Additional Problems (5 Marks):
Question 1.
A radioactive sample has 2.6 µg of pure which has a half life of 10 minutes. How many nuclei are present initially. Also find its initial activity.
Solution:
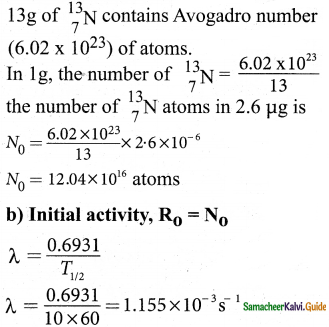
R0 = λN0
= 1.155 × 10-3 × 12.04 × 10-16
= 13.90 × 1013 decay/second
R0 = 13.90 × 1013 Bq
In terms of curie
R0 = \(\frac{13.90 \times 10^{13}}{3.7 \times 10^{10}}\)
= 3.75 × 103 [1 Ci = 3.7 × 1010 Bq]
Question 2.
The Bohr atom model is derived with the assumption that the nucleus of the atom is stationary and only electrons revolve around the nucleus. Suppose the nucleus is also in motion, then calculate the energy of this new system.
Solution:
1. Let the mass of the electron be m and mass of the nucleus be M. Since there is no external force acting on the system, the centre of mass of hydrogen atom remains at rest. Hence, both nucleus and electron move about the centre of mass as shown in figure.
2. Let v be the velocity of the nuclear motion and υ be the velocity of electron motion. Since the total linear momentum of the system is zero,
-mυ + Mυ = 0 or
Mυ = mυ = p
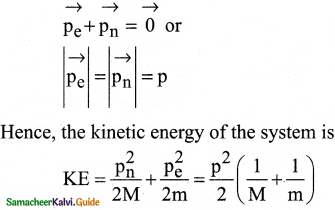
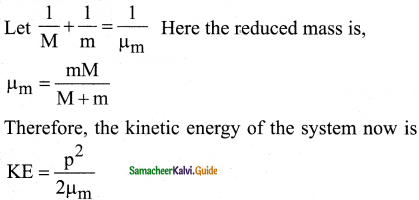
3 .Since the potential energy of the system is same, the total energy of the hydrogen can be expressed by replacing mass by reduced mass, which is
En = \(\frac{\mu_{\mathrm{m}} \mathrm{e}^{4}}{8 \varepsilon_{0}^{2} \mathrm{~h}^{2}} \frac{1}{\mathrm{n}^{2}}\)
4. Since the nucleus is very heavy compared to the electron, the reduced mass is closer to the mass of the electron.
Excition energy and excitation potential:
1. The energy required to excite an electron from lower energy state to any higher energy state is known as excitation energy.
2. The excitation energy for an electron from ground state (n = 1) to first excited state (n = 2) is called first
excitation enegy, which is
EI = E2 – E1 = -3.4 eV – (-13.6eV) = 10.2 eV
3. Similarly, the excitation energy for an electron from ground state (n = 1) to second excited state (n = 3) is
called second exciation energy, which is
EII = E3 – E1 = -1.51 eV – (-13.6eV) = 12.1 eV and so on.
4. Excitation potential is defined as excitation energy per unit charge:
E1 = eV1
⇒ V1 = \(\frac{1}{\mathrm{e}}\) E1 = 10.2 volt
5. Second excitation potential is,
EII = evII
=> VII = \(\frac{1}{\mathrm{e}}\)EII = 12.1 volt and so on.
Ionization energy and ionization potential:
An atom is said to be ionized when an electron is completely removed from the atom that is, it reaches the state with energy The minimum energy required to remove an electron from an atom in the ground state is known as binding energy or ionization energy.
Eionisation = E∞ – E1
= 0 – (-13.6 eV)
= 13.6 eV
When an electron is in nth state of an atom, the energy spent to remove an electron from that state – that is, its ionization energy is
Eionisation = E∞ – En
= 0 – (-\(\frac{13.6}{\mathrm{n}^{2}}\) Z2 eV)
= \(\frac{13.6}{\mathrm{n}^{2}}\) Z2 eV
At normal room temperature, the electron in a hydrogen atom (Z = 1) spends most of its time in the ground state. The amount of energy spent to remove an electron from the ground state of an atom (E = 0 for n—>∞) is known as first ionization energy (13.6 eV). Then, the hydrogen atom is said to be in ionized state or simply called as hydrogen ion, denoted by H+. If we supply more energy than the ionization energy, the excess energy will be the kinetic energy of the free electron.
Ionization potential is defined as ionization energy per unit charge.
Vionisation = \(\frac{1}{\mathrm{e}}\) Eionisation
= \(\frac{13.6}{\mathrm{n}^{2}}\) Z2 eV
Thus, for a hydrogen atom (Z = 1), the ionization potential is
V = \(\frac{13.6}{\mathrm{n}^{2}}\) volt
The radius, velocity and total energy in ground state, first excited state and second excited state is listed.
![]()
Question 3.
Suppose the energy of a hydrogen like atom is given as En = –\(\frac{54.4}{n^{2}}\) eV where n∈N. Calculate the following :
a) Sketch the energy levels for this atom and compute its atomic number.
b) If the atom is in ground state, compute its first excitation potential and also its ionization potential.
c) When a photon with energy 42eV and another photon with energy 56 eV are made to collide with this atom, does this atom absorb these photons?
d) Determine the radius of its first Bohr orbit
e) Calculate the kinetic and potential energies in the ground state.
Solution:
a) Given that En = –\(\frac{54.4}{n^{2}}\) eV
For n = 1, the ground state energy E1 = -54.4 eV and for n = 2, E2 = -13.6 eV.
Similarly E3 = -6.04 eV, E4 = -3.4 eV and so on.
For large value of principal quantum number – that is , n = ∞, we get E∞ = 0 eV

b) For a hydrogen like atom, ground state energy is
E1 = –\(\frac{13.6}{\mathrm{n}^{2}}\) Z2 eV
When Z is the atomic number. Hence, comparing this energy with given energy, we get,
-13.6 Z2 = -54.4 ⇒ Z = +2. Since, atomic number cannot be negative number Z = 2.
(c) The first excitation energy is
E1 = E2 – E1 = -13.6eV – (-54.4eV) = 40.8 eV
Hence, the first excitation potential is
V1 = \(\frac{1}{\mathrm{e}}\) E1 = \(\frac{(40.8 \mathrm{eV})}{\mathrm{e}}\) = 40.8 volt
The first ionization energy is
Eionisation = E∞ – E1 = 0 – (-54.4 eV) = 54.4 eV
Hence, the first ionization potential is
Vionisation = \(\frac{1}{\mathrm{e}}\) Eionisation
= \(\frac{(54.4 \mathrm{eV})}{\mathrm{e}}\)
= 54.4 volt
d) Consider two photons to be A and B.
Given that photon A with energy 42 eV and photon B with energy 51 eV.
From Bohr assumption, difference in energy levels is equal to photon energy, then atom will absorb energy, otherwise, not.
E2 – E1 = -13.6 eV – (-54.4 eV)
= 40.8 eV ≈ 41 eV
Similarly,
E3 – E1 = -6.04 eV – (-54.4 eV)
= 48.36 eV
E4 – E1 = -3.4 eV – (-54.4 eV)
= 51 eV
E3 – E2 = -6.04 eV -(-13.6 eV)
= 7.56 eV
and so on
But note that,
E2 – E1 ≠ 42 eV, E3 – E1 ≠ 42 eV,
E4 – E1 ≠42 eV and E3 – E2 ≠ 42 eV
For all possibilities, no difference in energy is an integer multiple of photon energy. Hence, photon A is not absorbed by this atom. But for Photon B, E4 – E1 = 51 eV, which means, photon B can be absorbed by this atom.
e) Since total energy is equal to negative of kinetic energy in Bohr atom model, we get
KEn = -En = -(-\(\frac{54.4}{n^{2}}\) eV)
= \(\frac{54.4}{n^{2}}\) eV
Potential energy is negative of twice the kinetic energy, which means,
Un = -2KEn = -2(\(\frac{54.4}{n^{2}}\) eV)
= \(\frac{108.8}{n^{2}}\) eV
For a ground state, put n = 1
Kinetic energy is KE1 = 54.4 eV and Potential energy is U1 = -108.8 eV
Question 4.
Compute the binding energy of \({ }_{2}^{4} \mathrm{He}\) nucleus using the following data : Atomic mass of Helium atom, M4 (He) = 4.00260 u and that of hydrogen atom, mH = 1.00785 u
Solution:
Binding energy BE [ZmH + Nmn – MA] c2
For helium nucleus, Z = 2, N = A – Z =4 – 2 = 2
Mass defect
∆m =[(2 × 1.00785 u) + (2 × 1 .008665u) – 4.00260u]∆m = 0.03038 u
B.E = 0.03038u × c2
B.E = 0.03038 × 931 MeV=28 MeV
[∴ 1 uc2 =931 MeV]
The binding energy of the \({ }_{2}^{4} \mathrm{He}\) nucleus is 28 MeV.
![]()
Question 5.
To determine the age of Keezhadi, the charcol of 200g sent for carbon dating. The activity of \(6 \mathrm{C}^{14}\) is found to be 38 decays/s. Calculate the age of charcoal. (Half life of \({ }_{6}^{14} \mathrm{C}\) = 5730 years)
Solution:
The activity R of the sample R = R0 eλ – t …………..(1)
eλ – t = \(\frac{R_{0}}{R}\)
t = \(\frac{1}{\lambda} \ln \left(\frac{R_{0}}{R}\right)\) …………..(2)
Here R = 38 decays/sec = 38 Bq
To find decay constant, we use the equation
λ = \(\frac{0.6931}{\mathrm{~T}_{1 / 2}}\)
= \(\frac{0.6931}{5730 \mathrm{yr} \times 3.156 \times 10^{7} \mathrm{~S} / \mathrm{yr}}\)
[ 1 yr = 365.25 × 24 × 60 × 60S = 3.156 × 107]
λ = 3.83 × 10-12 S-1
The mass of the charcoal is 200g
In 12g of carbon, there are 6.02 × 1023 carbon atoms
So 200g contains,
\(\frac{6.02 \times 10^{23} \text { atoms } / \mathrm{mol}}{12 \mathrm{~g} / \mathrm{mol}}\) × 200 ≈ 1 × 1025 atoms
The total number of carbon -14 atoms is given by
N0 = 1 × 1025 × 1.3 × 10-12 = 1.3 × 1013 atoms
The initial activity
R0 = 3.83 × 10-12 × 1.3 × 1012 = 50 decays/sec
R0 = 50 Bq
Substituting R0 in equation (2) we get