TN State Board 12th Computer Applications Important Questions Chapter 16 Electronic Payment Systems
Question 1.
What is physical money?
Answer:
Physical money is cash, which is the traditional and most widely used payment instrument that consumers use, in their daily lives to buy goods and services.
Question 2.
What is an electronic payment?
Answer:
The term electronic payment refers to a payment made from one bank account to another bank account using any one electronic methods.
![]()
Question 3.
What are newer electronic payment system?
Answer:
UPI, Bitcoin, Mobile payment, Digicash, eway, Paypal, Paytm, Applepay etc…
Question 4.
Write the classification of electronic payment methods.
Answer:
Electronic payment systems are generally classified into two types. They are
- Micro electronic payment systems.
- Macro electronic payment systems.
Question 5.
What is Micro Electronic Payment systems?
Answer:
Micro electronic payment systems is an on-line payment system designed to allow efficient and frequent payments of small amounts.
Eg: Watch a movie online.
![]()
Question 6.
What is Macro electronic payment systems?
Answer:
Macro electronic payment systems is an on-line payment systems, supports payment of higher value.
Eg: Card based payment.
Question 7.
What is payment cards?
Answer:
Payment cards are plastic cards that enable cashless payments.
Eg: Debit card.
Question 8.
What is credit card?
Answer:
- Credit card is an electronic payment system normally used for retail transactions.
- Credit card enables the bearer to buy goods or services from a vendor to payback the value later with an agreed interest.
![]()
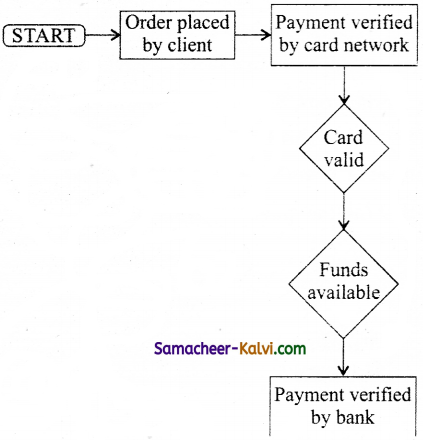
Question 9.
Who is Bearer?
Answer:
The holder of the credit card account who is responsible for payments of invoice in full or a portion of the balance and carried forward.
Question 10.
Who is merchant?
Answer:
Storekeeper or vendor who sell or providing service, receiving payment made by its customers through the credit card.
Question 11.
Who Acquirer?
Answer:
Merchant’s bank that is responsible for receiving payment on behalf of merchant send authorization requests to the issuing bank.
![]()
Question 12.
Define credit card network?
Answer:
Credit card network acts as the intermediate between the banks. The company responsible for communicating the transaction between the acquirer and the credit card issuer.
Question 13.
Who is Issuer?
Answer:
Bearer’s bank, that issue the credit card, set limit of purchases, decides the approval of transactions, issue invoices for payments, charges, offer card linked products, insurance, additional cards etc.
Question 14.
Write the size of the payment cards.
Answer:
All payment cards are usually plastic cards of size 85.60 mm width x 53.98 mm height, rounded comers with a radius of 2.88 mm to 3.48 mm and thickness of 0.76 mm.
![]()
Question 15.
What is EMV chip?
Answer:
EMV (Europay, Mastercard, Visa) is integrated chip in addition to magnetic stripe to store cardholder’s information.
Question 16.
What is RFID symbols?
Answer:
RFID symbols are four curved lines radiating rightwards similar to a titled Wi-Fi symbol. It indicates contactless smart card.
Question 17.
What is card brand logo?
Answer:
- Card brand logo is the name of the credit card network company.
- Visa, Mastercard, Rupay are leading credit card network companies.
![]()
Question 18.
What is magnetic stripe?
Answer:
Magnetic stripe is an iron based magnetic material containing encrypted data about the card holder and account number.
Question 19.
What is Hologram?
Answer:
Hologram is a security feature that prevents duplication. It is a 3-dimensional image formed by interference of light beams.
Question 20.
What is CVC / CW?
Answer:
CVC is a Card Verification Code / Card Verification Value is a 3 digit code usually printed to the left of signature pane validates the card.
![]()
Question 21.
What is debit card?
Answer:
Debit card is an electronic payment card where the transaction amount is deducted directly from the card holder’s bank account.
Question 22.
What are the ways of processing debit card transactions?
Answer:
Now, there are three ways of processing debit card transaction. They are
- EFTPOS (also known as online debit or PIN debit)
- Offline debit, (also known as signature debit)
- Electronic purse card system.
Question 23.
What is stored value cards?
Answer:
Stored value card is a type of debit card that is pre-loaded with certain amount, with which a payment is made. It is a card that has default monetary value on to it.
![]()
Question 24.
What are the types of stored value card?
Answer:
There are two types of stored value card, they are
- Closed loop: Closed loop cards are issued by a specific merchant.
- Open loop: Open loop cards can be used to make debit transactions at variety of retailers.
Question 25.
What is a smart card?
Answer:
A smart card is a physical card that has an embedded integrated chip that acts as a security. A smart card is the card with which we can exchange the data, store it and manipulate data.
Question 26.
What is ECS?
Answer:
ECS (Electronic Clearing Services) can be defined as repeated transfer of funds from one bank account to multiple bank accounts or vice versa.
![]()
Question 27.
What is EFT?
Answer:
EFT (Electronic Funds Transfer) is the electronic transfer of money over an online network. EFT is a widely used method for moving funds in B2B business models used.
Question 28.
What is E-cash?
Answer:
E-cash (Electronic Cash) is a currency that flows in the form of data. It is a digital money product that provides a way to pay for products and services without resorting to paper or coin currency.
Question 29.
What are function of cryptocurrency?
Answer:
The function of cryptocurrency is based on technologies such as mining, block chain, directed acyclic graph, distributed register etc.,
Question 30.
What is called Digicash?
Answer:
In 1989, David chaum an American cryptographer invented the first form of cryptocurrency called Digicash in the Netherlands.
![]()
Question 31.
Define the term Bitcoin.
Answer:
The term cryptocurrency began to be used after the appearance of the Bitcoin. Bitcoin is the most popular and the first decentralized cryptocurrency.
Question 32.
What is Altcoins?
Answer:
- Altcoins is the collective name for all cryptocurrencies that appeared after bitcoin.
- Many altcoins are inherently very similar to bitcoin in characteristics and structure.
Question 33.
What is mobile banking?
Answer:
Mobile banking is another form of net banking. The term mobile banking also called m-banking. M-banking refers to the services provided by the bank to the customer to conduct banking transactions with the aid of mobile phones.
![]()
Question 34.
What are the transaction made by the m-banking?
Answer:
- Balance checking, account transfers, payments, purchases etc…
- Transactions can be done at anytime and anywhere using m-banking.
Question 35.
What is known as Internet Banking?
Answer:
Internet banking is a collective term for E-banking, online banking, virtual banking, direct banks, web banking and remote banking.
Question 36.
What is self service banking?
Answer:
- Self service banking means, a branch of bank exclusively operating of an individual customer.
- The online banking system will typically connect to the core banking system operated by customers themselves.
Question 37.
Write the advantages of Internet banking.
Answer:
- In Internet banking access it can be used anywhere in the world and at any time.
- Internet banking does not need installing any additional software, that is any standard browser is adequate.
![]()
Question 38.
Expand the following,
(a) PIN;
(b) OTP;
(c) ACH;
(d) COD.
Answer:
(a) PIN – Personal Identification Number
(b) OTP – One Time Password
(c) ACH – Automated Clearing House
(d) COD – Cash On Delivery
Question 39.
What is UPI?
Answer:
UPI (Unified Payments Interface) is a real-time payment system developed by National Payments Corporation of India (NCPI) to facilitate inter-bank transactions.
Question 40.
What are the types of UPI of address?
Answer:
There are two types of UPI address, they are,
- Global address – It includes bank account numbers and IFSC.
- Local address – It is a virtual payment address.
![]()
Question 41.
What is VPA?
Answer:
VPA (Virtual Payment Address) is enable us to send and receive money from multiple banks and prepaid payment issuers. VPA also called as UPI-ID, is a unique ID similar to email-id.
Question 42.
What is MPIN?
Answer:
MPIN (Mobile Banking Personal Identification Number) is required to confirm each payment.
Question 43.
What is COD?
Answer:
COD (Cash On Delivery) also called as collection on delivery, describes a mode of payment in which the payment is made only on receipt of goods rather in advance.
![]()
Question 44.
What is BHIM?
Answer:
BHIM (BHarat Interface for Money) is an exclusive mobile app for UPI developed by National Payments Corporation of India (NPCI) and launched on 30 December 2016.
Question 45.
What is IFSC?
Answer:
IFSC (Indian Financial System Code) is an 11 digit alpha-numeric code issued by Reserve Bank of India.
Question 46.
What are the ways can be explained the Micro electronic payment transactions?
Answer:
- Customer proves his authentication and the payment processor issues micro payments.
- Customer pays the micro payments to the online service provider and gets the requested goods or services form them.
- Seryice provider deposits micro payments received from the customer to the payment processor and gets the money.
![]()
Question 47.
Write the steps on micro electronic payment systems work on the basis of simple cryptographic algorithms.
Answer:
- Hash chain based micro electronic payment system.
- Hash collisions and hash sequences based micro electronic payment systems.
- Shared secrete keys based micro electronic payment systems.
- Probability based micro electronic payment systems.
Question 48.
What are the popular macro on-line payment systems?
Answer:
Some of the popular macro on-line payment system are
- Card based payment systems.
- Electronic account transfer.
- Electronic cash payment systems.
- Mobile payment systems and Internet payment systems.
![]()
Question 49.
What are the ways used card payment system?
Answer:
There are three widely used card based payment systems. They are,
- Credit card based payment systems (Pay later)
- Debit card based payment systems (Pay now)
- Stored value card based payment systems (pay before)
Question 50.
Write a short note on Diners club card.
Answer:
- The Diners club card, which was made of paper card board.
- The card was accepted in only 27 restaurants and was used only by friends.
- Later it was enhanced and accepted worldwide.
- Now, the card was made of plastic and the diners club still exists today under the name Diners Club International.
Question 51.
How can be classified by smart cards?
Answer:
Smart cards can be classified into contact smart cards and contactless smart cards.
1. Contact smart cards: Contact smart cards have a contact area of approximately 1 square centimeter, comprising several gold-plated contact pads.
These cards used as a communication medium between the smart card and a host.
2. Contactless smart cards: Contactless smart card is empowered by RF induction technology.
Smart cards, whether they are contact or contactless cards do not have an internal power source.
![]()
Question 52.
Write the advantages of the Electronic ClearingServices (ECS).
Answer:
- ECS system are bulk payments, guaranteed payments and no need to remember payment dates.
- It can be used by institutions for making payments such as disbursing of salary, pension or dividend interest among shareholders.
- Individual bank customers can make small value such as paying EMI of a loan, electricity bills, telephone bills, insurance premium, as well as SIP investments.
Question 53.
Describes the users of ECS.
Answer:
ECS can be used for both credit and debit purposes.
1. ECS credit: ECS credit is used for making bulk payment of amounts. In this mode, a single account is debited and multiple accounts are credited. This type of transactions are push transactions.
2. ECS debit: ECS debit is an inverse of ECS credit. It is used for bulk collection of amounts. This type of transactions are pull transactions.
Question 54.
Explain NEFT.
Answer:
- NEFT (National Electronic Fund Transfer), it is called by India. In USA, they may be referred to as ‘e-cheques’.
- NEFT is an electronic fund transfer system initiated by the Reserve Bank of India.
- It is established and maintained by Institute for Development and Research in Banking Technology (IDRBT).
Question 55.
Explain the RTGS payment system.
Answer:
- RTGS (Real Time Gross Settlement system) is a payment system particularly used for the settlement of transactions.
- RTGS transactions are processed at the real-time, RTGS payments are also called push payments.
- RTGS transactions are unconditional and Irrevocable method.
![]()
Question 56.
Explain the block chain in cryptocurrency.
Answer:
- Blockchains are an open distributed book that records transactions of cryptocurrencies between any two parties in an efficient and verifiable manner.
- It is continuously growing list of records, called blocks, which are linked to each other and protected using encryption algorithm.
- Each block typically contains a hash pointer as link to a previous block.
- The validity of the coins of each cryptocurrency is also provided by a blockchain.
Question 57.
What are the ways can be implemented by mobile banking operations?
Answer:
The mobile banking operations can be implemented in the following ways
- Connecting the call center.
- Automative IVR telephone services.
- Using a mobile phone via SMS.
- WAP technology
- Using smartphone applications.
Question 58.
What are the advantages of credit card?
Answer:
- Most credit cards are accepted worldwide.
- It is not necessary to pay physical money at the time of purchase. The customer gets an extra period to pay the purchase.
- Depending on the card, there is no need to pay annuity.
- Alows purchases over the internet in installments.
- Some issuers allows “round up” the purchase price and pay the difference in cash to make the transaction easy.
![]()
Question 59.
Describe the modern credit card number.
Answer:
- The modem credit card number has 16 digit unique identification number.
- The first digit of the credit number is Major Industry Identifier (Mil). Eg: 4 banks.
- The next 5 digits uniqueiv identifies the issuing operations.
- The first 6 digits together called as Issuer Identification Number (IIN).
- The next 9 digits are the Account number.
- The last digit is a check digit.
Question 60.
How can you to transfer the fund using net banking?
Answer:
- Login to net banking account using user name with password given by the bank.
- Add the beneficiary as a payee to enable transfer of fund. Account number, Name, IFSC are to be filled.
- The beneficiary is added, choose RTGS / NEFT / IMPS as mode of fund transfer.
- Select the account to transfer money from, select the payee, enter the amount to be transferred.
- Click on submit button
- Now, enter the OTP received to mobile number linked to the corresponding, account for complete the transaction.
![]()
Question 61.
What are the advantage of mobile banking?
Answer:
- Immediate money transfers through mobile device round the clock 24×7.
- Can use single mobile application for accessing multiple bank accounts.
- Single click authentication for transferring of fund.
- There is not required to enter the details such as card number, Account number, IFSC etc., for every transaction.
- Electronic payments will become much easier without requiring a digital wallet, or credit or debit card.
Question 62.
Define electronic payment system.
Answer:
- An electronic payment system is a financial arrangement that consists an intermediator to facilitate transfer of money-substitute between a payer and a receiver.
- Sometimes it is also called liquidation, clearing system or clearing service.
![]()
Question 63.
Distinguish micro electronic payment and macro electronic payment.
Answer:
| Micro electronic payment |
Macro electronic payment |
| Micro electronic payment system designed to allow efficient and frequent payments of small accounts. | Macro electronic payment systems support payments of higher value. |
| As the security of micro electronic payment systems is comparatively low it could be tampered. | The security requirements are more rigorous in macro payment systems because of huge money transactions. |
Question 64.
List the types of micro electronic payments based on its algorithm.
Answer:
- Hash chain based micro electronic payment systems.
- Hash collisions and hash sequences based micro electronic payment systems.
- Shared secrete keys based micro electronic payment systems.
- Probability based micro electronic payment systems.
![]()
Question 65.
Explain the concept of e-wallet.
Answer:
- e-wallet (Electronic wallet) or electronics purses allow users to make electronic transactions quickly and securely over the internet through smartphones or computer.
- There are several electronic wallet services that are now widely used. Eg: Paypal, SBI Buddy.
Question 66.
What is a fork in cryptocurrency?
Answer:
Fork in cryptocurrency are cryptocoins, e-cash, alternative currencies or virtual currencies.
Cryptocurrency also be distributed accounting system based on cryptography, storing information about the state of ownership in conventional units.
Question 67.
Define micro electronic payment and its role in E-Commerce.
Answer:
- Micro electronic payment is an on-line payment system designed to . allow efficient and frequent payments of small accounts,
- The major role in E-Commerce is of micro electronic payment systems were designed to pay for simple goods on the Internet.
- And the micro on-line payments by customer, service provider and payment processor are involved.
![]()
Question 68.
Compare and contrast the credit card and debit card.
Answer:
| Credit card |
Debit card |
| Credit card is an electronic payment system normally used for retail transactions. | Debit card is an electronic payments and where the transactions amount is deducted directly from the card holder’s bank account. |
| A credit card enables the bearer to buy goods or services from a vendor, based on the cardholders limit and payback the value later. | Generally, debit cards function as ATM cards and acts as a substitute for cash. In modem era the use of debit cards has become so widespread. |
| Every credit card account has a purchase limit set by the issuing bank or the firm. | Every debit card has to purchase that amount is deduced directly from the card holders account. |
Question 69.
Explain briefly Anatomy of a credit card.
Answer:
All payment cards are usually plastic cards of size 85.60 mm width x 53.98 mm height, rounded comers with a radius of 2.88mm to 3.48mm and thickness of 0.76 mm.
- Publisher – Emplem of the issuing bank
- Credit card number – 16 digit unique identification number.
- EMV chip – Magnetic stripe to store information.
- RIFD symbol – It indicates that it is a contactless smartcard.
- Hologram – Security feature that prevent duplication.
![]()
Question 70.
Briefly explain the stored value card and its types.
Answer:
(i) Stored value card is a type of debit card that is pre-loaded with certain amount with which a payment is made.
(ii) The card may be disposed when the value is used, or recharged to use it again.
(iii) There are two types of stored value card, they are,
• Closed loop (single purpose)
• Open loop (Multi purpose)
Question 71.
Write a note on mining in cryptocurrency.
Answer:
- The cryptocurrency units are created by the solution of cryptographic • tasks called mining.
- The miners not only generate new monetary units, but also initiate new transactions to the block chain.
- As a reward, they will receive new Bitcoins.
- The process of mining is extremely electrical energy consumptive.
- The initial value of cryptographic currency is just the cost of consumed electricity.
![]()
Question 72.
What is credit card? Explain the key players of a credit card payment system and bring out the merits of it.
Answer:
Credit card is an electronic payment system normally used for retail transactions. A credit card enables the bearer to buy goods or services.
Key players of a credit card payments system:
- Bearer – The holder of the credit card account.
- Merchant – Storekeeper or vendor.
- Acquirer – Merchant’s bank
- Credit card network – It acts as the intermediate between banks.
- Issuer – Bearer’s bank.
Merits of credit card:
- Most credit cards are accepted world wide.
- It is not necessary to pay physical money at the time of purchase.
- Depending on the card, there is no need to pay annuity.
- Allows purchase over the internet in installments.
Question 73.
Briefly explain Electronic Account transfer and its types.
Answer:
Electronic account transfer is an alternative electronic payment system. With the advent of computers, network technologies and electronic communications a large number of alternative electronic payment systems have emerged.
They are ECS, EFT, RTGS, etc.,
(i) ECS (Electronic Clearing Services) can be defined from one bank account to multiple bank accounts or vice versa using computer and Internet technology.
ECS system provides the convenience of paperless payments. ECS can be used for both credit and debit purposes.
(ii) EFT (Electronic Funds Transfer) is the ‘electronic transfer’ of money over an online network.
The amount sent from the sender’s bank branch is credited to the receiver’s bank branch on the same day in batches.
(iii) RTGS (Real Time Gross Settlement) system is a payment system particularly used for the settlement of transactions between the banks. Real time gross settlement transactions are unconditional and irrevocable.
![]()
Question 74.
Write a note on:
(a) Internet banking
(b) Mobile banking.
Answer:
(a) Internet banking:
- Internet banking is a collective term for E-banking, online banking, virtual banking, direct banks, web banking and remote banking.
- Internet banking allows customers of a financial institution to conduct various financial transactions on a secure website.
- It enables customers of a bank to conduct a wide range of financial transactions through its website.
- The online banking system will typically connect to the core banking operated by customers themselves.
(b) Mobile banking:
- Mobile banking is another form of net banking .
- The term mobile banking (m-banking) refers to the services provided by the bank to the customer to conduct banking transactions with the aid of mobile phones.
- Transactions can be done at any time and anywhere. Transactions include balance checking, account transfers, payments, purchases etc.,
- Mobile banking operations can be implemented in the callcenter, IVR service,SMS, WAP and smartphone applications.
![]()
Question 75.
What is cryptocurrency? Explain the same.
Answer:
(i) Cryptocurrency can be defined as distributed accounting system based on cryptography, storing information about the state of ownership in conventional units.
(ii) Cryptocurrency is also called as cryptocoins, e-cash, alternative . currencies or virtual currencies and are classified as a subset of digital currencies.
(iii) The function of Cryptocurrency is based on technologies such as Bitcoin, Altcoins, mining, Block chain, directed Acylic Gaph, Distributed Register etc.,
(iv) Bitcoin is the most popular Cryptocurrency, but there are many other Cryptocurrencies, which are referred to as altcoins.
(v) Altcoins is the collective name for all Cryptocurrencies that appeared after Bitcoin.
(vi) Many altcoins are inherently very similar to Bitcoin in characterises, and structure.
(vii) The cryptocurrency units are created by the solutions of erytographic tasks called mining.
(viii) The process of mining is extremely electrical energy consumptive.
(ix) Block chains are an open distributed book that records transactions of cryptocurrencies between any two parties in an efficient and verifiable manner.
Question 76.
Explain in detail: Unified payments interface.
Answer:
(i) Unified Payments Interface (UPI) is a real-time payment system developed by National Payments Corporation of India (NCPI) to facilitate inter-bank transactions. –
(ii) UPI is simple, secure and instant payment facility. This interface is regulated by the Reserve Bank of India.
(iii) UPI withdraws and deposits funds directly from the bank aecc at wherever a transaction is requested. .
(iv) UPI is also available as an Unstructured Supplementary Service D .ui (USSD) service.
(v) UPI is developed on the basis of Immediate Payment Service (IMPS).
(vi) To initiate a transaction, UPI applications use two types of address, Global address and Local address.
(vii) Virtual Payment Address (VPA) also called as UPI-ID, is a unique ID enable us to send and receive money from multiple banks.
(viii) The MPIN (Mobile banking Personal Identification Number) is required • to confirm each payment.
(ix) UPI allows operating multiple bank accounts in a single mobile application.
![]()
Question 77.
Choose any presentation tool (e.g, Open office impress)
Answer:
Start the program ‘open office impress’ for creating presentation on title ‘various payment system’.
Click open office impress → presentation → Empty presentation → Select background colour, slide transition, presentation type,then click create.
Slide layout is created, now we can type the title as ‘various payment methods’.
Question 78.
Create a slide describing a payment method.
Answer:
Type the sub heading as ‘Description’ and then type description as “The method of payment” depend on.
- The item we are buying
- The cost of the item
- The method of payment accepted by the seller. The payment methods are cash, debit or credit cards, cheque, electronic transfer payments and EMI payment.
Question 79.
List the futures of the particular payment method.
Answer:
- An electronic payment is a non-cash payment though electronic medium.
- There are various features like credit payment system, E-wallet, smart card, real time payment system.
![]()
Question 80.
List the advantages and disadvantages of the same.
Answer:
Advantages:
- Increase sales.
- Reduced transaction costs.
- Increased speed and convenience.
- Easily accessible and user friendly.
Disadvantage:
- Security concerns
- Disputed transactions
- Increased business costs.
- Necessity of Internet Access.
![]()
Question 81.
Repeat the steps for other payment methods.
Answer:
Cash:
Cash payment using banknotes and coins. It is most common method of payment.
Advantage:
Widely accepted, fast and convenient.
Disadvantage:
Cash and coins are heavy to carry around.
Cannot used for online transaction.
Debit and credit card:
A card issued by the bank. The purchase amount is deducted immediately from bank accounts.
Advantage:
(i) Easy to carry and use.
(ii) Cashless payments
Disadvantage:
(i) Lost card can be misused.
(ii) In credit card, interest will be charged.
![]()
Choose the correct answer:
Question 1.
Which is the traditional and most widely used payment instrument that consumer use, in their daily lives?
(a) Electronic payment
(b) Physical money
(c) Account transfer
(d) Mobile payment
Answer:
(b) Physical money
Question 2.
Which is also called as liquidation, clearing system or clearing service?
(a) Electronic payment
(b) Physical money
(c) Account transfer
(d) Cash payment
Answer:
(a) Electronic payment
Question 3.
Which system is an essential part of a companies financial operations?
(a) Payment
(b) Account
(c) e-wallet
(d) Internet
Answer:
(a) Payment
![]()
Question 4.
Which of the following is of newer payment system?
(a) Paytm
(b) UPT
(c) Bitcoin
(d) All of these
Answer:
(d) All of these
Question 5.
How many types of electronic payment system classified?
(a) 2
(b) 3
(c) 4
(d) 5
Answer:
(a) 2
Question 6.
Which one of the payment system is designed to allow payments of small amounts?
(a) Micro
(b) Macro
(c) cheque
(d) All of these
Answer:
(a) Micro
![]()
Question 7.
Which electronic payment that use expensive public key cryptography?
(a) Micro
(b) Macro
(c) cheque
(d) All of these
Answer:
(b) Macro
Question 8.
Which electronic payment systems support payment of higher value?
(a) Micro
(b) Macro
(c) cheque
(d) All of these
Answer:
(b) Macro
Question 9.
Which are called plastic cards that enable cashless payments?
(a) Credit card
(b) Debit card
(c) Payment card
(d) All of these
Answer:
(d) All of these
![]()
Question 10.
Which known as electronic payment system normally used for retail transactions and payback to the issuer?
(a) Debit card
(b) Traveler card
(c) Credit card
(d) All of these
Answer:
(c) Credit card
Question 11.
Who is holder of the credit card account and responsible for payment?
(a) Bearer
(b) Merchant
(c) Acquirer
(d) Issuer
Answer:
(a) Bearer
Question 12.
Who is receiving payment made by its customers through the credit card?
(a) Bearer
(b) Merchant
(c) Acquirer
(d) Issuer
Answer:
(b) Merchant
![]()
Question 13.
_________ is responsible for receiving payment on behalf of merchant?
(a) Bearer
(b) Merchant
(c) Acquirer
(d) Issuer
Answer:
(c) Acquirer
Question 14.
Who is that issue the credit card, set limit of purchases, and is bearer’s bank?
(a) Bearer
(b) Merchant
(c) Acquirer
(d) Issuer
Answer:
(d) Issuer
Question 15.
How many digit has modern credit card identification number?
(a) 12
(b) 14
(c) 16
(d) 20
Answer:
(c) 16
![]()
Question 16.
The first 6 digits together called in credit card number?
(a) UN
(b) ISO
(c) IEC
(d) CVC
Answer:
(a) UN
Question 17.
Which chip is magnetic stripe to store card holder’s information?
(a) IIN
(b) ISO
(c) CVC
(d) EMV
Answer:
(d) EMV
Question 18.
EMV stands for:
(a) Electronic Machine Verifier
(b) European Machine Verification
(c) Electronic Model Verifier
(d) Europay Mastercard Visa
Answer:
(d) Europay Mastercard Visa
![]()
Question 19.
Which is Indian domestic open loop card launched in 2012?
(a) Master card
(b) Rupay
(c) Paytm
(d) Visa
Answer:
(b) Rupay
Question 20.
Which is an iron based magnetic material containing encrypted data?
(a) EMV chip
(b) RFID symbol
(c) Hologram
(d) Magnetic stripe
Answer:
(d) Magnetic stripe
![]()
Question 21.
Which is a security feature that prevents duplication in credit card?
(a) Hologram
(b) Card logo
(c) RFID symbol
(d) Magnetic strip
Answer:
(a) Hologram
![]()
Question 22.
How many digit is Card Verification Code (CVV) in credit card usually printed?
(a) 2
(b) 3
(c) 4
(d) 5
Answer:
(b) 3
Question 23.
Which card is transaction amount directly deducted the cardholder’s bank account?
(a) Credit
(b) Traveller
(c) Debit
(d) Pre paid card
Answer:
(c) Debit
Question 24.
How many ways are there processing debits card transactions?
(a) 2
(b) 3
(c) 4
(d) 5
Answer:
(b) 3
![]()
Question 25.
Which type of card is pre-loaded with certain amounts for future use?
(a) Credit
(b) Stored value
(c) Traveller
(d) Paytm
Answer:
(b) Stored value
Question 26.
How many type of store value card available?
(a) 2
(b) 3
(c) 4
(d) 5
Answer:
(a) 2
Question 27.
Which is modern version of card based on payments?
(a) debit card
(b) credit card
(c) smartcard
(d) pre-paid card
Answer:
(c) smartcard
![]()
Question 28.
Which type of smart cards have a contact area of approximately square centimeter?
(a) Contact
(b) contactless
(c) EFT
(d) All of these
Answer:
(a) Contact
Question 29.
Which type of smart card is empowered by RF induction technology?
(a) Contact
(b) contactless
(c) EFT
(d) All of these
Answer:
(b) contactless
Question 30.
What is called as repeated transfer of funds from one bank account to multiple bank account or vice verse?
(a) ECS
(b) EFT
(c) RTGS
(d) NEFT
Answer:
(a) ECS
![]()
Question 31.
Which type of transactions are called push transactions?
(a) ECS credit
(b) ECS debit
(c) NEFT
(d) EFT
Answer:
(a) ECS credit
Question 32.
Which is an inverse of ECS credit and is used for bulk collection of amounts?
(a) ECS credit
(b) ECS debit
(c) NEFT
(d) EFT
Answer:
(b) ECS debit
Question 33.
Which type of transactions are called as pull transactions?
(a) ECS credit
(b) ECS debit
(c) NEFT
(d) EFT
Answer:
(b) ECS debit
![]()
Question 34.
Which is the ‘electronic transfer’ of money over an online network?
(a) ECS credit
(b) ECS debit
(c) NEFT
(d) EFT
Answer:
(d) EFT
Question 35.
Which method is widely used and B2B business models?
(a) EFT
(b) ECS credit
(c) ESC debit
(d) NEFT
Answer:
(a) EFT
Question 36.
Which systems world wide is driven primarily by the central bank of a country?
(a) NEFT
(b) RTGS
(c) ESC
(d) Either (a) or (b)
Answer:
(d) Either (a) or (b)
![]()
Question 37.
Which is a currency that flows in the form of data?
(a) E-cash
(b) Cash
(c) Cheque
(d) all of these
Answer:
(a) E-cash
Question 38.
Which is a unique virtual asset designed to work as a medium of exchange using cryptographic algorithm?
(a) Conditional
(b) Unconditional
(c) Irrevocable
(d) Cryptocurrency
Answer:
(d) Cryptocurrency
Question 39.
Which is as distributed accounting system based on cryptography?
(a) Conditional
(b) Unconditional
(c) Irrevocable
(d) Cryptocurrency
Answer:
(d) Cryptocurrency
![]()
Question 40.
Which is the state of ownership of a cryptocurrency is related to individual system blocks?
(a) Portfolios
(b) Conditional
(c) Unconditional
(d) Irrevocable
Answer:
(a) Portfolios
Question 41.
David chaum an American cryptographer invented the first form of crytocurrency called.
(a) Mining
(b) Digicash
(c) Block chain
(d) Bitcoin
Answer:
(b) Digicash
Question 42.
Which is the most popular and the first decentralized cerptocurrency?
(a) Mining
(b) Digicash
(c) Block chain
(d) Bitcoin
Answer:
(d) Bitcoin
![]()
Question 43.
Which is the collective name for all crypotocuurencies that appeared after bitcoin?
(a) Altcoins
(b) Mining
(c) Digicash
(d) Block chain
Answer:
(a) Altcoins
Question 44.
Which is inherently very similar to Bitcoin in characteristics and structure?
(a) Altcoins
(b) Mining
(c) Digicash
(d) Block chain
Answer:
(a) Altcoins
Question 45.
Which are called the cryptocurrency units are created by the solution of cryptographic tasks?
(a) Altcoins
(b) Mining
(c) Digicash
(d) Block chain
Answer:
(b) Mining
![]()
Question 46.
The process of mining is extremely consumptive.
(a) Electrical energy
(b) Thermal energy
(c) Wind energy
(d) Solar energy
Answer:
(a) Electrical energy
Question 47.
Which are an open distributed book that records transactions of cryptocurrencies?
(a) Altcoins
(b) Mining
(c) Digicash
(d) Block chains
Answer:
(d) Block chains
Question 48.
Which are by default resistant to data modification without approval of a trusted authority?
(a) Altcoins
(b) Mining
(c) Digicash
(d) Block chains
Answer:
(d) Block chains
![]()
Question 49.
Which are safely designed with high fault tolerance it is best suited to distributed computing system?
(a) Altcoins
(b) Mining
(c) Digicash
(d) Block chains
Answer:
(d) Block chains
Question 50.
Which are allow users to make electronic transactions quickly and securely over smartphones?
(a) e-wallets
(b) Blockchain
(c) e-purses
(d) (a) and (c)
Answer:
(d) (a) and (c)
Question 51.
Which is first recognized and popular method for storing money in electronic form?
(a) e-wallets
(b) Blockchain
(c) Digicash
(d) Mining
Answer:
(a) e-wallets
![]()
Question 52.
Paypal is a:
(a) e-wallets
(b) Blockchain
(c) Digicash
(d) Mining
Answer:
(a) e-wallets
Question 53.
How many digits are IFSC alpha numeric code that uniquely identify individual bank branch?
(a) 6
(b) 9
(c) 11
(d) 13
Answer:
(c) 11
Question 54.
Which is a real time payment system developed by NPCI?
(a) Unified Payment Interface (UPI)
(b) Cash On Delivery (COD)
(c) ECS
(d) RTGS
Answer:
(a) Unified Payment Interface (UPI)
![]()
Question 55.
Virtual Payment Address (VPA) also called as:
(a) UPI – ID
(b) MPIN
(c) IMPS
(d) IFSC
Answer:
(a) UPI – ID
Question 56.
MPIN stands for:
(a) Mobile Banking Personal Identification Number
(b) Money Banking Personal Identification Number
(c) Mobile Banking Personal Individual Number
(d) Mobile Banking Paying Identified Number
Answer:
(a) Mobile Banking Personal Identification Number
Question 57.
Which is required to confirm each payment?
(a) UPI-ID
(b) MPIN
(c) IMPS
(d) IFSC
Answer:
(b) MPIN
![]()
Question 58.
USSD stands for:
(a) Unstructured Supplementary Service Data.
(b) United Supplementary Service Device.
(c) United Secondary System Device.
(d) Unstructured Secondary System Data.
Answer:
(a) Unstructured Supplementary Service Data.
Question 59.
What will become much easier without requiring a digital wallet or credit or debit card?
(a) Cash on delivery
(b) Electronic payment
(c) e-pay
(d) e-service
Answer:
(b) Electronic payment
Question 60.
Which is also called so collection on delivery and describes a mode of payment?
(a) Cash on delivery(COD)
(b) e-payment
(c) e-pay
(d) e-service
Answer:
(a) Cash on delivery(COD)
![]()
Question 61.
BHIM stands for:
(a) Bank Hologram Intemational.Money
(b) Bharat Interface for Money
(c) Bank Host Imediate Money
(d) Bharat Help Insurance Money
Answer:
(b) Bharat Interface for Money
Question 62.
NPCL stands for:
(a) Natural Payments Corporation of India
(b) National Pacific corporation of India
(c) National Payments Corporation of India
(d) Network Payments Corporation of India
Answer:
(c) National Payments Corporation of India
Question 63.
Match the following (Operations of credit card).
| (A) Bearer | (i) Shopkeeper |
| (B) Merchant | (ii) Bearer’s Bank |
| (C) Acquirer | (iii) Card holder |
| (D) Issuer | (iv) Merchant’s bank |
(a) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
(b) (A) – (i); (B) – (ii); (C) – (iv); (D) – (iii)
(c) (A) – (ii); (B) – (i); (C) – (iii); (U) – (iv)
(d) (A) – (iv); (B) – (iii); (C) – (i); (D) – (ii)
Answer:
(a) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
![]()
Question 64.
Match the following (Anatomy of a Credit card).
| (A) EMV chip | (i) Wi Fi symbol |
| (B) RFID symbol | (ii) Chip and PIN |
| (C) Magnetic Strip | (iii) Prevent duplicate |
| (D) Hologram | (iv) encrypted data |
(a) (A) – (iii); (B) – (ii); (C) – (i); (D) – (iv)
(b) (A) – (ii); (B) – (i); (C) – (iv); (D) – (iii)
(c) (A) – (ii); (B) – (iii)- (C) – (i); (D) – (iv)
(d) (A) – (iv); (B) – (iii); (C) – (ii); (D) – (i)
Answer:
(b) (A) – (ii); (B) – (i); (C) – (iv); (D) – (iii)
Question 65.
Match the following (Electronic Account Transfer):
| (A) ECS | (i) Electronic Transfer |
| (B) ECS Credit | (ii) Pull transactions |
| (C) ECS Debit | (iii) Push transactions |
| (D) EFT | (iv) Electronic Clearing System |
(a) (A) – (ii); (B) – (iii); (C) – (i); (D) – (iv)
(b) (A) – (ii); (B) – (i); (C) – (iv); (D) – (iii)
(c) (A) – (iv); (B) – (iii); (C) – (ii); (D) – (i)
(d) (A) – (iv); (B) – (ii); (C) – (i); (D) – (iii)
Answer:
(c) (A) – (iv); (B) – (iii); (C) – (ii); (D) – (i)
Question 66.
Match the following (Cryptocurrency):
| (A) Bitcoin | (i) First cryptocurrency |
| (B) Altcoin | (ii) blocks |
| (C) Mining | (iii) Similar to Bitcoin |
| (D) Block chain | (iv) Cryptographic tasks |
(a) (A) – (iii); (B) – (iv); (C) – (ii); (D) – (i)
(b) (A) – (iii); (B) – (ii); (C) – (i); (D) – (iv)
(c) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
(d) (A) – (i); (B) – (iii); (C) – (iv); (D) – (ii)
Answer:
(d) (A) – (i); (B) – (iii); (C) – (iv); (D) – (ii)
![]()
Question 67.
Match the following (Unified Payment Interface):
| (A) UP | (i) Inter bank transactions |
| (B) NCPI | (ii) Mode of fund transfer |
| (C) IFSC | (iii) real time payment |
| (D) RTGS | (iv) Global address |
(a) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
(b) (A) – (iii); (B) – (ii); (C) -(i); (D) – (iv)
(c) (A) – (iv); (B) – (iii); (C) – (i); (D) – (ii)
(d) (A) – (iv); (B) – (i); (C) – (ii); (D) – (iii)
Answer:
(a) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
Question 68.
Choose the incorrect pair:
(a) Physical money – Cash
(b) Paytm – Payment system
(c) Debit card – Pay cater
(d) Traveller card – Pay before
Answer:
(c) Debit card – Pay cater
Question 69.
Choose the incorrect pair .
(a) Debit card – Physical Properties
(b) EFT pos – PIN debit
(c) offline debit – signature debit
(d) Rupay – closed loop card
Answer:
(d) Rupay – closed loop card
![]()
Question 70.
Choose the incorrect pair:
(a) EFT – B2B
(b) NEFY – pull transaction
(c) RTGS – Large payments
(d) RBI – Central Bank
Answer:
(b) NEFY – pull transaction
Question 71.
Choose the correct pair:
(a) Digicash – e-cheque
(b) Namecoin- DNS server
(c) e-wallets – e-purses
(d) e-wallet – SBI Buddy
Answer:
(a) Digicash – e-cheque
Question 72.
Choose the correct pair:
(a) m-banking – net banking
(b) e-banking – web banking
(c) Google chrome – direct banks
(d) e-payments – cashless
Answer:
(c) Google chrome – direct banks
![]()
Question 73.
Choose the incorrect statement:
(a) Cash is a physical money and traditionally widely used as payment.
(b) An electronic payment system is also called liquidation.
(c) Many electronic payment system have been developed by internet technologies.
(d) Payment system is not an essential part of financial operations.
Answer:
(d) Payment system is not an essential part of financial operations.
Question 74.
Choose the incorrect statement:
(a) Hash chain based macro electronic payment systems.
(b) Hash collisions based micro electronic payment systems.
(c) Hash sequences based micro electronic payment systems.
(d) Shared secrete keys based micro electronic payment systems.
Answer:
(a) Hash chain based macro electronic payment systems.
Question 75.
Choose the incorrect statement:
(a) The Diners club card which was made of paper-card board.
(b) The Diners club card still exists today the name of diners club international.
(c) Credit card only accepted within the country.
(d) Depending on the credit card, there is no need to pay annuity.
Answer:
(c) Credit card only accepted within the country.
![]()
Question 76.
Choose the correct statement:
(a) Card verification code (CVC / CW) value is a 4 digit code.
(b) A credit card or debit card it is a plastic and has a magnetic strip on its back.
(c) The modem based payment system is e-cheque.
(d) The credit card is that pre-loaded with certain amounts.
Answer:
(b) A credit card or debit card it is a plastic and has a magnetic strip on its back.
Question 77.
Choose the correct statement:
(a) Electronic cash is (E-Cash) is a currency that flows in the form of data.
(b) Many E-commerce websites that use e-wallets as a smart card.
(c) Mobile banking also called as e-banking.
(d) Virtual Payment Address (VPA) also called as United Payment Interface (UPI).
Answer:
(a) Electronic cash is (E-Cash) is a currency that flows in the form of data.
Question 78.
Assertion (A):
Credit card is an electronic payment system normally used for retail transactions.
Reason (R):
A credit card enables the bearer to buy goods or services from a vendor, to pay back the value later.
(a) Both A and R are True, and R is the correct explanation for A.
(b) Both A and R are True, but R is not the correct explanation for A.
(c) A is True, but R is false. .
(d) A is false, but R is true.
Answer:
(a) Both A and R are True, and R is the correct explanation for A.
![]()
Question 79.
Assertion (A):
The modern version of card based payment is smart cards.
Reason (R):
Open loop cards can be used to make debit transaction at variety of retailers, is also called as prepaid – debit cards.
(a) Both A and R are True, and R is the correct explanation for A.
(b) Both A and R are True, but R is not the correct explanation for A.
(c) A is True, but R is false.
(d) A is false, but R is true.
Answer:
(b) Both A and R are True, but R is not the correct explanation for A.
Question 80.
Assertion (A):
Electronic Clearing Service (ECS) can be defined as repeated transfer of funds.
Reason (R):
ECS system provides only small amounts transaction.
(a) Both A and R are True, and R is the correct explanation for A.
(b) Both A and R are True, but R is not the correct explanation for A.
(c) A is True, but R is false.
(d) A is false, but R is true.
Answer:
(c) A is True, but R is false.
Question 81.
Assertion (A):
RTGS payments are generally small-value^ayment.
Reason (R):
RTGS payments are also called as push payments that are triggered by the payer.
(a) Both A and R are True, and R is the correct explanation for A.
(b) Both A and R are True, but R is not the correct explanation for A.
(c) A is True, but R is false.
(d) A is false, but R is true.
Answer:
(d) A is false, but R is true.
![]()
Question 82.
Assertion (A):
The process of mining is extremely Bio energy consumptive.
Reason (R):
e-wallets transactions are not securely through smart phones.
(a) Both A and R are True.
(b) Both A and R false.
(c) A is True, but R is false.
(d) A is false, but R is true.
Answer:
(b) Both A and R false.
Question 83.
Pick the odd one out: (Micro electronic payment).
(a) Subscriptions of online games
(b) read journals
(c) a movie online
(d) Mobile payment
Answer:
(d) Mobile payment
Question 84.
Pick the odd one out: (Cards)
(a) Credit card
(b) Debit card
(c) PAN card
(d) Stored value card
Answer:
(c) PAN card
![]()
Question 85.
Pick the odd one out: (Credit card Operations)
(a) Bearer
(b) Publisher
(c) Merchant
(d) Acquirer
Answer:
(b) Publisher
Question 86.
Pick the odd one out:
(a) Visa
(b) Master card
(c) ATM card
(d) Rupay
Answer:
(c) ATM card
![]()
Question 87.
Pick the odd one out: (Electronic Account Transfer)
(a) DNS
(b) ECS
(c) EFS
(d) RTGS
Answer:
(a) DNS
Question 88.
Based on the monetary value e payment system can be classified into:
(a) Micro and Macro
(b) Micro and Nano
(c) Maximum and Minimum
(d) Maximum and Macro
Answer:
(a) Micro and Macro
Question 89.
Which of the following is not a category of micropayment?
(a) Buying a movie ticket
(b) Subscription to e journals
(c) Buying a laptop
(d) Paying for smartphone app
Answer:
(d) Paying for smartphone app
![]()
Question 90.
Assertion (A):
Micro electronic payment systems support higher value payments.
Reason (R):
Expensive cryptographic operations are included in macro payments.
(a) Both A and R are correct and R is the correct explanation of A .
(b) Both A and R are correct, but R is not the correct explanation of A
(c) A is true and R is false
(d) A is false and R is true
Answer:
(d) A is false and R is true
Question 91.
Which of the following is correctly matched?
(a) Credit Cards – pay before
(b) Debit Cards – pay now
(c) Stored Value Card – pay later
(d) Smart card – pay anytime
Answer:
(b) Debit Cards – pay now
Question 92.
ECS stands for:
(a) Electronic Clearing Services
(b) Electronic Cloning Services
(c) Electronic Clearing Station
(d) Electronic Cloning Station
Answer:
(a) Electronic Clearing Services
![]()
Question 93.
Which of the following is not a Altcoin?
(a) Litecoin
(b) Namecoin
(c) Ethereum
(d) Bitcoin
Answer:
(c) Ethereum
Question 94.
Which of the following is true about Virtual payment address (VPA)?
(a) Customers can use their e-mail id as VPA
(b) VPA does not includes numbers
(c) VPA is a unique ID
(d) Multiple bank accounts cannot have single VPA
Answer:
(c) VPA is a unique ID
Question 95.
Pick the odd one in the credit card transaction:
(a) card holder
(b) merchant
(c) marketing manager
(d) acquirer
Answer:
(c) marketing manager
![]()
Question 96.
Which of the following is true about debit card?
(i) debit cards cannot be used in ATMs
(ii) debit cards cannot be used in online transactions
(iii) debit cards do not need bank accounts
(a) (i), (ii), (iii)
(b) (ii), (iii), (iv)
(c) (iii) alone
(d) (iv) alone
Answer:
(d) (iv) alone
Question 97.
debit cards and credit cards are identical in physical properties
|
List A |
List B |
| (A1) First Digit | (B1) Account number |
| (A2) 9th to 15th Digit | (B2) Mil Code |
| (A3) First 6 Digits | (B3) BIN Code |
| (A4) Last Digit | (B4) Check digit |
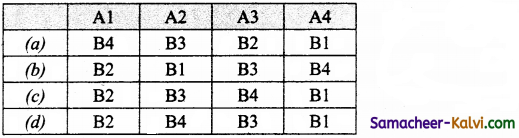
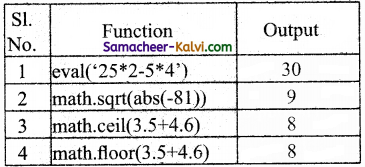
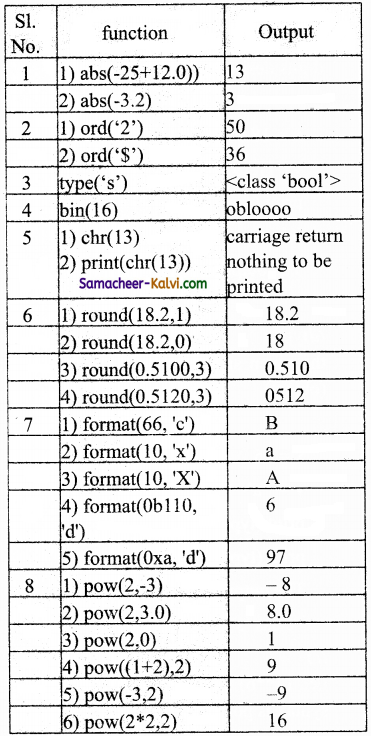
Answer:
(d)