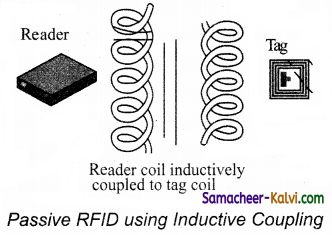
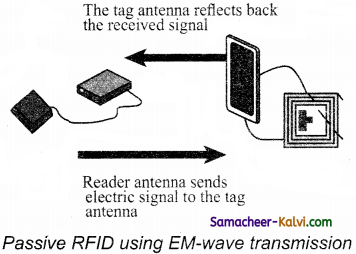
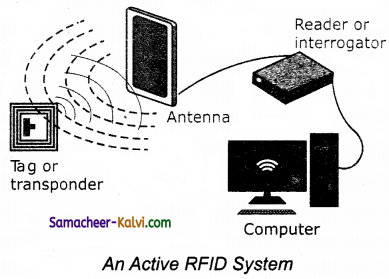
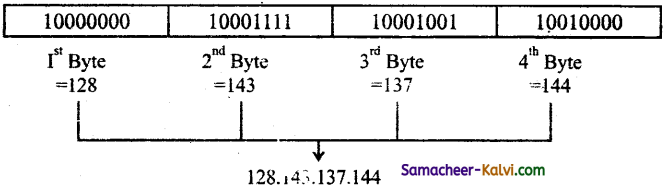
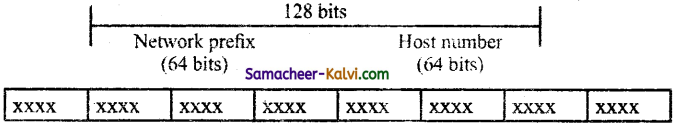
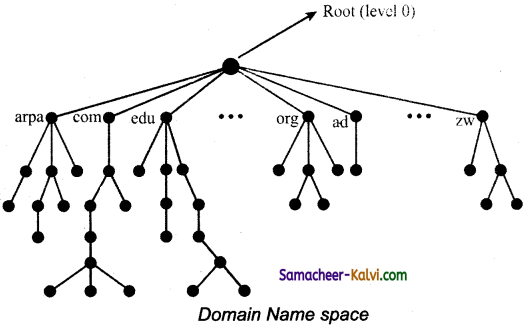
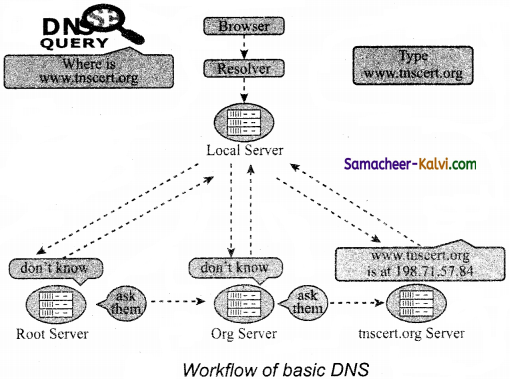
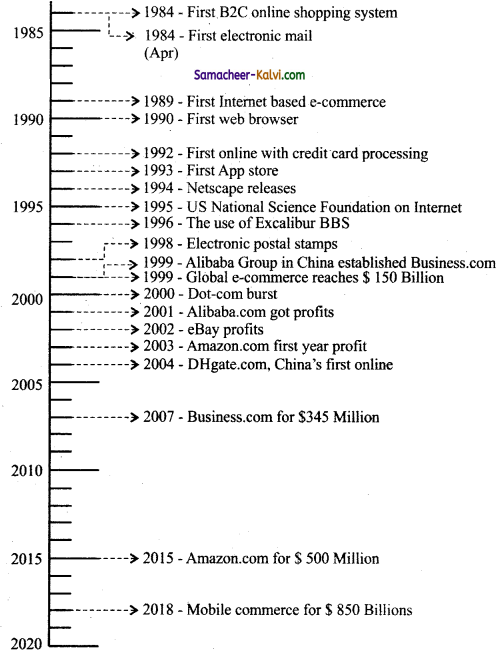
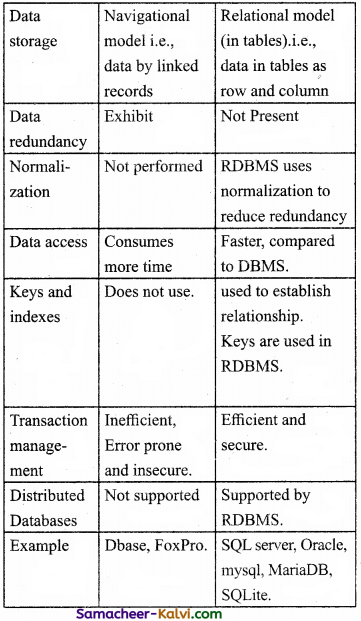
TN State Board 12th Computer Applications Important Questions Chapter 10 Introduction to Computer Networks
Question 1.
List the shared resources in internet.
Answer:
- Some of the shared resources are file server, web camera, speakers, printer, scanner, fax machine etc.,
- Accessing services such as WWW, digital audio, digital video which are shared to use applications, software and storage services.
Question 2.
What is nodes?
Answer:
Computer which is connected to network called as nodes. The data originates and terminates at these particular nodes is called as a source and destination.
![]()
Question 3.
What is 5G?
Answer:
- 5G (Fifth Generation), the industry of telecommunication has been hard working on the development of their next generation “5G” cellular communication technology.
- This 5G intense to boost up the speed the mobile connections dramatically.
Question 4.
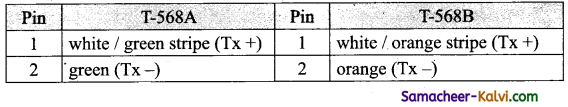
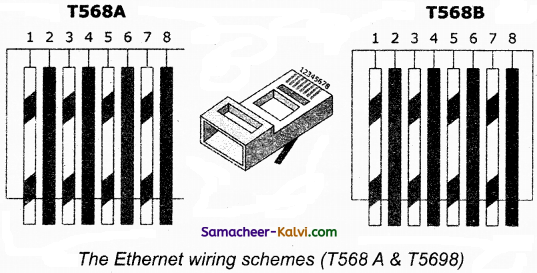
What is Ethernet?
Answer:
A system for connecting a number of computer systems to form a local network, with protocols to control the passing of information and to avoid simultaneous transmission by two or more system.
Question 5.
What is Hosts?
Answer:
- A network hosts is a computer connected to a computer network. A host may work as a server offering information resources, services and applications to users or other nodes on the network.
- Hosts are assigned at least one network address.
![]()
Question 6.
What are online service providers?
Answer:
Online service providers are Flipkart, Amazon, Snap deal etc., to buy • products via internet and have the product at door steps.
Question 7.
What is E-Governance?
Answer:
E-Govemance (Electronic governance) is the application of information and communication technology for delivering government services, exchange of information, communication transactions and services between govemment- to-citizen.
Question 8.
What is E-banking?
Answer:
E-banking (Electronic banking) is a product designed for the purpose of online banking that enables you to have easy and safe access to your bank account.
Question 9.
Define merchandising.
Answer:
Merchandising is to makes merchant an easier to get a specific type of products, company, brand can be done easier via internet.
![]()
Question 10.
Write some internet powerful search engine?
Answer:
The some internet powerful search engine are internet explorer, yahoo, bing and later, google stepped in with user friendly gmail, youtube, google drive, google maps etc.,
Question 11.
What are two things have marked its evolution of internet growing?
Answer:
The two things have marked its evolution of internet growing now a days are mobile technology and social web.
Question 12.
What are plays powerful communication computer networks?
Answer:
Using computer networks can easily communicate at very low cost via mobile, social media, Telephone, e-mail, chatting, video telephone, video conferencing, skpye, sms, mms, whatsapp, groupware etc.,
Question 13.
What is resources sharing?
Answer:
Resource sharing means one device accessed by many systems via network.
![]()
Question 14.
What are resource sharing devices available?
Answer:
Resource sharing is sharing such as printers, scanners, PDA, Fax machine and modems etc.,
Question 15.
What is cloud computing?
Answer:
A cloud computing means storing and accessing data and programs over the internet instead of your computer’s hard drive.
Question 16.
What is usage of cloud computing?
Answer:
- The usage of latest technologies as cloud computing are being used to allow globally without sacrifying security or limiting user access.
- Here on internet conversations happen faster, quick decision making saves a lot of time.
Question 17.
What are the method easily done to pay or receive payments?
Answer:
There are two methods commonly used using internet, they are gateways and online payments.
![]()
Question 18.
What are the business easily done using internet?
Answer:
Company renewals, license, other certificates, bill payments, receipts, invoice, stock manitenance etc., can be done without any geographical boundaries using internet.
Question 19.
What are advantages using internet for business man?
Answer:
- Direct human interactions are reduced using internet.
- Buyer directly purchase any product from manufacturer with lowest cost, middle person brokerage charges are reduced.
Question 20.
What are devices used networks at home?
Answer:
Network at home is a group of devices such as computers, mobile, speakers, camera, game system,’and printer that connect via network with each other.
![]()
Question 21.
What are ways to connected networks at home?
Answer:
Networks at home were connected in two ways they are
- Wired network
- Wireless network
Question 22.
Define wired network.
Answer:
A wired netw ork system connected with network cable. Eg: speakers, CCTV, printers, outdoors, and scanners etc., with cables (Wi-Fi).
Question 23.
Define wireless network.
Answer:
A wireless network is connecting devices like tablets (tab), indoor cameras and E-readers etc., without cable.
Question 24.
What are main role plays network at home?
Answer:
Network at home plays main role to access all such as e-banking, e-leaming, e-govemance, e-health, telemedicine, telemarketing, callcenters, video conferencing, digitalization of memories, can easy to access and use by avoiding lot of time and stacked at queue.
![]()
Question 25.
What is mobile network?
Answer:
Mobile network is the network connecting devices without cable (wireless).
Question 26.
What are devices used fixed transceivers and moving via more than one cell during transmission?
Answer:
Mobiles, Tablets, Pagers, Laptops, Engaged with Mobile broadband just like Modems etc.,
Question 27.
List out the social network media.
Answer:
Social network media are Whatsapp, Facebook, Twitter, Blogs, Pinterest, Linkedln, Classmates and so on.
Question 28.
List out the social network attributes.
Answer:
Social networks share several attributes in common they are membership, content contribution, frequent return visits, human relationship building.
![]()
Question 29.
What is flame wars?
Answer:
When we have mixed group of people coming together online, many discussions arise which lead to personal attacks called flame wars.
Question 30.
What is cloud storage?
Answer:
- Cloud storage is a service model in which data is maintained, managed, backup remotely and made available to users over a network.
- Just a storage of data on online, access in different area no geographical limits was in neeed.
Question 31.
What is E-Readers?
Answer:
E-Readers is similarly called as e-book reader these were designed for the purpose of reading via mobile electronics device to read digital e-books and periodically.
Question 32.
What is WWW?
Answer:
The WWW (World Wide Web) is combination of all resources and users on the internet that are using the Hyper Text Transfer Protocol (HTTP).
The World Wide Web is the universe of network accessible information, an embodiment of human knowledge.
![]()
Question 33.
Write short note on development on mobile networks.
Answer:
- The first generation (1G) mobile wireless communication network was analog used for voice calls only.
- The second generation (2G) is a digital technology and supports text messaging.
- The third generation (3G) mobile technology provided higher data . transmission, rate, increased capacity and provide multimedia support.
- The fourth generaion (4G) LTE (Long Term Evolution) provides in addition to the usual voice and other services, but not reached many parts of the world.
- The fifth generation (5G) is a currently under development of their next generation. 5G intense to boost up the speed the mobile connections dramatically.
Question 34.
Write short notes on SABRE.
Answer:
- SABRE (Semi Automatic Business Research Environment) at commercial Airline Reservation System online connected with two main frame computers.
- Packets switching was developed by Paul Baran and Donald devices to transfer the information between computers and networks.
- NPL (National Physical Laboratory) network at United Kingdom Local Area Network (LAN) using line speed of 768 kbit/s was implemented by Davies Pioneered.
![]()
Question 35.
Write INTERNET stands for
Answer:
- INTERNET – INTERnational NETwork (Technology, telecom, intelligence)
- INTERNET – INTERconnected computerNETwork (science, space and environment)
- INTERNET – Interesting Notions Transmitted Electronically Round Newly Engineered Technology.
Question 36.
Write the steps of disadvantages of Internet.
Answer:
- Simply wasting the precious time on internet by surfing, searching unwanted things.
- Lot of unnecessary information is also there, why because anyone can post anything on their webpage, blogs.
- Hackers and viruses can easily theft our more valuable information available in the internet. There a lot of security issues are there in E-banking.
Question 37.
Write a short note on mobile networks.
Answer:
- Mobile network is the network connecting devices without cable (wireless).
- Mobile computers, such as laptop, tablet, and hand held computers, were fastest growing segments.
- At land ares network was distributed as cells, each will be served by single location transceiver, but generally three cells sites or a base transceiver station.
- The base station provides the cell with network coverage and other features that can be utilized for transmission of voice, data and other content as well.
![]()
Question 38.
Expand the following.
(i) SAGE
(ii) SABRE
(iii) ARPANET
(iv) ARCNET
Answer:
(i) SAGE – Semi Automatic Ground Environment
(ii) SABRE – Semi Automatic Business Research Environment.
(iii) ARPANET – Advanced Research Projects Agency Network.
(iv) ARCNET – Attached Resource Computer NETwork.
Question 39.
Briefly explain internet explosion.
Answer:
- Internet is simply defined as the World Wide Web connection of individual networks which operated by academic, industry, governments, and private parties.
- The internet served to interconnect with laboratories engaged at government research, and from 1994 it is expanded to serve millions of user and a multiple purpose in all parts of this universe.
- Internet promotes as the universal source of information of billions of people, at work, at home, at school.
- Mobile technology on hand made possible to great reach of internet and increase the internet user all over the world.
- The internet allows all to be democratic in mass media. Anyone can have a webpage in internet with very low investment.
- Almost anyone that who can read and write can have a access and a presence in World Wide Web very low investment.
- People everywhere can express and publish their ideas and opinions via blogging.
![]()
Question 40.
Explain growth of business using networks.
Answer:
- Networks are necessary for successful business operations and technology for the business interaction.
- Now a days computer networks were faster, the communication has been transformed the way of business performed.
- By the usage of latest technologies, such as cloud computing are being used to allow globally without sacrifying security or limiting user access.
- On the way of e-banking we already have seen that we can pay or receive money from or to the customer may be easily done via gateways or by online payments were much easier on this method.
- Government subsidies were available for their business to promote their business by digitalization.
- Direct human interactions are reduced because of internet.
- Buyer directly purchase any product from manufacturer with lowest cost, middle person brokerage charges are reduced.
Question 41.
Mention some features of mobile networks.
Answer:
- Mobile device is less consumption of power is used comparing with a single transmitter or satellite often cell towers were nearer.
- Huge capacity than a large transmitter, at single frequency can be used for different or many links as long as they are in different cells.
- Covering large area than a single transmitter, we can add more towers indefinitely and cannot be limited by any horizon limits.
- Private cellular networks can be used at various locations like research and about large organizations and small industries, likely as public safety agencies.
- Even though all the service provider giving internet cannot make a reach to computer.
- When the reach of mobile it makes all to access the internet via mobile or cellular phone reaches the network easier to access.
- Where ever we go, we can access to easily.
![]()
Question 42.
Explain the attributes of social networks for sharing to common people.
Answer:
(i) Membership:
- Social nets all generally requires user to register names and accounts for duplicate and secrecy.
- Many public networks offer free registration, but some charge fees for their premium services.
- Private networks restrict registration to people who meet certain eligibility criteria.
(ii) Content contribution:
Networks allows members to easily share comments, movies, music, short films and / or photos with others.
(iii) Frequent return visits:
Healthy social net takes a centers around a base of members who check in regularly to contribute theirs and also for new updates.
(iv) Human relationship building:
The common goal of most social networks is allowing the interactions that build stronger connections within communicates of people.
![]()
Question 43.
Explain usefulness of social networks.
Answer:
(i) Group information sharing over long distances:
- Friends and family members can keep in contact via mobile phone calls or by text messages, social net suggestion a much richer environment for staying connected.
- Many scenarios such as sharing photo, albums, video or convey their wishes someone, work better these networks because an entire group can participate together with one.
(ii) Broadcast announcements:
- Cities can more comfort to spread work of emergencies and natural calamities.
- Venues and local shops can advertise upcoming events on social networks.
(iii) Fostering diversity of thought:
- Some critics of social networks point out that online communities attract people by similar interests and backgrounds.
- When we have mixed group of people coming together online, many discussions arise which lead to personal attacks called flame wars.
![]()
Question 44.
Define Computer Network.
Answer:
- A set of computers connected together for the purpose of sharing resources is called as computer network.
- At present, Internet is the most common resource shared everywhere.
Question 45.
Define internet.
Answer:
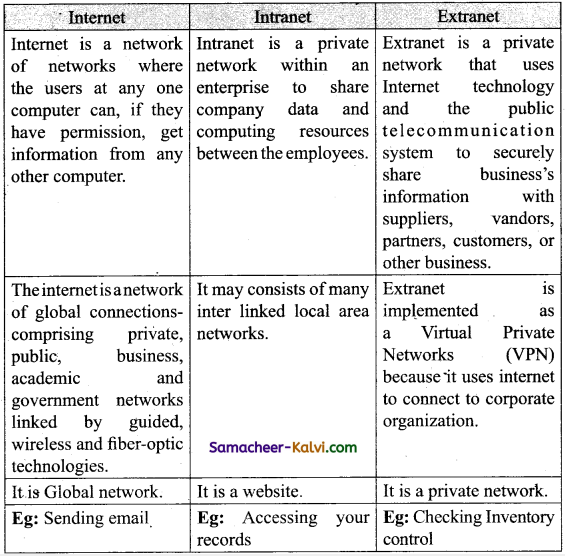
Networks of network is called Internet.
The internet is a global wide area network that connects computer systems across the world. And exchanges private, public, business, academic and- government networks.
Question 46.
What are the common uses of computer network?
Answer:
The common uses of computer networks are
- Communication
- Resource sharing
- Data or software sharing
- Money saving
![]()
Question 47.
List out same features of mobile network.
Answer:
- Less consumption of power is used in mobile devices.
- Huge capacity than a large transmitter, at single frequency can be used for different in cells.
- Covering large area than a single transmitter, we can add more towers indefinitely.
Question 48.
Difference between wired and wireless networks.
Answer:
|
Wired Network |
Wireless Network |
| A wired network system connected with network cable. | A wireless network is connecting device like tablets (tab). |
| Eg: Speakers, CCTV, Printers, outdoors and Scanners etc., with cable (Wi – Fi) | Eg: Indoor cameras and E – readers etc., without cables. |
Question 49.
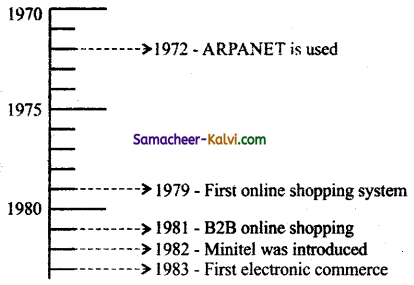
Define ARPANET.
Answer:
- ARPANET (Advanced Research Projects Agency Network) was the network that became the basis for the internet.
- ARPANET was an early packet-switching network and the first network to implement the TCP / IP protocol.
- ARPANET was developed under the direction of the U.S. Advanced Research Projects Agency (ARPA).
- In 1969, the idea became a modest reality with the interconnection of four university computers.
![]()
Question 50.
What is the usage of cloud storage and cloud computing?
Answer:
- Cloud storage is simply storing data and files, and performing backups to an external location offsite.
- Cloud storage, data is stored on a virtual server, not the employees actual devices.
- Cloud computing is running applications through a virtual desktop over a secure internet connection.
- Cloud computing, No special hardware requirements. The ability to access apps and data from just about anywhere on just about my device.
- Combining cloud storage with cloud computing provides companies the benefits of both services.
Question 51.
Explain the growth of the computer networking.
Answer:
(i) The growth of the computer networking technology was developing in very interesting and fastest way.
(ii) Growth on popularity of cloud storage and cloud computing. On behalf of buying physical copies of games, music and movies, increasingly downloading and buy digital licenses their need via Internet.
(iii) Developments on mobile network infrastructure that have allow the people in their developed areas who can allow it to their developed areas who can allow it to their smart mobile phones as video broadcasting system and as mobile television.
(iv) Some of the people underlying and staying connected all the times, whenever they at the workplace, via a home network, via public Wi-Fi hotspot or smart phones.
(v) “5G” (fifth generation)cellular communication technology, this 5G intense to boost up the speed the mobile connections dramatically.
(vi) Artificial Intelligence (AI) will help to maintain, manage, and protect it.
(vii) Artificial network is powering algorithms will become most intelligent; it might find faster and reliable methods of anticipating threats and cleaning networks.
(viii) Artificial intelligence able to be a better predict traffic as it collects and analyzes data in real time, some of network managers were better prepared for big events such as the worldcup, Olympics, valentine’s day, which often put on the Internet under pressure.
![]()
Question 52.
Mention some uses of network at business, home, mobile, social application.
Answer:
The computer networks plays major role on providing information to large, small organization as well as individual common man.
(i) Network in Business:
- In Twenty first centuries communications is necessary for successful business operations and technology for the business interaction.
- We all know that “time is money” in business. On the way of e-banking, we can pay or receive money from or to the customer may be easily done via gateways or by online payments were much easier.
- Commercial information, cheaper marketing, comparison of product can be very easier now a days.
- Company renewals, licence, other certificates, bill payments, receipts, invoice, stock maintenance, can be done without any geographical boundaries required here on doing via Internet and computer networks.
(ii) Network at home:
- Network at home were connected in two ways they are wired network and wireless network.
- Network at home plays main role to access all such as e e-learning, e-govemance, e-health, telemedicine, callcenters, video conferencing, digitalization of memories, can easy to access and use by avoiding lot of time and stacked at queue.
Mobile Networks:
- Mobile network is the network connecting devices without cable.
- Mobile network is used for searching some important points, checking mail can be done, watching the progress can be easier on this way. Computer knowledge not necessary to easily access the internet via mobile network.
(iv) Social Application:
- Social network media is very fast and easiest way to cover the all the people, who they are connected in network.
Eg: Whatsapp, Facebook, Twitter, Blogs, Pinterest, Linkedln, classmates and so on. . - Through the above social media we share our thoughts in diffr^nt formats and different size of files. The corporate also ores intram
- Usefulness of social networks are group information sharing ove’ long distance, Broadcast announcements, fostering diversity 01 thoughts etc.,
![]()
Question 53.
List out the wireless network?
Answer:
- Wireless PAN (Personal Area Network)
- Wireless LAN (Local Area Network)
- Wireless Adhoc Network.
- Wireless MAN (Metropolitan Area Network)
- Cellular Network.
- Global Area Network.
- Space Network
Question 54.
Find out how your family members and public members uses the network?
Answer:
Our family members using computer networks on mobiles. My mother using youtube by searching on videos for different cooking. My younger brother playing network gaming and other entertainments. My father to access network for email, paying phone bill, electricity bill, corporation taxes and other E-Govemance, E-banking etc., My elder sister using network for video conferencing with his friends and searching research materials for her higher studies. Myself using social media and ordered delicious food from various hotels.
The public members are probably using network for mail searching, Social media, Reservation Ticket Booking etc., Now a days on this current situation of people are using individual networks such as mobile, tab etc.,
(Students are requested to write about your family members and nearer people Using network).
![]()
Question 55.
Instead of landline (wired network) what were the types of wireless network you know.
Answer:
- Wireless LAN
- Cellular network
Question 56.
Some of example devices with wireless networks.
Answer:
Tablets (tab), Indoor cameras, E-readers, Laptops, Smartphones, Bluetooth etc.,
Question 57.
How social media has its memory management?
Answer:
- Social media has shared memory, it provides a buffer-type functionality that speeds up the delivery of temporal/historical data.
- The main idea is to have a central point in the memory(RAM) of the platform that will manage and provide a temporal/ historical data.
![]()
Question 58.
Do you have a account on social media (or) create an account.
Answer:
If you have social media account you can use social media through registered login id and password.
Create an account in social media for example to create an account in facebook should follow the steps.
(i) Go to facebook.com / r. php (Displaying registration form)
(ii) Enter the new login name go by in everyday life.
(iii) Enter your date of birth.
(iv) Enter the mobile number, to use email instead of mail or sign-up with email.
(v) Tap male or female to select your gender.
(vi) Choose a password and tap signup.
(vii) If we finish creating an account, we need to confirm our email or mobile numbers.
Using Facebook account, we can create other social media accounts.
Question 59.
Analyse how the social media applications transfer a huge data.
Answer:
(i) Social media is defined as web-based and mobile based internet applications.
(ii) Social media data is clearly the largest, richest and most dynamic guidance base of human behaviour, bringing new opportunities to understand individuals, groups and society.
(iii) All the status updates, pictures and videos posted by the people on their social media contains information.
(iv) These user behaviour data – can be transferred via applications for individual or business purposes.
(v) For example, facebook collects information from all devices that we have installed it or access its service from do depending on the permission, it will collect things from our devices like location via GPS, time zone etc., This information are collected as data, these datas can be used for individual, public and commercial purpose.
![]()
Choose the correct answer:
Question 1.
Networks of network is called:
(a) WAN
(b) MAN
(c) Internet
(d) LAN
Answer:
(c) Internet
Question 2.
What is called computer networking exchanges the data with each other through wired or wireless connections between different terminals?
(a) Nodes
(b) Internet
(c) Networking
(d) All of these
Answer:
(a) Nodes
Question 3.
Which one of the following cable media which is transferred the data through wires?
(a) WAN
(b) Nodes
(c) MAN
(d) Fiber optics
Answer:
(d) Fiber optics
![]()
Question 4.
An example of wireless media:
(a) cable
(b) Wi-Fi
(c) nodes
(d) All of these
Answer:
(b) Wi-Fi
Question 5.
Which is identified by networking nodes?
(a) Computer name
(b) Server name
(c) Mail address
(d) IP addresses
Answer:
(d) IP addresses
Question 6.
Which is called connecting more than one computer?
(a) Server
(b) Hub
(c) Node
(d) Network
Answer:
(d) Network
![]()
Question 7.
Who were developed by packet switching?
(a) Paul Baran
(b) Donald devices
(c) Both (a) and (b)
(d) Vintcerf
Answer:
(c) Both (a) and (b)
Question 8.
Which company was introduced first telephone switch?
(a) Western electric
(b) European electric
(c) Southern electric
(d) West European electric
Answer:
(a) Western electric
Question 9.
Expand ARPANET:
(a) Advanced Research Project Agency Network.
(b) American Research Project Agency Network.
(c) Australian Research Project Agency Network.
(d) All Research Project Agency Network.
Answer:
(a) Advanced Research Project Agency Network
![]()
Question 10.
Expand ARCNET:
(a) Advanced Research Computer Network.
(b) Attached Resource Computer Network.
(c) American Research Computer Network.
(d) All Resource Computer Network.
Answer:
(b) Attached Resource Computer Network
Question 11.
How many nodes were connected by ARPANET in 1969?
(a) 2
(b) 3
(c) 4
(d) 5
Answer:
(c) 4
Question 12.
Which French network named was the first for making hosts?
(a) Western Electric
(b) French Network
(c) Cyclades
(d) Normalades
Answer:
(c) Cyclades
![]()
Question 13.
Which is responsible for reliable delivery of data?
(a) Hosts
(b) HUB
(c) Node
(d) Server
Answer:
(a) Hosts
Question 14.
Which was created by John Murphy of data point corporation?
(a) ARPANET
(b) ARCNET
(c) ETHERNET
(d) HOSTS
Answer:
(b) ARCNET
Question 15.
Which was token passing network used first to share the storage device in 1976?
(a) ARCNET
(b) ETHERNET
(c) ARPANET
(d) HOSTS
Answer:
(a) ARCNET
![]()
Question 16.
INTERNET stands for:
(a) ESITER national NETwork
(b) INTER connected computer NETwork.
(c) Interesting Notions Transmitted Electronically Round Newly Engineered Technology
(d) All of these
Answer:
(d) All of these
Question 17.
Which is made easier to collect their certificates through online?
(a) E-Banking
(b) E-Govemance
(c) E-Leaming
(d) E-Business
Answer:
(b) E-Govemance
Question 18.
Which was can easily theft our more valuable information available in the Internet?
(a) Hackers
(b) Viruses
(c) (a) and (b)
(d) Anti-viruses
Answer:
(c) (a) and (b)
![]()
Question 19.
Which cellular communication technology to boost up the speed the mobile connections dramatically?
(a) 2G
(b) 3G
(c) 4G
(d) 5G
Answer:
(d) 5G
Question 20.
Which will help to maintain, manage, and protect mobile networks?
(a) Cloud computing
(b) Artificial Intelligence (AI)
(c) Browsers
(d) Hackers
Answer:
(b) Artificial Intelligence (AI)
Question 21.
Which method is powering algorithms will become most intelligent and . anticipating threats and cleaning networks?
(a) Artificial Network
(b) Cloud computing
(c) Browsers
(d) Hackers
Answer:
(a) Artificial Network
![]()
Question 22.
What does sharing means one device accessed by many system?
(a) Communication
(b) Resource
(c) Data
(d) Money
Answer:
(b) Resource
Question 23.
What will be stored at central computer or server, when using computer network?
(a) Software
(b) Data sharing
(c) Resources sharing
(d) All of these
Answer:
(d) All of these
Question 24.
Which are being used to allow globally without sacrifying security or limiting user access?
(a) Cloud computing
(b) Server
(c) Hub
(d) Node
Answer:
(a) Cloud computing
![]()
Question 25.
What is known as that we can pay or receive money from or to the customer may be easily done?
(a) gate ways
(b) online payment
(c) (a) or (b)
(d) cheque
Answer:
(c) (a) or (b)
Question 26.
What does to promote their business used by government subsidies?
(a) Digitalization
(b) Server
(c) Software
(d) Computer
Answer:
(a) Digitalization
Question 27.
What does can access more than one person in one device?
(a) Network
(b) Router
(c) Datacard
(d) (b) or (c)
Answer:
(d) (b) or (c)
![]()
Question 28.
Which of the following is not wired network system? ’
(a) E-readers
(b) Speakers
(c) CCTV
(d) Scanners
Answer:
(a) E-readers
Question 29.
Which of the following is used wireless network?
(a) E-readers
(b) Speakers
(c) CCTV
(d) Scanners
Answer:
(a) E-readers
Question 30.
Which can be used, from the home we ordered delicious food from various hotels and restaurants at time without delay?
(a) Internet
(b) Networks
(c) Browsers
(d) Data card
Answer:
(a) Internet
![]()
Question 31.
Which network is the network connecting devices without cable?
(a) Internet
(b) Mobile
(c) Cloud computing
(d) Server
Answer:
(b) Mobile
Question 32.
Which will provides the cell with network coverage and other features that can be utilized for transmission of voice, data and other content as well?
(a) Base transceiver station
(b) Server
(c) Cloud computing
(d) Internet
Answer:
(a) Base transceiver station
Question 33.
Which is used to communicate with one another with fixed transceivers and moving via more than one cell during transmission?
(a) Base transceiver station
(b) Portable transceivers
(c) Cloud computing
(d) Server
Answer:
(b) Portable transceivers
![]()
Question 34.
Which is very fast easiest way to cover all the people?
(a) Server
(b) Cloud computing
(c) Social media
(d) Datacard
Answer:
(c) Social media
Question 35.
Which of the following one is not a social media?
(a) LinkedIn
(b) Twitter
(c) Blogs
(d) Tablets
Answer:
(d) Tablets
Question 36.
Which is requires user to register names and accounts for avoid duplicate and secrecy in social nets?
(a) Membership
(b) Content contribution
(c) Frequent return visits
(d) Human relationship building
Answer:
(a) Membership
![]()
Question 37.
Which is allows members to easily share comments, music, photos etc., with others?
(a) Membership
(b) Content contribution
(c) Frequent return visits
(d) Human relationship building
Answer:
(b) Content contribution
Question 38.
What does healthy social net takes a centers around a base of members who check in regularly to contribute theirs?
(a) Membership
(b) Content contribution
(c) Frequent return visits
(d) Human relationship building
Answer:
(c) Frequent return visits
Question 39.
Which is common goal of most social networks is allowing the interactions that build stronger connections with in communities of people?
(a) Membership
(b) Content contribution
(c) Frequent return visits
(d) Human relationship building
Answer:
(d) Human relationship building
![]()
Question 40.
When we have mixed group of people coming together online, many discussions arise which lead to personal attacks called:
(a) Flame wars
(b) Hacking
(c) Viruses
(d) None of these
Answer:
(a) Flame wars
Question 41.
Match the following:
| (A) Bluetooth | (i) shared resources |
| (B)node | (ii) wireless |
| (C) IP address | (iii) terminals |
| (D) printer | (iv) Network addresses |
(a) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
(b) (A) – (ii); (B) – (iv); (C) – (i); (D) – (iii)
(c) (A) – (iii); (B) – (ii); (C) – (i); (D) – (iv)
(d) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
Answer:
(a) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
Question 42.
Match the following:
| (A) SAGE | (i) Token-passing Network |
| (B) SABRE | (ii) Hierarchical routing |
| (C) ARPANET | (iii) NPL network |
| (D)ARCNET | (iv) US Military Radar |
(a) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
(b) (A) – (iii); (B) – (ii); (C) – (i); (D) – (iv)
(c) (A) – (iv); (B) – (iii); (C) – (ii)- (D) – (i)
(d) (A) – (iv); (B) – (i); (C) – (ii); (D) – (iii)
Answer:
(c) (A) – (iv); (B) – (iii); (C) – (ii)- (D) – (I)
![]()
Question 43.
Match the following:
| (A)Yahoo | (i) online providers |
| (B) gmail | (ii) unauthorized access |
| (C) Hackers | (iii) search Engine |
| (D) Flipkart | (iv) mailing operations |
(a) (A) – (iii); (B) – (ii); (C) – (i); (D) – (iv)
(b) (A) – (iii); (B) – (iv); (C) – (ii); (D) – (i)
(c) (A) – (ii); (B) – (iv); (C) – (i); (D) – (iii)
(d) (A) – (ii); (B) – (i); (C) – (iii); (D) – (iv)
Answer:
(b) (A) – (iii); (B) – (iv); (C) – (ii); (D) – (i)
Question 44.
Match the following:
| (A) Communication | (i) Reduce paper |
| (B) Resource sharing | (ii) e – mail |
| (C) Data sharing | (iii) PDA |
| (D) Money sharing | (iv) Back up |
(a) (A) – (ii); (B) – (iv); (C) – (i); (D) – (iii)
(b) (A) – (iii); (B) – (ii); (C) – (i); (D) – (iv)
(c) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
(d) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
Answer:
(c) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
Question 45.
Match the following:
| (A) Whatsapp | (i) 2004 |
| (B) Facebok | (ii) 2002 |
| (C) Twitter | (iii) 2009 |
| (D) Linkedln | (iv) 2006 |
(a) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
(b) (A) – (iii); (B) – (ii); (C) – (iv; (D) – (i)
(c) (A) – (ii); (B) – (iv); (C) – (i); (D) – (iii)
(d) (A) – (ii); (B) (i); (C) – (iii); (D) – (iv)
Answer:
(a) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
![]()
Question 46.
Choose incorrect pair:
(a) Network – sharing
(b) Internet – Network
(c) Wi-Fi – node
(d) IP addresses – Network addresses
Answer:
(c) Wi-Fi – node
Question 47.
Choose incorrect pair:
(a) Paul Baran – Packet switching
(b) WAN – Lawrence Roberts
(c) Ethernet – Robert metcalfe
(d) ARCNET – John Murphy
Answer:
(b) WAN – Lawrence Roberts
Question 48.
Choose the incorrect pair:
(a) Bing – Browser
(b) Facebook – Social web
(c) DDos1 Hacks
(d) MMS – Networks
Answer:
(d) MMS – Networks
![]()
Question 49.
Choose the incorrect pair:
(a) 1G -1 GB / s
(b) 2G – 64 kb / s
(c) 3G – 2 mb / s
(d) 4G -100 mb / s
Answer:
(a) 1G -1 GB / s
Question 50.
Choose the incorrect pair:
(a) CCTV – Wired network
(b) Indoor cameras – Wireless network
(c) e-market – Online shopping
(d) mobile – Social Network
Answer:
(d) mobile – Social Network
Question 51.
Choose the correct pair:
(a) WWW – Accessing server
(b) Bluetooth – Server
(c) Network – Software
(d) Data – Server
Answer:
(a) WWW – Accessing server
Question 52.
Choose the correct pair:
(a) SABRE – Mainframe
(b) Packet switching – Reservation
(c) WAV – Resource sharing
(d) Arecnet – time sharing
Answer:
(a) SABRE – Mainframe
![]()
Question 53.
Choose the correct pair:
(a) Cells – Wired Network
(b) Flame war – Abusive message
(c) Hosts – Service provider
(d) Malware – Hardware
Answer:
(c) Hosts – Service provider
Question 54.
Choose the correct pair:
(a) e-Govemance – online buying
(b) e-Banking – online certificate
(c) e-Readers – online purchase
(d) e-Waste – Unwanted electronic things
Answer:
(d) e-Waste – Unwanted electronic things
Question 55.
Choose the correct pair:
(a) Network – Resource
(b) Wi-Fi – Wireless Fidelity
(c) Blogging – virus
(d) Gmail – social media
Answer:
(b) Wi-Fi – Wireless Fidelity
![]()
Question 56.
Choose the incorrect statement:
(a) Digital Audio is a shared resource in internet.
(b) A set of computers connected together is called network.
(c) Computer networking is a technique of digital telecommunications network.
(d) Computer which is connected to network called as nodes.
Answer:
(a) Digital Audio is a shared resource in internet.
Question 57.
Choose the incorrect statement:
(a) Artificial intelligence will help to maintain, manage, and protect mobile networks.
(b) DDoS (Distributed Denial of Service) attacks and attempted backs.
(c) Artificial network are difficulties faced by the service provider.
(d) Artificial intelligence able to be a better predict traffic as it collects and analyzes data in real time.
Answer:
(c) Artificial network are difficulties faced by the service provider.
Question 58.
Choose the incorrect statement:
(a) Connecting more than one device is called as network.
(b) The well-known networking for all is Internet.
(c) Now a days the internet plays a vital role.
(d) Snap deal is a type of network in early days.
Answer:
(d) Snap deal is a type of network in early days.
![]()
Question 59.
Choose the incorrect statement:
(a Vint cerf is called Internet founding father.
(b) Lawrence Roberts is considered one of the father of the Internet.
(c) SAGE method was used as private online reservation system.
(d) Packet switching was developed by Paul Baran.
Answer:
(c) SAGE method was used as private online reservation system.
Question 60.
Choose the incorrect statement:
(a) NPL (National Physical Laboratory) at United Kingdom local area network.
(b) Integalactic computer Network was developed by J.C. RLicklider.
(c) First Telephone switch was introduced by Western electric.
(d) WAN (Wide Area Network) at Newyork local area network.
Answer:
(d) WAN (Wide Area Network) at Newyork local area network.
Question 61.
Choose the correct statement.
(a) E-Govemance made easier to bought products from online service providers.
(b) E-Banking plays an important role only in Merchandising.
(c) Internet Explorer is a search engine.
(d) Youtube is a service provider.
Answer:
(c) Internet Explorer is a search engine.
![]()
Question 62.
Choose the correct statement:
(a) Hackers and viruses can easily theft our more valuable information.
(b) Facebook was created in 2006.
(c) The Internet does not allows all to be democratic in mass media.
(d) Any one can have a webpage in internet with very high investment.
Answer:
(a) Hackers and viruses can easily theft our more valuable information.
Question 63.
Choose the correct statement:
(a) Resource sharing means one device accessed by single system.
(b) PDA is used as Data sharing.
(c) Networks at home were connected in four ways.
(d) CCTV is a wired network system.
Answer:
(d) CCTV is a wired network system.
Question 64.
Choose the correct statement:
(a) Mobile network is the network connecting devices without cable.
(b) Computer knowledge is must to access the internet through mobile.
(c) Blogs is a service provider.
(d) Classmates is one of the browser.
Answer:
(a) Mobile network is the network connecting devices without cable.
![]()
Question 65.
Choose the correct statement:
(a) The corporate also uses internets.
(b) Cloud storage is storage in hard disk.
(c) Cloud computing is to share resources, software and information.
(d) Hosts is a internet browser.
Answer:
(c) Cloud computing is to share resources, software and information.
Question 66.
Assertion (A):
ARPANET is the Hierarchical routing after 1970’s internet today.
Reason (R):
First in 1969, four nodes of ARPANET were connected between four universities using 50 k bits / s circuit.
(a) Both A and R are True, and R is the correct explanation for A.
(b) Both A and R are True, but R is not the correct explanation for A.
(c) A is True, but R is false.
(d) A is false, but R is true.
Answer:
(a) Both A and R are True, and R is the correct explanation for A.
Question 67.
Assertion (A):
Online service provides are filpkart, amazon, snapdeal etc., to buy products via internet and have the product at door steps.
Reason (R):
E-Governance made easier to collect their certificates through online.
(a) Both A and R are True, and R is the correct explanation for A.
(b) Both A and R are True, but R is not the correct explanation for A.
(c) A is True, but R is false.
(d) A is false, but R is true.
Answer:
(b) Both A and R are True, but R is not the correct explanation for A.
![]()
Question 68.
Assertion (A):
Internet promotes as the universal source of information of billions of people, at work, at home, at school.
Reason (R):
Google drive is used on internet by surfing, searching unwanted things.
(a) Both A and R are True, and R is the correct explanation for A.
(b) Both A and R are True, but R is not the correct explanation for A.
(c) A is True, but R is false.
(d) A is false, but R is true.
Answer:
(c) A is True, but R is false.
Question 69.
Assertion (A):
Resource sharing means one device accessed by one system.
Reason (R):
Using computer networks, we can interact with the different people with each other at all over the world. .
(a) Both A and R are True, and R is the correct explanation for A.
(b) Both A and R are True, but R is not the correct explanation for A.
(c) A is True, but Rjs false.
(d) A is false, but R is true.
Answer:
(d) A is false, but R is true.
Question 70.
Assertion (A):
Malware is a internet browser.
Reason (R):
Flame wars is called as virus.
(a) Both A and R are true.
(b) Both A and R are false.
(c) A is True, but R is false.
(d) A is false, but R is true.
Answer:
(b) Both A and R are false.
![]()
Question 71.
Which one of the following protocol is not used in internet?
(a) HTTP
(b) DHCP
(c) DNS
(d) None
Answer:
(d) None
Question 72.
Internet works on:
(a) Packet switching
(b) Circuit switching
(c) Both (a) and (b)
(d) None of these
Answer:
(a) Packet switching
Question 73.
Which protocol assigns IP address to the client connected in the internet?
(a) DHCP
(b) IP
(c) RPC
(d) DNS
Answer:
(a) DHCP
![]()
Question 74.
Bluetooth is the wireless technology for: ,
(a) Local Area Network
(b) Personal Area Network
(c) Both (a) and (b)
(d) None of these
Answer:
(b) Personal Area Network
Question 75.
An RPC (Remote Procedure Call) is initiated by the:
(a) server
(b) Client
(c) Both (a) and (b)
(d) None of these
Answer:
(b) Client
Question 76.
_______ allows LAN users to share computer program and data.
(a) Communication server
(b) Print server
(c) File server
(d) Network
Answer:
(c) File server
![]()
Question 77.
TCP /IP is a:
(a) Network hardware
(b) Network software
(c) Protocol
(d) None of these
Answer:
(c) Protocol
Question 78.
_______ are hardware and software combinations that connect devices running different native protocol.
(a) Protocol
(b) Models
(c) Gateways
(d) Ports
Answer:
(c) Gateways
Question 79.
Which agency assign IPs?
(a) IEEE
(b) ANST
(c) ICANN
(d) BSNL
Answer:
(c) ICANN
![]()
Question 80.
Which protocol is used for browsing website?
(a) TCP
(b) HTTP
(c) FTP
(d) TFTP
Answer:
(b) HTTP
Question 81.
Who was widely known as father of the Internet?
(a) Vint cerf
(b) Tim Berners Lee
(c) Robert E. Khan
(d) Lawrence Roberts
Answer:
(a) Vint cerf
![]()
Question 82.
Who was founding father of the Internet?
(a) Vint cerf
(b) Tim Berners Lee
(c) Robert E. Khan
(d) Lawrence Roberts
Answer:
(d) Lawrence Roberts
Question 83.
A set of computers connecting together is called as:
(a) Network
(b) Server
(c) Hub
(d) Node
Answer:
(a) Network
Question 84.
Computer network devices that originates route and terminate the data were called as:
(a) Hub
(b) Resource
(c) Node
(d) Cable
Answer:
(c) Node
![]()
Question 85.
Match the period and methods available on history of computer networking in the Internet:
| (a)1950 | (i) X.25 TCP/IP |
| (b) 1966 | (ii) SAGE |
| (c) 1976 | (iii) WAN |
| (d) 1972 | (iv) ARCNET |
(a) (A) – (iv); (B) – (iii); (C) – (ii); (D) – (i)
(b) (A) – (iii); (B) – (iv); (C) – (ii); (D) – (i)
(c) (A) – (D); (B) – (ii); (C) – (iii); (D) – (iv)
(d) (A) – (ii)); (B) – (iii); (C) – (iv); (D) – (i)
Answer:
(c) (A) – (D); (B) – (ii); (C) – (iii); (D) – (iv)
Question 86.
Western Electric introduced the first widely used ……………… that implemented true computer control.
(a) Packet switch
(b) Arpanet
(c) Host
(d) Telephone switch
Answer:
(d) Telephone switch
![]()
Question 87.
Wi-Fi is short name for:
(a) Wireless Fidelity
(b) Wired Fidelity
(c) Wired Fiber optic
(d) Wireless Fiber optic
Answer:
(a) Wireless Fidelity
Question 88.
People everywhere can express and publish their ideas and opinions via:
(a) Tele-medicine
(b) blogging
(c) Server
(d) Node
Answer:
(b) blogging
Question 89.
Which one of the following periods, the speed capacity supported towards gigabit on computer network?
(a) SABRE
(b) SAGE
(c) NEW FIBRE OPTICS
(d) ARCNET
Answer:
(c) NEW FIBRE OPTICS
![]()
Question 90.
One among them was challenging to the business people on computer networking:
(a) Hacking
(b) Viruses
(c) Both (a) and (b)
(d) none of this above
Answer:
(c) Both (a) and (b)
Question 91.
…………. able to predict, manage, and protect the computer network at Internet.
(a) Artificial intelligence
(b) Broadband provider
(c) Cloud computing
(d) Transceivers
Answer:
(a) Artificial intelligence
Question 92.
………… use less power comparing with single transmitter or satellite often cell towers nearer.
(a) Mobile devices
(b) Transistors
(c) WiFi
(d) Communication
Answer:
(a) Mobile devices
![]()
Question 93.
People now a days getting relaxed via:
(a) Business
(b) Corporate company
(c) News papers
(d) Social media
Answer:
(d) Social media
Question 94.
Which one of the following is not the social media?
(a) Gmail
(b) Facebook
(c) Twitter
(d) Linkedin
Answer:
(a) Gmail
Question 95.
Facebook was created at year.
(a) 2002
(b) 2004
(c) 2013
(d) 2010
Answer:
(b) 2004
![]()
Question 96.
In mobile network, land areas for network coverage was distributed as:
(a) Firmware
(b) cells
(c) Range
(d) Service
Answer:
(b) cells
Question 97.
Which one were harmful to computer?
(a) Bloggers
(b) Browser
(c) Hackers
(d) Twitter
Answer:
(c) Hackers
![]()
Question 98.
Which innovation made the people to use Internet?
(a) Social web
(b) Mobile technology
(c) Mobile App
(d) Both (a) and (b)
Answer:
(d) Both (a) and (b)