TN State Board 12th Computer Applications Important Questions Chapter 11 Network Examples and Protocols
Question 1.
Write the function of Internet Protocol (IP).
Answer:
- The main function is to allows Internet working an boost up the internet.
- Internet portocol will deliver packets from the source host and it will deliver to the destination host.
Question 2.
What is Network protocols?
Answer:
Network protocols is that the usual procedures, rules, formal standards and policies comprised of formats which allocates communication between more . than one device which connected to the network.
Question 3.
What is the unique aim of ARPA Net?
Answer:
ARPAC (Advanced Research Project Agency). The unique aim was to generate a network that would permit users of a research computer from one university to ‘talk to’ research computers on other universities.
![]()
Question 4.
What is Internet?
Answer:
A network of networks, where the users at any one computer can, if they have permission get information from any other computer. The Internet is a network of global connections.
Question 5.
What do you understand about Internet?
Answer:
The Internet denotes to the global communication system, including infrastructure and hardware, whereas the web is one of the services interconnected over the Internet.
Question 6.
What is Extranet?
Answer:
Extranet is a private network that uses Internet technology and the public telecommunication system to securely share business’s information with suppliers, vendors, partners, customers, or other businesses.
![]()
Question 7.
What is IoT?
Answer:
IoT (Internet of Things) is to the digital interconnection of everyday objects with the internet.
Eg: Home appliances, wearable devices, automobiles etc.,
Question 8.
What is refer ‘thing’ in IoT?
Answer:
The ‘thing’ in IoT refers to an objects that have been assigned an IP address and have the ability to collect and transfer data over a network without manual assistance or intervention.
Question 9.
What is called cells?
Answer:
A mobile network or cellular network as it is made up of a large number of signals areas called cells. These cells join to form a large coverage area.
![]()
Question 10.
Define Mobile base station.
Answer:
- A mobile device will connect to the nearest or least base station.
- The base stations are connected to digital exchange where the communication is sent to other telephone or data networks.
Question 11.
What is SIM?
Answer:
SIM (Subscriber Identity Module) technology to authenticate a user for identification and billing purposes, and to encrypt the data to prevent listen without permission.
Question 12.
Expand the following.
(i) NMT
(ii) GSM
(iii) TMDA
(iv) CDMA
Answer:
(i) NMT – Nordic Mobile Telephone
(ii) GSM – Global System for Mobile
(iii) TMDA – Time Division Multiple Access
(iv) CDMA – Code Division Multiple Access
![]()
Question 13.
What is GPRS?
Answer:
GPRS (General Packet Radio Service) is a data service which enables mobile devices to send and receive messages, picture messages, and e-mails.
Question 14.
What is Li-Fi?
Answer:
Li-Fi is a wireless technology which uses light-emitting diodes (LEDs) for data transmission.
Question 15.
What is Wi-Fi?
Answer:
Wi-Fi stands for wireless fidelity. It is wireless network technology that permits computers and alternative devices to be connected to every alternative into a local area network and to the net without wires and cables.
Question 16.
What technology use Wi-Fi?
Answer:
Wi-Fi uses radio frequencies for data transmission. And is additionally stated as wireless local area network.
![]()
Question 17.
What is RFID?
Answer:
RFID (Radio Frequency Identification) used for radio waves to read and capture information stored on a tag attached to an object.
Question 18.
What is a RFID tag?
Answer:
RFID tag has silicon Mircochip attached to a small antenna and mounted on a substrate.
Question 19.
What is a reader in RFID?
Answer:
A reader has a scanner with antennas to transmit and receive signals, used for communication.
Question 20.
What is a controller in RFID?
Answer:
A controller is the host computer with a microprocessor which receives the reader input and process the data.
![]()
Question 21.
What is Transmission Control Protocol (TCP)?
Answer:
The Transmission control protocol is accountable for guaranteeing the trustworthy transmission of data.
Question 22.
What are important and Frequent TCP/IP protocols?
Answer:
The important and Frequent TCP/IP protocols are HTTP, HTTPs and FTP.
Question 23.
What is Network Layer?
Answer:
Network Layer is the layer where data is addressed, packaged, and routed among networks.
Question 24.
What is User Datagram Protocol (UDP)?
Answer:
User Datagram protocol provides connectionless, unreliable, one-to-one (or) one-to-many delivery.
![]()
Question 25.
What is DNS?
Answer:
DNS (Domain Name System) refer to- other host computers by using names rather than numbers.
Question 26.
What is a MAC Addresses?
Answer:
MAC (Medium Access Control) address is a hardware identification number that uniquely identifies each device on a network.
Question 27.
Write the broad types of Networking protocols.
Answer:
The bread types of Networking protocols are network communication protocols, Network security protocols and Network management protocols.
(i) Network communication protocols is that the basic data communication protocols which specific as HTTP and TCP/IP.
(ii) Network security protocols is that which implement security over network communications and include HTTP, SFTP and SSL.
(iii) Network management protocols will provide network governance and maintenance and include ICMP and SNMP.
![]()
Question 28.
List out generations of mobile networks.
Answer:
- First generation (1G) – 1981 – NMT launch
- Second generation (2G) – 1991 – GSM launch
- Third generation (3G) – 2003 – UK 3G launch
- Second to third generation bridge (2.5) – 2000 – GPRS launch
- Fourth generation (4G) – 2007
- Fifth generation (5G) – 2019 +
Question 29.
Write short notes on RFID.
Answer:
- RFID – Radio Frequency Identification
- RFID uses RF wireless technology to identify.
- RFID used for radio waves to reaad and capture information stored on a tag attached to an object.
- Tag can be read from several feet away and does not need to be in direct- line-of-sight of the reader to be tracked.
- RFID has been made up of two parts a reader and a tag or a label.
- RFID tags are installed with a transmitter and receiver.
![]()
Question 30.
Write short notes on RFID component.
Answer:
- RFID component on the tags has two parts, they are microchip and the Antenna.
- A microchip which stores nad processes the information.
- The antenna to receive and transmit a signal
- The tag replies the information from its memory bank.
- The reader will transmit to read the result to RFID computer program.
Question 31.
Write the Frequent TCP/IP protocols.
Answer:
The Frequent TCP/IP protocols are HTTP, HTTPs, FTP.
Frequent TCP/IP protocols:
(i) HTTP (Hyper Text Transfer Protocol) is used between a web client and web server and it guarantees non-secure data transmissions.
(ii) HTTPS (Hyper Text Transfer Protocol Secure) is used between a web client and a web server ensures secure data transmissions.
(iii) FTP (File Transfer Protocol) is used between computers for sending and receiving file.
![]()
Question 32.
What do you know about domain names and TCP/IP addresses?
Answer:
- TCP/IP is a set of protocols which governs communications among all computers on the Internet.
- The address for any website is not as easy as to remember, domain name are used instead.
For example, 216.58.216.164 is one of the IP address for google and google.com is the domain name.
Question 33.
Explain about Network Interface layer.
Answer:
- Network interface layer is the bottom most level layer.
- It is comparable to that of the open system interconnection physical and data link layers.
- Different TCP/IP protocols are being used at this layer, Ethernet and – Token Ring for local area networks and protocols such as X.25 , Frame Relay, and ATM for Wide Area Networks.
- It is assumed to be an unreliable layer.
Question 34.
Explain the important internet protocols that operate at the network layer.
Answer:
The important internet protocols that operate at the Network layer are.
- Internet protocol (IP): Routable protocol which uses IP addresses to deliver packets.
- It is an unreliable protocol, does not guarantee delivery of information.
- ARP (Address Resolution Protocol) resolves IP addresses to MAC (Medium Access Control) addresses.
- ICMP (Internet Control Message Protocol) used by network devices to send error messages and operational information.
- IGMP (Internet Group Management Protocol) is a communication protocol used by hosts and routers to send multicast messages to multiple IP addresses at once.
![]()
Question 35.
Explain the Transport Layer.
Answer:
The sessions are recognised and data packets are swapped between hosts in this layer.
The two main protocols established at this layer are
- TCP (Transmission Control Protocol) provides reliable connection oriented transmission between two hosts. It ensures delivery of packets between the hosts.
- UDP (User Datagram Protocol) provides connectionsless, unreliable, one-to-one or one-to-many delivery.
Question 36.
Explain the most popular Application layer protocols.
Answer:
The most popular application layer protocols are
- HTTP (Hyper Text Transfer Protocol) is core protocol of the World Wide Web.
- FTP (File Transfer Protocol) is that enables a client to send and receive complete files from a server.
- Telnet is connect to another computer on the internet. ‘
- SMTP (Simple Mail Transfer Protocol) is provide e-mail services.
- DNS (Domain Name System) is refer to other host computers by using names rather than numbers.
![]()
Question 37.
Expand the following.
(i) EDGE
(ii) LED
(iii) Li-Fi
(iv) Wi-Fi
(v) UMTS
(vi) MPLS
Answer:
(i) EDGE – Enhanced Data rates for Global Evolution
(ii) LED – Light Emitting Diode
(iii) Li-Fi – Light Fidelity
(iv) Wi-Fi – Wireless Fidelity
(v) UMTS – Universal Mobile Telecommunication Systems
(vi) MPLS – Multiprotocol Label Switching.
Question 38.
List out the Application of Internet.
Answer:
- Download programs and files
- Social media
- E-Banking
- Audio and video conferencing
- E – Commerce
- File sharing
- E – Governance
- Information browsing
- Search the web addresses for access through search engine.
- Chatting and etc.,
![]()
Question 39.
List out the Applications of Intranet.
Answer:
- Sharing of company policies/rules and regulations.
- Access employee database.
- Distribution of Circulars/office orders. .
- Access product and customer data.
- Sharing of information of common interest.
- Launching of personal/departmental home pages.
- Submission of reports.
- Corporate telephone directories.
Question 40.
List out the Applications of Extranet.
Answer:
- Customer communications
- Online education/training
- Account status enquiry
- Inventory enquiry
- Online discussion
- Supply-chain management
- Order status enquiry
- Warranty registration
- Claims
- Distributor promotions.
![]()
Question 41.
Explain the generations of mobile Networks.
Answer:
(i) First Generation (1G) – 1981 – NMT Launch:
During the initial periods the mobile systems were based on analog transmission. Here NMT (Nordic Mobile Telephone) communication is used, It very poor voice quality, and they used unsure and unencrypted transmission, which leads to the spoofing of its identifies.
(ii) Second Generation (2G) – 1991 – GSM launch:
GSM (Global System Mobile communication) was most popular standard which is used second generation.
GSM mobile system grown digital transmission using SIM. SIM stands for subscriber identity module technoloty to authenticate a user for identification and billing purposes, and to encrypt the data to prevent listen without permission.
(iii) Third Generation (3G) – 2003 – 3G Launch:
In this generation of . mobile systems merges different mobile technology standards, and uses higher frequency bands for transmission and code division mutiple access to delivery data rates. MMS, Voice, Video and data are supported in this generation.
(iv) Fourth Generation (4G) – 2007:
4G was based on an adhoc networking model where there was no need for a fixed infrastructure operation. ADHOC networking requires global mobility feature and connectivity to a global IPV6 network to support an IP address for each mobile device.
(v) Fifth Generation (5G) – 2019+:
5G targets to performance the high data rate, reduced latency, energy saving, cost reduction, higher system, capacity and massive device connectivity.
5G new radio can access at lower frequencies from 600 MHz to 6 GHz.
![]()
Question 42.
Explain working of passive and Active RFID system.
Answer:
(i) A passive RFID system using induction coupling method.
The RFID tag gets power from the reader through the inductive coupling method.
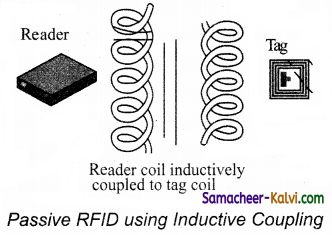
(ii) A passive RFID system using EM wave propagation method:
The reader antenna transmits the electromagnetic waves that are received by the antenna.
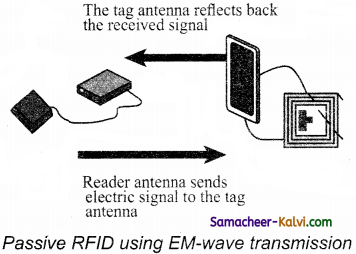
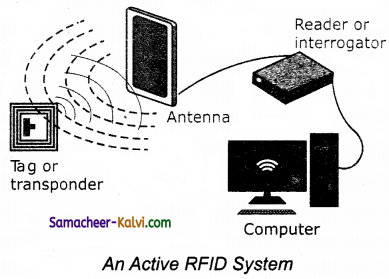
(iii) Working of Active RFID system:
The reader sends signal to the tag using an antenna.
![]()
Question 43.
Expand of the following.
(i) IoT
(ii) ATM
(iii) WLANS
(iv) OSI
(v) SMTP
(vi) ICMP
(vii) IGMP
(viii) ARP
(ix) UDP
(x) ITU
Answer:
(i) IoT – Internet of Things
(ii) ATM – Asynchronous Transfer Mode/Automatic Teller Machine (in) WLANS – Wireless Local Area Network System
(iv) OSI – Open System Interconnection
(v) SMTP – Simple Mail Transfer Protocol
(vi) ICMP – Internet control Message Protocol
(vii) IGMP – Internet Group Management Protocol
(viii) ARP – Address Resolution Protocol
(ix) UDP – User Datagram Protocol
(x) ITU – International Telecommunication Union.
![]()
Question 44.
Explain all other network protocols other that TCP/IP and OSI model.
Answer:
Except TCP/IP and OSI are called other network protocols.
(i) HTTP (Hyper Text Transfer Protocol):
A protocol used between a web client and a Webserver protects non-secure data transmissions.
(ii) HTTPS (Hyper Text Transfer Protocol Secure):
A protocol used between a web client and a Webserver permits secure data transmissions.
(iii) FTP (File Transfer Protocol):
Used between computers for sending and receiving data.
(iv) IP(Internet Protocol):
It routable Protocol which uses IP addresses to deliver packets.
(v) ARP (Address Resolution Protocol):
Resolves IP addresses to MAC (Medium Access Control) Addresses.
(vi) ICMP (Internet Control Message Protocol):
Used by network devices to send error messages and operational information.
(vii) SMTP (Simple Mail Transfer Protocol):
Provides e-mail services.
![]()
Question 45.
Define Intranet.
Answer:
Intranet is a private network within an enterprise to share company data and computing resources between the employees. It may consists of many interlinked local area networks.
Question 46.
What is the uses of mobile networks?
Answer:
- Mobile networking assign to the technology that can support data/voice, network connectivity using via radio transmission solution, wireless.
- Mobile networks are being used in diverse areas such as travel, education, stock trading, military, package delivery, disaster recovery, and medical emergencycare etc.,
Question 47.
List out the benefits of WiFi.
Answer:
- It povides mobility.
- It provides connection to Internet.
- Flexibility of LAN
- Ensures connectivity
- It allows places that are remote to benefit from connectivity.
- Low cost, high benefits.
![]()
Question 48.
How many types of RFID system available and what are they?
Answer:
Two types of RFID tags were active RFID system and passive RFID systems.
(i) Active RFID system:
The tag has its own power source. The systems used for larger distance and to track value goods like vehicles.
(ii) Passive RFID system:
The tag gets power through power from a reader antenna to the tag antenna. They are used or shorter range transmission.
Question 49.
Expand HTTP, HTTPS, FTP.
Answer:
HTTP – Hyper Text Transfer Protocol ,
HTTPS – Hyper Text Transfer Protocol Secure
FTP – File Transfer Protocol
Question 50.
Complete Internet, Intranet and Extranet.
Answer:
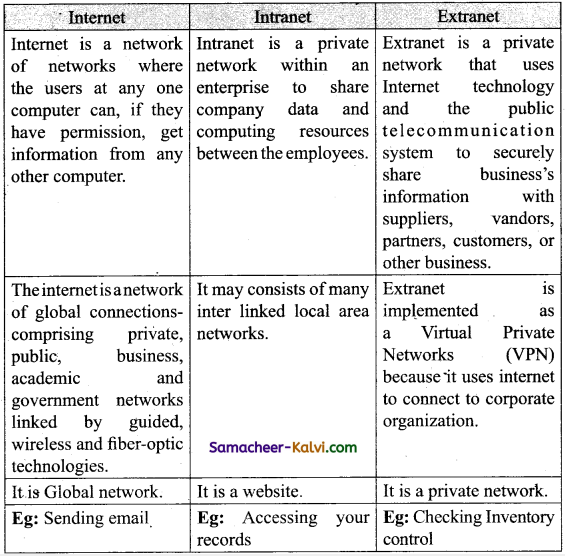
![]()
Question 51.
List out the components of a RFID system.
Answer:
The components of a RFID system follows.
(i) A RFID tag:
It has silicon microchip attached to a small antenna and mounted on a substrate.
(ii) A Reader:
It has a scanner with antenna to transmit and receive signals, used for communication.
(iii) A Controller:
It is the host computer with a microprocessor which receives the reader input and process the data.
Question 52.
Write short notes on HTTP, HTTPS, FTP.
Answer:
HTTP (Hyper Text Transfer Protocol):
It used between a web client and web server protects non-secure data transmission. The core protocol of the World Wide Web.
HTTPS (Hyper Text Transfer Protocol Secure):
It used between a web client and a web server permits secure data transmissions.
FTP (File Transfer Protocol):
It used between computers for sending and receiving data. Enables a client to send and receive complete files from a server.
![]()
Question 53.
What are the layers available in TCP/IP?
Answer:
There are four layers available in TCP/IP Protocol. They are
- Network Access Layer – Concerned with building packets.
- Internet Layer – Describes how packets are to be delivered.
- Transport Layer – Ensure the proper tmasmission of data.
- Application Layer – Application network processes. These processes include FTP, HTTP, and SMTP.
Question 54.
Expand ARP, ICMP, SMTP and DNS.
Answer:
ARP – Address Resolution Protocol
ICMP – Internet Control Message Protocol
SMTP – Simple Mail Transfer Protocol
DNS – Domain Name System
![]()
Question 55.
Explain about Internet, Intranet and Extranet.
Answer:
INTERNET:
(i) The Internet, “the Net” is a world wide system of computer networks.
(ii) A network of networks where the users at any one computer can, if they have permission, get information from any other computer.
(iii) The internet is a network of global connections – Comprising private, public, business academic and government networks – linked by guided, wireless and fibre-optic technologies.
(iv) It was perceived by the advanced research projects agency (ARPA) of the US government in 1969 and was first recognized as the ARPANET.
INTRANET:
(i) Intranet is a private network within an enterprise to share company data and computing resources between the employees.
(ii) It may consist of many interlinked local area networks.
(iii) It includes connections through one or more gateway computers to outside internet.
EXTRANET:
Extranet is a private network that uses Internet technology and the public Telecommunication system to securely share business’s information with suppliers, vendors, partners, customers, or other business.
![]()
Question 56.
Discuss about OSI model with its layers.
Answer:
OSI (Open System Interconnection) model was found in the year 1934, general framework that enables network protocols along with software and systems to be developed based on general set of guidelines. It describes the standards for the inter-computer communication.
OSI Layers:
(i) Physical Layer:
This is the Is* layer, it defines the electrical and physical specifications for devices.
(ii) Data Link Layer:
It is the 2nd layer and it guarantees that the data transmitted are free of errors. This layer has simple protocols like “802.3 for Ethernet” and “802.11 for Wi-Fi”.
(iii) Network layer:
It is the 3rd layer determining the path of the data packets.
At this layer, routing of data packets is found using IP Addressing.
(iv) Transport Layer:
It is the 4th layer that guarantees the transportation/ sending of data is successful. It includes the error checking operation.
(v) Session Layer:
It is the 5th layer, identifies the established system session between different network entities. It controls dialogues between computers.
(vi) Presentation on Layer:
It is the 6th layer that does the translation of data to the next layer. Encryption and decryption protocols occur in this layer.
(vii) Application Layer:
It is the 7th layer, which acts as the user interface platform comprising of software within the system.
![]()
Question 57.
Difference between TCP/IP and OSI model.
Answer:
| TCP/IP Model |
OSI Model |
| TCP/IP is standard protocol used for every network including internet. | OSI is not a protocol but a reference model used for understanding and designing the system architecture. |
| TCP/IP is a four layered model. | OSI has seven layered model. |
| TCP/IP is used for establishing a connection and communicating through the network. | OSI is a conceptual model which is not practically used for communication. |
| TCP/IP protocol tells how information should be packaged, sent, and received, as well as how to get to its destination. | OSI model that enables network protocols along with software and systems to be developed based on general set of guidelines. |
| TCP/IP is a combination of two protocols, transmission control protocol (TCP) and internet protcol (IP). | It describes the standards for the inter – computer communication. |
| ProtocoTdependent standard. | Protocol independent standard. |
Question 58.
Explain about the development, merits and demerits in Mobile networks.
Answer:
Merits:
- Mobile Network provides voice/data services even while roaming.
- It is used in areas where cables cannot be laid out due to its wireless nature.
- It is easy to maintain and to upgrade the equipments.
- The mobile is connected immediately with mobile network.
- The quality and flexibility of services that offer the customers.
- Greater access to modem apps and services and improved networking capabilities.
Demerits:
- Mobile Network offers less data rate compare to wired networks.
Eg: Fibre optics. - The wireless communication is influenced by climatic conditions and interference from other wireless devices.
- The installation of antennas for mobile network require space, foundation tower, time and effort.
- There are different wireless standards used in mobile networks such as GSM, CDMA, LTE etc.,
- Work place distractions as the range of technologies and devices increases.
- Increased IT security needs-portable devices are vulnerable to security risks.
![]()
• List out some web address with http and https.
Question 59.
Find some of the http web addresses.
Answer:
- http: // www.worldbank.org
- http: // www.ox.ac.uk
- http: // www.ucla.edu
- http: // www.mit.edu
- http: // www.fortune.com
Question 60.
Give some example for https.
Answer:
- https: // www.time.com
- https: // www.dailymail.co.uk
- https: // www.un.org
- https: // www.redcross.org
- https: // www.hilton.com
Question 61.
Can you know difference between http and https.
Answer:
| http |
https |
| URL begins with “http://” | URL starts with “https://” |
| User port number 80 for comimunication | User port number 443 for communication |
| It is considered to be unsecured | It is considered to be secure |
| Encryption is absent | Encryption is present |
| ft does not require any certificates | It needs SSL certifications |
![]()
Choose the correct answer:
Question 1.
Which is the principal of the cpmmunication protocol and working with boostup the internet?
(a) Internet Protocol (IP)
(b) Simple Mail Transfer Protocol (SMTP)
(c) File Transfer Protocol (FTP)
(d) User Datagram Protocol (UDP)
Answer:
(a) Internet Protocol (IP)
Question 2.
Which is a network of global connections?
(a) Extranet
(b) Intranet
(c) Internet
(d) Networks
Answer:
(c) Internet
Question 3.
Which is a private network within an enterprise to share company data?
(a) Extranet
(b) Intranet
(c) Internet
(d) Networks
Answer:
(b) Intranet
![]()
Question 4.
Which is refers to the.digital interconnection of everyday objects with the internet?
(a) Extranet
(b) Intranet
(c) Networks
(d) Internet of Things (IoT)
Answer:
(d) Internet of Things (IoT)
Question 5.
Which type is used you to send e-mail to your friend?
(a) Extranet
(b) Intranet
(c) Internet
(d) IoT
Answer:
(c) Internet
Question 6.
Which type is used to accessing your record in the employee personnel file?
(a) Extranet
(b) Intranet
(c) Internet
(d) IoT
Answer:
(b) Intranet
![]()
Question 7.
Which type is used for checking availability of inventory from an outside ‘ supplier?
(a) Extranet
(b) Intranet
(c) Internet
(d) IoT
Answer:
(a) Extranet
Question 8.
Which network is madeup of large number of signals areas called cells?
(a) Mobile Network
(b) Local Area Network
(c) Wide Area Network
(d) Metropolitan Network
Answer:
(a) Mobile Network
Question 9.
Which Transmission launched in First generation of mobiles?
(a) NMT Launch
(b) GSM Launch
(c) GPRS Launch
(d) 2G Launch
Answer:
(a) NMT Launch
![]()
Question 10.
Which Transmission launched in second generation on mobiles?
(a) NMT Launch
(b) GSM Launch
(c) GPRS Launch
(d) 2G Launch
Answer:
(b) GSM Launch
Question 11.
SIM stands for:
(a) Standard Identified Mobile
(c) Subscriber Identified Mobile
(b) Standard Individual Mobile
(d) Subscriber Identity Module
Answer:
(d) Subscriber Identity Module
Question 12.
Which mobile systems grown digital transmission using SIM?
(a) NMT
(b) GPRS
(c) GSM
(d) 2G
Answer:
(c) GSM
![]()
Question 13.
GPRS stands for:
(a) General Packet Radio Service
(b) Government Program Radio Service
(c) General Program Radio Service
(d) Government Program Rare Service
Answer:
(a) General Packet Radio Service
Question 14.
Which data service is to send and receive picture message and e-mails in mobiles?
(a) GSM
(b) NMT
(c) GPRS
(d) 2G
Answer:
(c) GPRS
Question 15.
Which is a wireless technology uses light-emitting diodes (LEDs) for data transmission?
(a) Li-Fi
(b) Wi-Fi
(c) GSM
(d) GPRS
Answer:
(a) Li-Fi
![]()
Question 16.
Which is used radio frequencies for data transmission?
(a) Li-Fi
(b) Wi-Fi
(c) GSM
(d) GPRS
Answer:
(b) Wi-Fi
Question 17.
Li-Fi short form:
(a) Light Fidelity
(b) Light Fiction
(c) Light Finite
(d) Limit Fidelity
Answer:
(a) Light Fidelity
Question 18.
Which one of the following is not a application of Internet?
(a) Social media
(b) E-Mail
(c) E-banking
(d) claims
Answer:
(d) claims
![]()
Question 19.
The term Li-Fi was first used by:
(a) Harald Haas
(b) Steven H.Walker
(c) D. Eisenhower
(d) John Murphy
Answer:
(a) Harald Haas
Question 20.
WCDMA stands for:
(a) Wide computer Division Multiple Access
(b) Wideband Code Division Multiple Access
(c) Wideband Compile Direct Multiple Access
(d) Wide Connect Direct Multiple Access
Answer:
(b) Wideband Code Division Multiple Access
Question 21.
Which generation is an adhoc networking model where there was no need for a fixed infrastructure operation?
(a) 2G
(b) 3G
(c) 4G
(d) 5G
Answer:
(c) 4G
![]()
Question 22.
Which is used for radio waves to read and capture information stored on a tag attached to an object?
(a) GPRS
(b) EDGE
(c) UMTS
(d) RFID
Answer:
(d) RFID
Question 23.
How many parts types are madeup of RFID?
(a) 2
(b) 3
(b) 4
(d) 5
Answer:
(a) 2
Question 24.
How many component are there in RFID?
(a) 2
(b) 3
(c) 4
(d) 5
Answer:
(a) 2
![]()
Question 25.
Which year was found open system interconnection (OSI)?
(a) 1952
(b) 1950
(c) 1932
(d) 1934
Answer:
(d) 1934
Question 26.
Which OSI layer defines the electrical and physical specifications for devices?
(a) Physical
(b) Data Link
(c) Network
(d) Transport
Answer:
(a) Physical
Question 27.
Which OSI layer is guarantees that transmitted are free of error?
(a) Physical
(b) Data Link
(c) Network
(d) Transport
Answer:
(b) Data Link
![]()
Question 28.
Which OSI layer is determining path and route of the data packets?
(a) Physical
(b) Data link
(c) Network
(d) Transport
Answer:
(c) Network
Question 29.
Which OSI Layer that guarantees the sending of data is successful?
(a) Physical
(b) Data Link
(c) Network
(d) Transport
Answer:
(d) Transport
Question 30.
Which OSI layer that controls dialogues between computers?
(a) Transport
(b) Session
(c) Presentation
(d) Application
Answer:
(b) Session
![]()
Question 31.
Which OSI Layer that occurs Encryption and decryption protocols?
(a) Transport
(b) Session
(c) Presentation
(d) Application
Answer:
(c) Presentation
Question 32.
Which OSI layer act as the user interface perform comprising of software within the system?
(a) Transport
(b) Session
(c) Presentation
(d) Application
Answer:
(d) Application
Question 33.
Which is a set of protocols that governs communications among all computers on the Internet? .
(a) HTTP
(b) TCP/IP
(c) HTTPS
(d) FTP
Answer:
(b) TCP/IP
![]()
Question 34.
Which protocol specifies the logistics of the packets that are sent out over networks?
(a) IP
(b) HTTP
(c) HTTPS
(d) FTP
Answer:
(a) IP
Question 35.
Which protocol is accountable for guaranteeing the trustworthy transmission of data?
(a) TCP
(b) IP
(c) FTP
(d) HTTP
Answer:
(a) TCP
Question 36.
Which protocol is used between a web client and web server and it guarantees non-secure data transmission?
(a) HTTP
(b) HTTPS
(c) FTP
(d) TCP
Answer:
(a) HTTP
![]()
Question 37.
Which protocol is used between a web client and a web server ensures secure data transmission?
(a) HTTP
(b) HTTPS
(c) FTP
(d) TCP
Answer:
(b) HTTPS
Question 38.
Which protocol is used between computers for sending and receiving file?
(a) HTTP
(b) HTTPS
(c) FTP
(d) TCP
Answer:
(c) FTP
Question 39.
Which is the bottom most level layer?
(a) Network Interface
(b) Physical
(c) Transport
(d) Application
Answer:
(a) Network Interface
![]()
Question 40.
Which layer is used where data is addressed, packaged40. Which layer is used where data is addressed, packaged, and routed among networks?
(a) Network Interface
(b) Network
(c) Transport
(d) Physical
Answer:
(b) Network
Question 41.
Which is address that gives hardware identification number?
(a) MAC
(b) ICMP
(c) IGMP
(d) SMTP
Answer:
(a) MAC
Question 42.
Which Protocol used by network devices to send error messages and operational information?
(a) MAC
(b) ICMP
(c) IGMP
(d) SMTP
Answer:
(b) ICMP
![]()
Question 43.
Which Protocol used by hosts and routers to send multicast messages to multiple IP addresses at once?
(a) MAC
(b) ICMP
(c) IGMP
(d) SMTP
Answer:
(c) IGMP
Question 44.
Which protocol provides connectionless, unreliable, one-to-one or one-to- . many delivery?
(a) IP
(b) TCP
(c) FTP
(d) UDP
Answer:
(d) UDP
Question 45.
Which is connect to another computer on the Internet?
(a) DNS
(b) SMTP
(c) Telnet
(d) FTP
Answer:
(c) Telnet
![]()
Question 46.
Which year was launched first generations of mobile networks?
(a) 1981
(b) 1989
(c) 1991
(d) 2000
Answer:
(c) 1991
Question 47.
Which has silicon microship attached to a small antenna in RFID system?
(a) RFID tag
(b) A reader
(c) A controller
(d) None of these
Answer:
(a) RFID tag
Question 48.
Which has a scanner with antennas to transmit and receive signals in RFID system?
(a) RFID tag
(b) A reader
(c) A controller
(d) None of these
Answer:
(b) A reader
![]()
Question 49.
Which is the host computer with a microprocessor that receives the reader input and process the data?
(a) RFID tag
(b) A reader
(c) A controller
(d) None of these
Answer:
(c) A controller
Question 50.
Match the following.
| (A) Internet | (i) Enterprise |
| (B) Intranet | (ii) Global |
| (C) Extranet | (iii) Objects |
| (D) Internet of things | (iv) Telecommunication |
(a) (A) – (iii); (B) – (ii); (C) – (iv); (D) – (i)
(b) (A) – (iii); (B) – (iv); (C) – (i); (D) – (ii)
(c) (A) – (ii); (B) – (i); (C) – (iv); (D) – (iii)
(d) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
Answer:
(c) (A) – (ii); (B) – (i); (C) – (iv); (D) – (iii)
Question 51.
Match the following.
| (A) 1G | (i) Adhoc |
| (B) 2G | (ii) MMS |
| (C) 3G | iii) NMT |
| (D) 4G | (iv) GSM |
(a) (A) – (iii); (B) – (iv); (C) – (ii); (D) – (i)
(b) (A) – (iii); (B) – (ii); (C) – (i); (D) – (iv)
(c) (A) – (ii); (B) – (i); (C) – (iv); (D) – (iii)
(d) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
Answer:
(a) (A) – (iii); (B) – (iv); (C) – (ii); (D) – (i)
![]()
Question 52.
Match the following.
| (A) Physical Layer | (i) Sending data |
| (B) Data Link Layer | (ii) Path of data |
| (C) Network Layer | (iii) Free errors |
| (D) Transport Layer | (iv) Electrical |
(a) (A) – (iii); (B) – (ii); (C) – (iv); (D) – (i)
(b) (A) – (iii); (B) – (iv); (C) – (i); (D) – (ii)
(c) (A) – (iv); (B) – (iii); (C) – (ii); (D) – (i)
(d) (A) – (iv); (B) – (ii); (C) – (i); (D) -( iii)
Answer:
(c) (A) – (iv); (B) – (iii); (C) – (ii); (D) – (i)
Question 53.
Match the following.
| (A) HTTP | (i) Secure data |
| (B) HTTPs | (ii) Non secure data |
| (C)FTP | (iii) Logistics of packets |
| (D) IP | (iv) File transaction |
(a) (A) – (ii); (B) – (iii); (C) – (iv); (D) – (i)
(b) (A) – (ii); (B) – (i); (C) – (iv); (D) – (iii)
(c) (A) – (iii); (B) – (iv); (C) – (i); (D) – (ii)
(d) (A) – (iii); (B) – (i); (C) – (ii); (D) – (iv)
Answer:
(b) (A) – (ii); (B) – (i); (C) – (iv); (D) – (iii)
Question 54.
Match the following.
| (A) Application Layer | (i) TCP |
| (B) Transport Layer | (ii) Ethernet |
| (C) Network Layer | (iii) HTTP |
| (D) Network Interface Layer | (iv) IP |
(a) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
(b) (A) – (iii); (B) – (ii); (C) – (iv); (D) – (i)
(c) (A) – (iv); (B) – (iii); (C) – (i); (D) – (ii)
(d) (A) – (iv); (B) – (i); (C) – (ii); (D) – (iii)
Answer:
(a) (A) – (iii); (B) – (i); (C) – (iv); (D) – (ii)
![]()
Question 55.
Choose the incorrect pair.
(a) Internet – AREA
(b) Intranet – Private
(c) Extranet – Global
(d) IoT – Object
Answer:
(c) Extranet – Global
Question 56.
Choose the incorrect pair.
(a) 1G – 1981
(b) 2G – 1994
(c) 3G – 2003
(d) 4G – 2010
Answer:
(d) 4G – 2010
Question 57.
Choose the incorrect pair.
(a) Application layer – MPEG
(b) Presentation layer – TSL
(c) Session layer – SAP
(d) Transport layer – TCP
Answer:
(a) Application layer – MPEG
![]()
Question 58.
Choose the correct pair.
(a) HTTP – Secure data
(b) HTTPs – Non-secure data
(c) DP – logistics
(d) TCP – Data processing
Answer:
(c) DP – logistics
Question 59.
Choose the correct pair.
(a) SMTP – e-mail service
(b) DNS – using numbers
(c) ICMP – hardware Identification
(d) MAC – error message
Answer:
(a) SMTP – e-mail service
Question 60.
Choose the incorrect statement.
(a) The main function is to allows internet working and boostup the internet.
(b) Internet protocol (IP) will deliver packets from the source host.
(c) Network protocols have to do ene-to-end process of secure on time and manage data or network communication.
(d) Network communication protocols is that the Basic data communication protocols which specific as SMTP and SNMP.
Answer:
(d) Network communication protocols is that the Basic data communication protocols which specific as SMTP and SNMP.
![]()
Question 61.
Choose the incorrect statement.
(a) The internet “The Net” is a world wide system of computer networks.
(b) The internet is a network of global conections
(c) Intranet is a private network that uses internet technology and the public telecommunication.
(d) Extranet is a private network that to securly share business’s information.
Answer:
(c) Intranet is a private network that uses internet technology and the public telecommunication.
Question 62.
Choose the incorrect statement.
(a) Internet of things (IoT) refers to the digital interconnection of everyday objects with the Internet.
(b) The ‘Thing’ in IoT refers to an objects that have been assigned an IP address.
(c) Wi-Fi uses microwaves for data transmission.
(d) Li-Fi is a wireless technology which uses light-emitting diodes for data transmission.
Answer:
(c) Wi-Fi uses microwaves for data transmission.
Question 63.
Choose the incorrect statement.
(a) Wi-Fi stands for wireless Fidelity.
(b) 5G target to performance the high data rate, reduced latency, energy saving, cost reduction, higher system, capacity, and massive device connectivity.
(c) RFID – Rare Frequency Identified.
(d) Wi-Fi is additionally stated as wireless local area network that stands for wireless local area network.
Answer:
(c) RFID – Rare Frequency Identified.
![]()
Question 64.
Choose the incorrect statement.
(a) RFID component on the tags has four parts.
(b) A microship which stores and process the information, and the antenna to receive and transmit a signal.
(c) A RFID tag has silicon microchip attached to a small antenna.
(d) A reader has a scanner with antennas to transmit and receive signals.
Answer:
(a) RFID component on the tags has four parts.
Question 65.
Choose the correct statement.
(a) Open System Interconnection (OSI) model was found in the year 1948.
(b) The physical layer defines that the data transmitted are free of errors.
(c) Data link layer defines that electrical specifications for devices.
(d) Network layer is determining the path of the data packets.
Answer:
(d) Network layer is determining the path of the data packets.
Question 66.
Choose the correct statement.
(a) Session layer that guarantees the sending of data is successful.
(b) Transport layer that controls dialogues between computers.
(c) Presentation layer does encryption and decryption protocols occurs.
(d) Application layer does the translation of data to the next layer.
Answer:
(c) Presentation layer does encryption and decryption protocols occurs.
![]()
Question 67.
Choose the correct statement.
(a) TCP/IP is a combination of two protocols.
(b) Internet Protocol (IP) is accountable for guaranteeing the trust worthy transmission of data.
(c) The Transmission Control Protocol (TCP) specifies logistics of the packets that are sent out over networks.
(d) FTP is used between a web client and a web server and it guarantees non- secure data transmissions.
Answer:
(a) TCP/IP is a combination of two protocols.
Question 68.
Choose the correct statement.
(a) Network protocols otherthan OSI and TCP/IP were simply known as other network protocols.
(b) HTTPS positions for Hypertext transmitted protocol service.
(c) HTTP in address bar mainly deals with scientific applications.
(d) TCP/IP has six layers.
Answer:
(a) Network protocols otherthan OSI and TCP/IP were simply known as other network protocols.
Question 69.
Choose the correct statement.
(a) IGMP is a network devices to send error messages and operational information.
(b) Network Interface layer is the bottommost level layer.
(c) Network layer is a communication used by hosts and routers to send multicast messages.
(d) DNS (Domain Name System) that refer to other host computers by using numbers rather than names.
Answer:
(b) Network Interface layer is the bottommost level layer.
![]()
Question 70.
Assertion (A):
The Internet “the Net”, is a world wide system of computer networks.
Reason (R):
The internet is a network of global connections linked by guided, wireless and Fiberoptic technologies.
(a) Both A and R are true, and R is the correct explanation for A.
(b) Both A and R are true, but R is not the correct explanation for A.
(c) A is true, But R is false.
(d) A is false, But R is true.
Answer:
(a) Both A and R are true, and R is the correct explanation for A.
Question 71.
Assertion (A):
A mobile network or cellular network as it is made up a large number of signals area called cells.
Reason (R):
Cells will often be smaller in size in large towns, as the number of users in the area is more.
(a) Both A and R are true, and R is the correct explanation for A.
(b) Both A and R are true, but R is not the correct explanation for A.
(c) A is true, But R is false.
(d) A is false, But R is true.
Answer:
(b) Both A and R are true, but R is not the correct explanation for A.
Question 72.
Assertion (A):
GPRS is a data service which enables mobile devices to send and receive picture messages and e-mails.
Reason (R):
GPRS was introduced between 2G and 3G for period of mobile networking development.
(a) Both A and R are true, and R is the correct explanation for A.
(b) Both A and R are true, but R is not the correct explanation for A.
(c) A is true, But R is false.
(d) A is false, But R is true.
Answer:
(c) A is true, But R is false.
![]()
Question 73.
Assertion (A):
Wi-Fi stands for Wired Fidelity.
Reason (R):
Wi-Fi provides connection to Internet.
(a) Both A and R are true, and R is the correct explanation for A.
(b) Both A and R are true, but R is not the correct explanation for A.
(c) A is true, But R is false.
(d) A is false, But R is true.
Answer:
(d) A is false, But R is true.
Question 74.
Assertion (A):
RFID component on the tag a microchip which receive and • transmit a signal.
Reason (R):
RFID component on Antenna which stores and process the information.
(a) Both A and R are true.
(b) Both A and R are false.
(c) A is true, But R is false.
(d) A is false, But R is true.
Answer:
(b) Both A and R are false.
Question 75.
Pick the odd one out.
(a) Internet
(b) APRANet
(c) Intranet
(d) Extranet
Answer:
(b) APRANet
![]()
Question 76.
Pick the odd one out.
(a) NMT
(b) GSM
(c) GPRS
(d) HTTP
Answer:
(d) HTTP
Question 77.
Pick the odd one out.
(a) Li-Fi
(b) Wi-Fi
(c) WiMAX
(d) DNS
Answer:
(d) DNS
Question 78.
The ………….., “the Net,” is a worldwide system of computer networks.
(a) internet
(b) mobile
(c) communication
(d) protocol
Answer:
(a) internet
![]()
Question 79.
Which one of the following will be easy the way to uses Internet technology and the public telecommunication system to securely share business’s information with suppliers, vendors, partners and customers?
(a) Extranet
(b) Intranet
(c) Arpanet
(d) Arcnet
Answer:
(a) Extranet
Question 80.
Match the following and choose the correct answer:
(i) HTTP -The core protocol of the World Wide Web.
(ii) FTP- enables a client to send and receive complete files from a server.
(iii) SMTP – Provide e-mail services.
(iv) DNS- Refer to other host computers by using names rather than numbers.
(a) (i), (ii), (iii), (iv)
(b) (ii), (iii), (iv), (i)
(c) (iii), (iv), (i), (ii)
(d) (iv), (iii), (ii), (i)
Answer:
(a) (i), (ii), (iii), (iv)
Question 81.
Communication over ……………….. is be made up of voice, data, images and text messages.
(a) social media
(b) mobile network
(c) whatsapp
(d) software
Answer:
(b) mobile network
![]()
Question 82.
Wi-Fi stands for:
(a) Wireless Fidelity
(b) Wired Fidelity
(c) Wired optic Fibre
(d) Wireless optic Fibre
Answer:
(a) Wireless Fidelity
Question 83.
A TCP/IP network with access restricted to members of an organization:
(a) LAN
(b) MAN
(c) WAN
(d) Intranet
Answer:
(d) Intranet
Question 84.
RFID stands for:
(a) Radio Free Identification
(b) Real Frequency Identity
(c) Radio Frequency Indicators
(d) Radio Frequency Identification
Answer:
(d) Radio Frequency Identification
![]()
Question 85.
It guarantees the sending of data is successful and which checks error on operation at OSI layer is:
(a) Application Layer
(b) Network Layer
(c) Transport Layer
(d) Physical Layer
Answer:
(c) Transport Layer
Question 86.
Which orie of the following will secure data on transmissions?
(a) HTTPS
(b) HTTP
(c) FTP
(d) SMTP
Answer:
(a) HTTPS
Question 87.
…………. provfdes e-mail service.
(a) DNS
(b) TCP
(c) FTP
(d) SMTP
Answer:
(d) SMTP
![]()
Question 88.
……………. refer to other host computers by using names rather than numbers.
(a) DNS
(b) TCP
(c) FTP
(d) SMTP
Answer:
(a) DNS
Question 89.
TCP/IP is a combination of two protocols:
(i) Transmission Control Protocol (TCP)
(ii) Internet Protocol (IP)
(iii) Selection Protocol (SP)
(iv) Captiai Protocol (CP)
(a) (i), (ii)
(b) (i), (iii)
(c) (iii), (iv)
(d) (ii), (iii)
Answer:
(a) (i), (ii)